|
PROJECT TO PROMOTE COMPETITION & INNOVATION
|
|
I N T H E D I G I T A L A G E
|
|
2001 K STREET, NW . SUITE 800 . WASHINGTON, DC 20006
|
January 28, 2002
Ms. Renata Hesse
Trial Attorney
Suite 1200
Antitrust Division
Department of Justice
601 D. Street, NW
Washington, D.C. 20530
| RE: |
Comments to the Proposed Final Judgment In
United States v. Microsoft Corporation, No. 98-1232
State of New York, et al v. Microsoft Corporation, No. 98-1233 |
Dear Ms. Hesse,
Enclosed please find ten (10) copies of the comments of the Project to Promote Competition and Innovation in the Digital Age ("ProComp"), submitted pursuant to the Tunney Act, 15 U.S.C. § 16, with respect to the Proposed Final Judgment in the above-captioned matters.
Please also note that this filing is accompanied by an affidavit prepared and submitted by Professor Kenneth J. Arrow, the original signed copy of which is attached hereto.
| |
Sincerely yours,
/s/
Mitchell S. Pettit
President
ProComp |
Comments to the Proposed Final Judgment In
United States v. Microsoft Corporation, No. 98-1232
State of New York, et al. v. Microsoft Corporation, No. 98-1233
Submitted By
Project to Promote Competition & Innovation
in the Digital Age ("ProComp")
Pursuant to the Tunney Act, 15 U.S.C. . 16
January 28, 2002
Kenneth W. Starr
Thomas D. Yannucci
Mark L. Kovner
Kirkland & Ellis
655 15th Street, N.W., Suite 1200
Washington, D.C., 20005
(202) 879-5000
Counsel for ProComp |
Robert H. Bork
1150 17th Street, N.W.
Washington, D.C. 20036
Counsel for ProComp |
| |
Kevin J. Arquit
Michael C. Naughton
Arman Y. Oruc
Clifford Chance Rogers & Wells LLP
200 Park Avenue
New York, N.Y. 10166
(212) 878-8000
Counsel for ProComp |
Mitchell S. Pettit, President
ProComp
2001 K Street, N.W., Suite 800
Washington, D.C. 20006
(202) 912-7140 |
| |
Glenn B. Manishin
Stephanie A. Joyce
Kelley Drye & Warren LLP
1200 19th Street, N.W., Suite 500
Washington, D.C. 20036
(202) 955-9600
Counsel for ProComp |
TABLE OF CONTENTS
This proposed decree is so ineffective that it would not have prevented Microsoft from destroying Netscape and Java, the very acts that gave rise to this lawsuit. It is so ineffective in controlling Microsoft that it might as well have been written by Microsoft itself.
The "public interest" standard of the Tunney Act, 15 U.S.C. § 16(e), is determined in this case by the unanimous legal ruling of the Court of Appeals for the District of Columbia Circuit sitting en bane. That Court held that Microsoft has maintained its monopoly in personal computer operating systems in clear violation of Section 2 of the Sherman Act. No decree that fails to cure that illegality and prevent its recurrence can conceivably serve the public interest. The Proposed Final Judgment ("PFJ" or "proposed decree") accomplishes neither of those mandatory purposes. For that reason, the proposed decree should be rejected by the District Court.
This case is entirely different from any settlement since the adoption of the Tunney Act in 1974. All other settlements were entered into prior to the conclusion of any trial, usually before any trial had even commenced. Cases holding that a Tunney Act court must accept a lesser remedy than might (or might not) be obtained after trial are utterly irrelevant. The Competitive Impact Statement's ("CIS") reliance upon such cases is misguided. United States v. Microsoft Corp., Revised Proposed Final Judgment and Competitive Impact Statement, 66 Fed. Reg. 59,452 (2001). Here, the District Court and the Court of Appeals, including a total of eight judges, have decided that in violating the Sherman Act, Microsoft's behavior is directly contrary to the public interest. The Tunney Act does not empower the District Court to enter a remedy that excuses past violations and permits future conduct of the same nature. The proposed decree does precisely that. It is no more binding on the District Court than would be a Department of Justice statement that henceforth a named company would be immune from antitrust prosecution.
In particular, the proposed settlement takes no steps to remedy Microsoft's foreclosure of middleware threats from competing Internet browsers and cross-platform Java technology, Microsoft's related efforts to illegally increase the applications barrier to entry protecting its Windows monopoly, or Microsoft's illegal commingling of browser and other middleware code with Windows. Further, the proposed settlement does not assure that future middleware competitors will have access to the necessary technical information to interoperate properly with Windows, and does not open up the critical Original Equipment Manufacturer ("OEM") distribution channel to these future competitors. Finally, the PFJ ignores the competitive threat to Microsoft's monopoly presented by server-based distributed applications, and thus fails to address Microsoft's practice of protecting its monopoly by controlling proprietary interfaces and communications protocols.
More significantly, the only suggestion in the CIS as to any basis for a very limited and deferential scope of judicial review is simply wrong. The Department insists that such a standard is "particularly" appropriate "where, as here, court's review of the decree is informed not merely by the allegations contained in the Complaint, but also by the extensive factual and legal record resulting from the district and appellate court proceedings." CIS, 66 Fed. Reg. at 59476. Exactly the opposite is the case. In routine Tunney Act cases, the law is clear that respect is to be accorded to the Department's antitrust enforcement judgments -- its "perceptions of the market structure and its view of the nature of the case" -- precisely because there is no factual or legal record before the court. United States v. Microsoft Corp., 56 F.3d 1448, 1448 (D.C. Cir. 1995) ("Microsoft l") (emphasis added). When a Sherman Act case has been litigated and affirmed on appeal, however, the district court is fully capable of assessing the proposed remedy in light of those rulings and its "familiarity with the market involved." Id. at 1461.
The closest parallel to this Court's review of the PFJ is the AT&T monopolization settlement presented by the Department and decided by this Court (Harold Greene, J.) under the Tunney Act. United States v. AT&T, 552 F. Supp. 131 (D.D.C. 1982), aff'd mere. sub nora., Maryland v. United States, 460 U.S. 1001 (1983). In the AT&Tease, Judge Greene had heard the vast majority of the evidence -- on all issues except remedy -- and more than a year earlier bad denied AT&T's motion to dismiss on the merits after the close of the government's case-in-chief. Following a wide-ranging Tunney Act process that included evidentiary hearings, third-party submissions and several days of oral argument, Judge Greene refused to approve the consent decree as proposed, even though it mandated divestiture of major components of the Bell System. He concluded that the decree was in certain respects substantively inadequate, precluded the Court from effective oversight and enforcement, and posed a risk of harming third-parties (despite the presence of complementary regulatory jurisdiction to accomplish similar goals). Judge Greene therefore insisted upon substantial modifications to the proposed decree before he would enter the settlement under the Tunney Act's public interest standard.
Recognizing the intense public concern over a possible "rubber stamp" of the settlement by the Court, Judge Greene concluded that it was his responsibility to ensure that the decree protected consumers, opened the relevant markets to effective competition in a timely manna-, and was readily enforceable. Significantly, Judge Green found that "unlike ordinary pre-trial antitrust settlements, the Court would 'be able to render sound judgments' because it 'ha[d] already heard what probably amounts to well over ninety percent of the parties' evidence both quantitatively and qualitatively, as well as all of their legal arguments." Id. at 152 (citations omitted). For this reason, Judge Greene held that "it does not follow that [the Court] must unquestionably accept a consent decree as long as it somehow, and, however inadequately, deals with the antitrust problems implicated in the lawsuit." Id.
The purpose of judicial review under the Tunney Act is to ensure that a consent decree follows "'the public interest as expressed in the antitrust laws.'" S. REP. NO. 93--298 (1973) ("SENATE REPORT") (emphasis added). Here, the Court of Appeals held specifically that "a remedies decree in an antitrust case must seek to 'unfetter a market from anticompetitive conduct,' to 'terminate the illegal monopoly, deny to the defendant the fruits of its statutory violation, and ensure that there remain no practices likely to result in monopolization in the future.'" United States v. Microsoft Corp., 253 F.3d 34, 103 (D.C. Cir. 2001) ("Microsoft III"') (quoting Ford Motor Co. v. United States, 405 U.S. 562, 577 (1972), and United States 1,. United Shoe Mach. Corp., 391 U.S. 244, 250 (1968)). The Department itself earlier emphasized to this Court on remand that "both the applicable remedial legal standard and the liability determination of the Court of Appeals are clear." Joint Status Report, United States v. Microsoft Corp., at 24 (D.D.C. filed Sept. 20, 2001). The Court of Appeals has spoken and its holding is binding on this Court as well as the litigants. Consequently, in the unique procedural posture of this case, the "public interest as expressed in the antitrust laws" is the Court of Appeals' mandate itself. SENATE REPORT, supra, at 5.
The CIS does not even cite, let alone argue, that the PFJ meets the D.C. Circuit's remedial standard, quoted above, to terminate the monopoly, deny the defendant of its ill-gotten fruits, and ensure that monopoly practices cannot arise in the future.
As that standard recognizes, there is no difference between the remedies called for when a defendant has unlawfully gained a monopoly or unlawfully maintained a monopoly. The offense of monopolization under Section 2 of the Sherman Act occurs when a finn has either "'acquired or maintained" monopoly power by anticompetitive means. United States v Grinnell Corp., 384 U.S. 563, 570-71 (1966); Microsoft III, 253 F.3d at 50. There is no legal basis to distinguish between the methods of monopolization either for liability or relief purposes, and neither DOJ nor Microsoft has cited a case making such a distinction. All arc equally unlawful and all arc equally harmful to consumers. Here, for example, even assuming that Microsoft achieved its monopoly power through legitimate business means, it has been found to have maintained such monopoly power through a series of anticompetitive conduct designed to illegally preserve its monopoly position by foreclosing rivals. But for this illegal maintenance, Microsoft's monopoly power would probably have dissipated, and competitors and consumers would have enjoyed the benefits of free and fair competition. Microsoft's internal communications demonstrate that Microsoft thought that would be the likely outcome.
For these reasons, courts apply broad relief even where a firm has been found to possess monopoly power that was legally acquired but illegally maintained. See, e.g., United Shoe, 391 U.S. at 250 (in context of a legally attained monopoly position that was illegally maintained, the Court held it has a duty to "prescribe relief which will terminate the illegal monopoly, deny to the defendant the fruits of its statutory violation, and ensure that there remain no practices likely to result in monopolization in the future"). And courts have never distinguished between illegal attainment and illegal maintenance when determining remedies for a Sherman Act Section 2 monopolization claim. See, e.g., Schine Chain Theatres, Inc. v. United States, 334 U.S. 110, 128 (1948) (holding conduct injunctions against future violations not adequate to protect public interest in monopolization cases since defendant thus maintains the full benefit of the monopoly; instead broad remedies, including divestiture, are necessary to undo the harm to the market); see also 3 PHILLIP E. AREEDA AND HERBERT HOVENCAMP, ANTITRUST LAW ¶ 653i (2002) (quoting United Shoe, 391 U.S. at 250-52, for the proposition that a "monopoly that has been created or maintained by plainly exclusionary conduct is unlawful and that it is the duty of the court to assure its 'complete extirpation.'" (emphasis added)). In short, an appropriate set of remedies to restore competition needs to be sufficient to pry open the market to competition, stop the bad acts, undo the effects of the bad acts, and preclude future alternative anticompetitive tactics.
The D.C. Circuit was well aware that this case involves monopoly maintenance -- that the achievement by Microsoft of a Windows monopoly in the first instance was not alleged to be unlawful -- but nonetheless specifically adopted the Ford/United Shoe remedy standard, including its command to "terminate" the defendant's monopoly power. That is the law of this case and the law in all Sherman Act monopolization cases.
By agreeing to the proposed settlement, the Department and the Settling States have "won a lawsuit and lost a cause." International Salt Co. v. United States, 332 U.S. 392, 401 (1947). By excluding consideration of terminating the Windows monopoly from their remedy calculations, Plaintiffs have ignored the central meaning of Section 2. They would have the Court sanction Microsoft's unlawful conduct allowing its monopoly to remain intact. The Court of Appeals' use of the traditional Ford/United Shoe standard clearly holds that that is not a proper remedy.
The CIS explains that the applications barrier to entry protecting Microsoft's monopoly was directly threatened by "two incarnations of middleware that, working together, had the potential to weaken the applications barrier severely without the assistance of any other middleware" -- Netscape and Java. CIS, 66 Fed. Reg. at 59464-65. Nonetheless, the PFJ inexplicably contains no provision addressing Internet browsers or cross-platform Java runtime technology, let alone any other provisions that erode the applications barrier to entry. Moreover, the proposed decree simply ignores a number of other significant ways in which the Court of Appeals held that Microsoft's practices violated the Sherman Act. Consequently, the PFJ does not "unfetter [the] market from anticompetitive conduct" or "ensure that there remain no practices likely to result in monopolization in the future." Microsoft III, 253 F.3d at 103.
Nothing in the settlement prohibits Microsoft from commingling code or binding its middleware to the operating system. This was a major issue in this litigation, and the Court of Appeals specifically found Microsoft's commingling of browser and operating system code to be anticompetitive. The danger is reinforced by the definition of "Windows Operating System Product" in Section VI.U, which states that what code comprises Windows "shall be determined by Microsoft in its sole discretion." PFJ, 66 Fed. Reg. at 59459. Thus, Microsoft can render the protections for middleware, meaningless by binding and commingling code and redefining the operating system to include the bound/commingled applications.
ProComp strongly disagrees with the notion that it is impossible to move the market forward to approximate where it would have been absent Microsoft's violations. The applications barrier to entry is not an immutable condition. There are remedial alternatives available to restore Internet browsers and cross-platform runtime technology to the position they would have achieved -- ubiquitous distribution without any "lock-in" to the Windows operating system m in the absence of Microsoft's violations. The open source Internet Explorer ("IE") licensing requirement proposed by the Litigating States does just that. More specifically, a remedy that acts directly to undermine the applications barrier to entry, for instance by requiring "porting" of the Office suite to other operating systems platforms, could potentially do precisely what Netscape and Java were poised to accomplish in 1995-98 -- "commoditize" the operating systems and thus allow operating systems competition to occur on the basis of efficiency and consumer demand, rather than hardware lock-in. In any event, by ignoring the economic importance of the competition destroyed by Microsoft's wide range of exclusionary practices, the PFJ fails to address the central lesson of this litigation. It does not redress the core Sherman Act violations on which liability was unanimously affirmed by the en bane Court of Appeals.
The relief proposed by the Litigating States acts directly to deny Microsoft the fruits of the violation (Interact Explorer licensing), pry open the operating systems market to competition (Java must carry) and erode the barrier to entry protecting Microsoft's monopoly power (applications porting). It is precisely these omissions m consequences of the Department's current, erroneously truncated remedy analysis m that fatally undermine the legal sufficiency of the PFJ. The Department's proposed remedy flatly contradicts the Court of Appeals' directives and thus "the public interest as expressed in the antitrust laws." SENATE REPORT, supra, at 5.
The PFJ purports to provide applications developers with the tools to create competing platforms, but the proposed decree fails to achieve even the narrow goals it sets out to accomplish. The PFJ neither creates the conditions under which new middleware competition can flourish nor provides OEMs with the freedom to support such middleware in the event these technologies avoid the predatory acts of Microsoft.
Most predatory conduct fails to achieve or maintain monopolization because the aggressor must incur greater costs than its prey in order to keep or drive competitors from the market. What this litigation has shown is that Microsoft has numerous weapons in its arsenal to impose far greater damage on its competitors than the loss Microsoft suffers by using such weapons. Controlling the disclosure of the Application Program Interfaces ("API") and the related technical information, imposing conditions on OEM licenses, "commingling" or bolting of software code and products are all examples of weapons Microsoft employed in its predatory attack on Netscape's Navigator and Java technologies. The PFJ does nothing to protect Microsoft from using the same tactics against any future middleware threats.
The PFJ purports only to make public those APIs between the operating system and Microsoft middleware that run on top of the operating system. It does not accomplish even that narrow result. To name a few, the convoluted definitions and exemptions to the API disclosure obligation allow Microsoft itself to decide which APIs will be subject to the disclosure requirement and when those APIs will be released. The decree also permits Microsoft to design and bundle its products in different ways to evade the disclosure requirements, for instance by permitting Microsoft in "its sole discretion" to decide what software comprises a "Windows Operating System Product." PFJ, 66 Fed. Reg. at 59459. With some simple packaging decisions, Microsoft can unilaterally dictate whether middleware competitors will receive the interoperability information necessary to innovate. In short, as explained in detail below, the API disclosure provisions are riddled with numerous deficiencies that render them ineffective in promoting competition.
These are not loopholes, but triumphal arches that allow Microsoft to proceed uninhibited by the antitrust laws. The PFJ expressly allows Microsoft to play a game of form over substance by categorizing pieces of code into different defined terms. The operation of the disclosure requirements is devoid of any notion of technological or economic efficiency.
The PFJ relies almost exclusively on OEMs to restore competition, a naive hope at best. OEMs do not have the resources or the economic incentive to create competition for Microsoft. In any event, the provisions regarding OEM flexibility to distribute competing middleware products ignore the economic realities of the software industry. Most importantly, the decree fails to provide OEMs and consumers with the flexibility to support competing middleware or other new technologies that Microsoft may deem as a threat to its monopoly position. The add/remove provisions in the proposed decree only allow for removal of end user access, i.e., the icon for Microsoft middleware, not the middleware itself. As discussed in the accompanying Declaration of Kenneth Arrow (Attachment A), Nobel laureate and the Department's own expert in Microsoft I, this perpetuates the applications barrier to entry that is at the heart of this litigation. Thus, the OEM provisions enhance rather than erode Microsoft's operating system monopoly power.
Even if these serious deficiencies in the structure, scope and language of the proposed decree were corrected, the settlement would still not create the conditions for a competitive operating systems market. The proposed decree hardly deals at all with Microsoft's likely future anticompetitive conduct. Microsoft's prodigious market power is now directed at the next threat to the Windows platform -- applications and services provided via the Internet and other networks m not the Netscape/Java threat of 1995-99. Microsoft has destroyed those revolutionary technologies that are a source of operating systems competition and has moved on to other areas that the proposed decree all but ignores.
*****
The PFJ fails to serve the public interest and to achieve the settled goals of monopolization relief reaffirmed in the Court of Appeals' decision. It ignores the changing market realities, and the core violations upheld by the D.C. Circuit. The proposed settlement exhibits an unjustifiable deference to a convicted monopolist in designing its products and determining the scope of the remedy. In doing so, it renounces its purported goal of creating the conditions for new middleware threats to flourish. Additionally, it clearly fails to deny Microsoft the "fruits" of its violations and "terminate" its monopoly power. It is precisely these flaws that fatally undermine the legal sufficiency of the PFJ. In contrast, the relief proposal by the Litigating States includes provisions, such as Interact Explorer licensing, Java must carry, applications porting, sufficient and timely disclosure of information, and the freedom to license unbundled Microsoft products, just to name a few, which deny Microsoft the fruits of the violation, pry open the OS market to competition and erode the barrier to entry protecting Microsoft's monopoly power. As a matter of law, the Department's settlement proposal cannot be said to be consistent with "the public interest as expressed in the antitrust laws," SENATE REPORT, supra, at 5, where it has proposed a remedy without reference to those laws as reiterated by the Court of Appeals in this very case.
This is the only substantial Government Section 2 case in more than 30 years litigated through trial to judgment, appeal and dual opportunities for Supreme Court review.1 A "rush to judgment" is simply not the appropriate course of judicial review under the Tunney Act, or otherwise. A decision on the adequacy of the proposed decree should therefore be deferred until after the conclusion of the evidentiary heating on the remaining Plaintiffs' ("Litigating States") relief proposals. Moreover, the normal Tunney Act flexibility accorded to the Government in offering a proposed pretrial antitrust settlement cannot hold in the unique circumstances of this case, in which the Court is obligated to conduct a searching, independent inquiry into the proposed decree, with no deference accorded to the government.
No court has ever approved an antitrust settlement where, as here, there are remaining plaintiffs in the very same consolidated action that are about to begin a full remedies hearing based on adjudicated Sherman Act liability that has been affirmed on appeal. In this unprecedented case,2 it is essential that the Court evaluate all available evidence bearing on the "'public interest" of the Department's proposed settlement.
The Tunney Act sets no deadlines. Neither the Act nor its legislative history in any way encourages "fast-track" review. Instead, the Act expressly allows the Court to set its own schedule and to tailor its judicial review process to the facts and circumstances of each antitrust case. 15 U.S.C. §§ 16(1)3 As the Senate sponsor of the Tunney Act explained:
- INTRODUCTION.
- Standard of Tunney Act Review
- Failure to Satisfy Settled Monopolization Remedies Law
- Failure to Redress Core Violations
- The PFJ Does Not Achieve its Purported Goals
- The API Disclosure Requirements
- OEM Desktop Flexibility
- The PFJ Fails to Address Competitive Issues that Will Determine the Future of the Software Industry
- THE COURT SHOULD DEFER DECISION ON THE PROPOSED DECREE UNTIL AFTER THE LITIGATING STATES' REMEDIES HEARING AND SHOULD APPLY THE SETTLED ANTITRUST REMEDY STANDARD EXPRESSLY REAFFIRMED IN THIS CASE BY THE COURT OF APPEALS
- Approving the Proposed Decree Before Completion of the Remedy Hearings Would Be Wholly Unprecedented and Highly Prejudicial
- Waiting to Rule on the Proposed Decree Until After the Remedies Trial Avoids Pre-Judging the Remedies Case and the Prospect of Inconsistent Rulings
- Deferring Ruling on the Proposed Decree Promotes the Tunney Act's Express Goal of Conserving Judicial Resources
- The Applicable Legal Standard for Reviewing the Proposed Decree is the Ford/United Shoe Test Specifically Mandated by the Court of Appeals
- The Court Owes No Tunney Act Deference To the Department in this Unprecedented Post-Trial, Post-Appeal Settlement
- The AT&T Model is Instructive by Conducting a Searching Inquiry into the Scope, Adequacy and Effectiveness of the Proposed Decree
- THE PROPOSED FINAL JUDGMENT IS INSUFFICIENT UNDER ANTITRUST REMEDIES LAW AND DOES NOT MEET THE STANDARD ARTICULATED BY THE DEPARTMENT
- The Decree Does Not "Undo" the Competitive Harm Resulting from Microsoft's Anticompetitive Practices
- The Proposed Settlement Fails to Deny Microsoft the Ill-gotten Fruits as Required by Established Antitrust Law
- The Decree Does Not Terminate or Redress Numerous Practices that the Court of Appeals Found to Violate the Sherman Act
- Integration of Windows and Middleware
- Coercion and Market Allocation
- Deception and Product Sabotage
- THE API DISCLOSURE AND OEM FLEXIBILITY PROVISIONS OF THE PROPOSED DECREE WILL NOT CREATE THE OPPORTUNITY FOR MIDDLEWARE COMPETITION
- The Proposed Decree's Provisions for Information Disclosure Do Not Assure that Future Middleware Competitors Will Have Access to Necessary Interoperability Information
- The API Provision's Scope is Far Too Narrow
- The API Provision of the PFJ Constructs an Illusive Framework for Disclosure of Interoperability Information
- Defined Terms Within the API Disclosure Provision Leave All Material Disclosure Determinations to Microsoft
- The API Disclosure Provision Also Leaves Critical Terms Undefined
- Under Provision III.D, APIs Will Never be disclosed in a Timely Manner
- The Exceptions from and Preconditions to API Disclosure Further Narrow the Scope of an Already Unworkable Disclosure Provision
- Cross-Licensing of Middleware APIs
- Timing of API Disclosure Obligation
- The Communications Protocol Provisions of the Decree Do Not Require Release of any Server APIs and are Based on Terms the Department Failed to Include in the Settlement
- The Proposed Decree's Provisions for OEM Flexibility Do Not Open the PC Manufacturing Channel to Future Middleware Competitors
- The OEM Provisions Place Sole Responsibility for Introducing Middleware Competition on PC Manufacturers
- The Provisions Allowing OEM Flexibility Do Not Address the Key Issue of Microsoft's Ubiquitous Middleware Development Platform
- The OEM Provisions Do Not Create a Level Playing Field for Middleware Desktop Competition
- Additional OEM Provisions Further Undermine the Crucial Ability of ISVs to Differentiate Competing Middleware Products
- The OEM Provisions Contain Other Superfluous Terms that Substantially Limit Any Potential Market Impact
- The OEM Provisions Have No Impact on Java
- The OEM Provisions Largely Codify Microsoft's Existing Business Practices
- The Proposed Decree Does Not Effectively Preclude Microsoft's Exclusive Dealings
- Current Market and Economic Realities Demonstrate that the PFJ is Incapable of Having Any Substantial Procompetitive Impact
- New Monopolies Enable Microsoft to Protect its Operating System Monopoly Despite the PFJ
- The Proposed Settlement Ignores the Likely Tactics Microsoft Will Use to Eliminate the Next Significant Threat to its Monopoly Position
- The Decree Increases Microsoft's Market Dominance and Actually Worsens Competitive Conditions in the Relevant Software Markets
- The Settlement Would Not Have Prevented Microsoft's Unlawful Campaign Against Netscape and Java
- THE PROPOSED DECREE IS HOPELESSLY VAGUE AND INHERENTLY UNENFORCEABLE
- DIVESTITURE REMAINS THE PREFERABLE AND MOST EFFECTIVE REMEDY FOR MICROSOFT'S SECTION 2 VIOLATIONS
- THE COURT SHOULD CONDUCT A RIGOROUS TUNNEY ACT EXAMINATION OF THE DECREE, THE COMPETITIVE IMPACT STATEMENT AND THE DEPARTMENT'S UNSUBSTANTIATED PROJECTIONS OF FUTURE COMPETITIVE EFFECT
- The Complexity and Substantial National Importance of this Case, the Government's Flat Reversal of Position and its Disregard of Clear Tunney Act Obligations All Dictate the Necessity of Critical Judicial Oversight in this Landmark Proceeding
- This Complex, Controversial, Nationally Important Antitrust Prosecution Demands Serious Judicial Oversight
- Heightened Scrutiny is Needed Because Neither the Department Nor Microsoft Complied With their Respective Tunney Act Obligations
- The Court Should Closely Examine the Government's Reversal of Position on Relief
- Live Evidence is Needed on the Technical and Economic Complexities of the Software Industry and the Profound Failings of, and Harms Caused by, the PFJ
- CONCLUSION
-
-
- Standard of Tunney Act Review
-
- Failure to Satisfy Settled Monopolization Remedies Law
-
- Failure to Redress Core Violations
-
- The PFJ Does Not Achieve its Purported Goals
-
-
- The API Disclosure Requirements
-
-
- OEM Desktop Flexibility
-
- The PFJ Fails to Address Competitive Issues that Will Determine the Future of the Software Industry
-
-
- Approving the Proposed Decree Before Completion of the Remedy Hearings Would Be Wholly Unprecedented and Highly Prejudicial
-
-
- Waiting to Rule on the Proposed Decree Until After the Remedies Trial Avoids PreJudging the Remedies Case and the Prospect of Inconsistent Rulings
The decision to make [Tunney Act] procedures discretionary is dictated by a desire to avoid needlessly complicating the consent decree process. There are some cases in which none of these procedures may be needed. On the other hand, there have been and will continue to be cases where the use of many or even all of them may be necessary. In fact, in a very few complex cases, failures to use some of the procedures might give rise to a, indication that the district court had failed to exercise its discretion properly.
119 Cong. Rec. 3453 (statement of Sen. Tunney) (emphasis added).
This highly complex case demands that the Court utilize all available procedures for evaluating the adequacy of the proposed decree and the evidentiary basis of the economic projections that underly the Department's remedial scheme. Deferring decision on the proposed decree is the only sensible approach. The Court's consideration of testimonial and other evidence on the failings of the decree will avoid unfair pre-judgment of the remedies remand and the entry of potentially conflicting relief. It also offers the most efficient means of ensuring that the many issues raised by the proposed decree and the Court of Appeals' decision receive a thorough hearing on the merits. Deferring judgment will not harm any party or inconvenience the Court, given that the Litigating States' upcoming remedies trial is scheduled to begin just thirteen days after the completion of the Tunney Act comment process.4 Indeed, neither the Justice Department nor Microsoft can claim to be prejudiced by a short deferment in judgment on the PFJ, because Microsoft represents that it is already complying with the terms of the proposed decree.
Deferral would also avoid the highly undesirable result of inconsistent judgments. The Litigating States' remedy proposal differs markedly from the proposed settlement in breadth, scope and approach. A premature ruling on the PFJ would force the Litigating States either to (1) pursue their relief proposal in full, knowing there may be inconsistent remedy orders issued by this Court that would make compliance difficult, if not impossible, or (2) stunt their case by limiting their proposed remedies to those that can be implemented in a manner consistent with the PFJ, even though they have already rejected that settlement as inadequate.
The Court faces a similar, untenable choice if it seeks to issue an early ruling on the proposed decree. The Court would have to limit its ultimate remedy order to the terms already required by its ruling on the Department's settlement, or order new remedies but vacate those portions of the PFJ that are inconsistent with the subsequent decree. This dilemma is easily avoided, however, by waiting to resolve the issues raised by the Tunney Act comments until after the Litigating States and Microsoft have had a full and fair opportunity to present evidence supporting their respective remedy proposals.
Avoiding conflicting remedial orders alone is reason enough to defer judgment on the decree. Inconsistent judgments are to be avoided in antitrust as in all complex litigation. See In re Transit Co. Tire Antitrust Litigation, 67 F.R.D. 59, 65 (W.D. Mo. 1975) (separate relief hearings "would result in duplication of effort [and] possible inconsistent judgments"). It is well-established that "[t]he avoidance of logically inconsistent judgments in the same action" is a "just reason for delay[ing]" entry of final judgment in multi-party civil actions.5
The Court should give particular weight to considerations of uniformity in this case, because of the great need to ensure that all in the software industry -- suppliers, customers and competitors -- face a fair and even playing field. As the Supreme Court has held, antitrust violations should be remedied "with as little injury as possible to the interest of the general public." United States v. American Tobacco Co., 221 U.S. 106 (1911). Thus, "the Court would be justified in rejecting the proposed decree or requiring its modification if it concluded that the decree unnecessarily conflicts with important public policies other than the policy embodied in the Sherman Act." AT&T, 552 F. Supp. at 151. In this case, such an important public policy is the uniform application of antitrust law to the national software market.
-
-
- Deferring Ruling on the Proposed Decree Promotes the Tunney Act's Express Goal of Conserving Judicial Resources
Deferring judgment on the proposed decree will also conserve judicial resources by allowing the Court to determine which questions raised by the PFJ can be resolved by the testimony and other evidence offered in the remedy trial. The Court may then limit or avoid duplicative evidence that must be adduced to assess whether the decree meets the applicable substantive standard for Tunney Act judicial review.
Consent decrees subject to Tunney Act review are generally used to obviate trial -- to avoid "extended proceedings" and provide a "'prompt and less costly'" means of resolving antitrust suits pre-litigation. CIS, 66 Fed. Reg. at 59476 (quoting 119 Cong. Rec. 24598 (1973)). Even the Department of Justice, in discussing the negotiation of antitrust settlements in its Practice Manual, identifies the consent decree as the best way to obtain relief "without taking the case to trial." Antitrust Division Manual, Ch. IV, § E, at 50 (3 rd ed. 1998) (emphasis added). Here, however, a liabilities trial has already occurred, and a remedies trial must occur regardless of when or whether the proposed Department settlement is approved. There is little or no court action to avoId. As a result, judicial resources are best conserved and most efficiently allocated by holding the remedies trial before ruling on the PFJ.
-
- The Applicable Legal Standard for Reviewing the Proposed Decree is the Ford/United Shoe Test Specifically Mandated by the Court of Appeals
In no reported case since adoption of the Tunney Act in 1974 has the Department sought to settle a monopolization action after prevailing at trial and on appeal. The CIS nonetheless suggests that in assessing the adequacy of the proposed decree under the Act, this Court must approve a settlement that is less than the remedy the Court would otherwise impose of its own accord. CIS, 66 Fed. Reg. at 59476 (citations omitted). In the unprecedented procedural posture of this case, it cannot.
The Court of Appeals agreed that relief in this case must seek to "terminate" Microsoft's operating system monopoly, to "unfetter" barriers to competition to the operating systems market, to "deny" Microsoft the "fruits" of its statutory violations, and to "ensure" there are no practices "'likely to result in monopolization in the future"'6 That mandate is binding on this Court as well as the litigants. The Supreme Court has "consistently held that an inferior court has no power or authority to deviate from the mandate issued by an appellate court." Briggs v. Pennsylvania R. Co., 334 U.S. 304, 306 (1948). Indeed, even prior to the Tunney Act the Supreme Court emphasized that in antitrust cases, "[t]he Department of Justice ... by stipulation or otherwise has no authority to circumscribe the power of the courts to see that [their] mandate is carried out." Cascade Natural Gas Corp. v. El Paso Natural Gas Co., 386 U.S. 129, 136 (1967). 7 Consequently, in the unique procedural posture of this case, the "public interest as expressed in the antitrust laws," SENATE REPORT, supra, at 5, is the Court of Appeals' mandate itself.
The D.C. Circuit did not establish a new legal standard for monopolization relief, but rather adopted the traditional test developed by the Supreme Court decades ago. See Microsoft. III, 253 F.3d at 103 (quoting Ford Motor Co. v United States, 405 U.S. 562, 577 (1972), and United States v. United Shoe Mach. Corp., 391 U.S. 244, 250 (1968)). Notably, however, the CIS does not even cite, let alone argue, that the PFJ meets the D.C. Circuit's remedial standard. The Department instead offers its own view that "[a]ppropriate injunctive relief in an antitrust case should: (1) [e]nd the unlawful conduct; (2) avoid a recurrence of the violation and others like it; and (3) undo its anticompetitive consequences." CIS, 66 Fed. Reg. at 59465 (citations omitted). This lesser standard is invalid because it ignores the Supreme Court's directives to "'terminate" the monopoly and to eradicate the "fruits" enjoyed by the unlawful monopolist.
To the extent that DOJ may contend this case is different because the acquisition of Microsoft's monopoly was not challenged, rather the unlawful maintenance of that monopoly, it would be incorrect. There is no legal basis to distinguish between the methods of monopolizalion either for liability or relief purposes, and neither DOJ nor Microsoft has ever cited a case making such a distinction. The adverse consumer welfare and economic efficiency consequences of monopoly power are the same whether a monopoly was illegally acquired, illegally maintained or both. Indeed, the D.C. Circuit was well aware that the achievement by Microsoft of a Windows monopoly in the first instance was not alleged to he unlawful, 8 but nonetheless specifically adopted the traditional Ford/United Shoe remedy standard.
The Court of Appeals' carefully crafted and detailed opinion can hardly be deemed to have applied this standard by accident. Accordingly, notwithstanding Microsoft's claim, it is simply not true that "contrary to the critics' overheated rhetoric, there is no basis for relief designed to terminate an `illegal monopoly.'"9 The fact that a monopoly was acquired lawfully does not provide any defense, because the monopolist forfeits its right to continue to hold even a lawfully acquired monopoly when it violates the Sherman Act in its preservation.10
The Department and Microsoft may argue that the Court of Appeals' "drastic" modification of liability is of crucial significance in evaluating the scope of a remedy. See Microsoft III, 253 F.3d at 105. What this contention ignores is that the Court of Appeals reversed or remanded separate, distinguishable legal theories for Sherman Act liability that all arose from the same set of operative facts. As the government explained to the Supreme Court:
The court of appeals affirmed the district court's central ruling that Microsoft violated Section 2 of the Sherman Act by engaging in an unlawful course of conduct to maintain its monopoly of the market for Intel-compatible PC operating systems. With minor exceptions, the court agreed with the district court's findings and conclusions that Microsoft's restrictions on original equipment manufacturers; its bundling of Internet Explorer into Windows; its dealings with internet access providers, independent software vendors, and Apple Computers; and its efforts to contain and to subvert Java technologies that threatened Microsoft's operating system monopoly, all served unlawfully to maintain the Windows monopoly.
Brief for the United States in Opposition [To Certiorari], Microsoft Corp. v. United States, No. 01-236, at 5 (S. Ct. filed Aug. 2001) (emphasis added; citations omitted). And the Court of Appeals added the explicit, highly unusual caution that "[n]othing in the Court's opinion is intended to preclude the District Court's consideration of remedy issues."11 That the lesser included offenses of attempted monopolization and tying were not upheld does nothing to subtract from the seriousness of the widespread Section 2 violations affirmed by the Court of Appeals or the Court's explicit reaffirmation of the Ford/United Shoe standard for antitrust relief.
The CIS" lengthy recitation of cases indicating that a Tunney Act court must accept a lesser remedy than might be obtained after trial is irrelevant. CIS, 66 Fed. Reg. at 59475-76. None of these cases arose in the context of a post-trial settlement of a Section 2 monopolization claim and thus none resolved whether the remedial standard adopted by the federal courts in a fully litigated antitrust case must be jettisoned if the government subsequently agrees to a consensual decree.12 More importantly, the Department has not offered any statutory or policy basis 1o justify its wooden invocation of Tunney Act dicta to this case. By failing to articulate any legitimate justification for the deference it insists upon, the Department's position suggests that it is designed to shield the merits of the decree from critique by the Court and to mask the weakness of the proposed settlement, rather than to satisfy any compelling institutional or constitutional policy.
The only suggestion in the CIS as to any basis for a limited scope of judicial review is just wrong. The Department insists that a different relief standard is "particularly" appropriate "where, as here, court's review of the decree is informed not merely by the allegations contained in the Complaint, but also by the extensive factual and legal record resulting from the district and appellate court proceedings." CIS, 66 Fed. Reg. at 59476. That has things backwards. In normal Tunney Act cases, the law is clear that respect is to be accorded to the Department's antitrust enforcement judgments w its "perceptions of the market structure and its view of the nature of the case" -- precisely because there is no factual or legal record before the court. Microsoft I, 56 F.3d at 1448. When a Sherman Act case has been litigated and affirmed on appeal, however, the district court is fully capable of assessing the proposed remedy against that record and its "familiarity with the market involved." Id. at 1461.13 In short, the Court of Appeals" mandate, and its application of traditional monopolization remedy law, is the applicable standard against which to measure the scope and efficacy of the PFJ.
-
- The Court Owes No Tunney Act Deference To the Department in this Unprecedented Post-Trial, Post-Appeal Settlement
The language, legislative history and purpose of the Tunney Act all indicate that the relatively deferential attitude ordinarily adopted by courts to antitrust settlements should not constrain this Court's inquiry into the legal sufficiency and acceptability of the remedy proposed by Microsoft, the Department and the Settling States.
The leading authority on Tunney Act deference is not at all to the contrary. In Microsoft I, the D.C. Circuit reversed the district judge for "construet[ing] his own hypothetical case and then evaluat[ing] the decree against that case." 56 F.3d at 1459. Here, no one is asking the Court to consider claims the government chose not to pursue. Quite to the contrary. ProComp asks the Court to grant effective relief for those claims that the Department actually brought and on which it has already prevailed.
The difference in judicial deference owed to the Executive Branch is easily understood against this backdrop. The Tunney Act was created as a "check on prosecutorial discretion," In re IBM, 687 F.2d 591,595 (2d Cir. 1982), that is, "a check.., on the government's expertise m or at the least, its exercise of it -- even on its good faith." United States v. Gillette Co., 406 F. Supp. 713, 715 (D. Mass. 1975). The concern of Congress was the predominance of pretrial antitrust settlements that otherwise would never reach a courtroom,14 For these reasons, the Microsoft I decision cautions that a district court's Tunney Act obligation to avoid delving too deeply into the substantive merits of antitrust settlements arises because "there are no findings that the defendant has actually engaged in illegal practices." Microsoft I, 56 F.3d at 1460 (emphasis in original).
That is obviously not the case here. Microsoft's liability for a wide variety of exclusionary practices violative of Section 2 of the Sherman Act has been adjudicated and affirmed on appeal. In contrast, it is clear that the Tunney Act was predicated on the assumption that proposed consent decrees would be presented in the context of pretrial settlements over which the courts had yet to engage in an exercise of judicial power. See 15 U.S.C. § 16(e)(1) (district court must "evaluate the competitive impact of... termination of alleged violations ...."); § 16(e)(2) (court must consider "the public benefit, if any, to be derived from a determination of the issues at trial"). Unlike the ordinary Tunney Act situation, in this case it is indisputably not correct to conclude that "[r]emedies which appear less than vigorous may well reflect an underlying weakness in the government's case." Microsoft I, 56 F.3d at 1461.
The Tunney Act's underlying principles of judicial restraint applicable to the exercise of prosecutorial discretion -- deeply rooted in separation of powers -- simply do not apply here.15 In the typical Tunney Act case, courts have made "no judicial finding of relevant markets, closed or otherwise, to be opened or of anticompetitive activity to be prevented," is by definition not present in a post-appeal antitrust settlement. Maryland v. United States, 460 U.S. 1001, 1004 (1983) (per curiam) (Rehnquist, J., dissenting). The separation of powers concerns in a post-trial settlement are actually reversed. 16 The source of Tunney Act deference is that "the court's authority to review a decree depends entirely on the government's exercising its prosecutorial discretion by bringing a case in the first instance." Microsoft I, 56 F.3d at 1459-60 (emphasis added). In contrast, deferential review of a post-trial settlement in a fully litigated, finally appealed antitrust prosecution would directly contradict the "mandate rule" of Cascade Natural Gas and would be inconsistent with this Court's Article III obligations.
The Court of Appeals has explained that because there are "constitutional difficulties that inhere in this statute," it is "inappropriate for the [district] judge to measure the remedies in the decree as if they were fashioned after trial." Microsoft I, 56 F.3d at 1461. The converse is true when a remedy is in fact fashioned after trial. In that situation, the court has already made the factual and legal findings that do not exist in the ordinary consent decree situation, and therefore is not required to "give due respect to the Justice Department's perception of the market structure and its view of the nature of the case." Id. at 1461.
In light of these serious constitutional concerns, this Court should not and cannot accept a proposed decree that falls short of the remedy that the Court would impose based on its own, independent assessment of the record and the Court of Appeals' remand mandate. The Court is undoubtedly aware of the long-standing maxim that constitutional questions are to be avoided if a statute can be interpreted so as not to raise them. E.g., Richmond Screw Anchor Co., 275 U.S. 331, 346 (1928). In the context of this unprecedented Tunney Act case, simple prudence dictates that the Court should construe the Act to dispense with deference to the government where liability has been adjudicated and affirmed on appeal, and thus avoid any possibility of a constitutional challenge to its remand decision on remedies.
Before turning to a substantive critique of the PFJ, it is appropriate to discuss the close parallels between Microsoft and the last major monopolization settlement presented by the Department and decided by this Court (Harold Greene, J.) under the Tunney Act. United States v. AT&T, 552 F. Supp. at 151.
Before the AT&T settlement was proposed, Judge Greene had heard the vast majority of the evidence--on all issues except remedy -- and had denied AT&T's motion to dismiss on the merits after the close of the government's case-in-chief. United States v. AT&T, 524 F. Supp. 1336, 1380 (D.D.C. 1981). Following a wide-ranging Tunney Act process that included evidentiary hearings, third-party submissions, and several days of oral augment, Judge Greene declined to approve the decree as proposed -- even though it required divestiture of the Bell system -- because he concluded that it was substantively inadequate, precluded the Court from effective oversight and enforcement, and posed a risk of harming third parties.
The Judge insisted upon substantial modifications to the proposed decree before he would enter the settlement under the Tunney Act's public interest standard. In doing so, Judge Greene explained that ,AT&T was "not an ordinary antitrust case." 552 F. Supp. at 151. Instead, in that case as in this one, the proposed decree was an "enormous undertaking" having "significant consequences for an unusually large number of ratepayers [i.e., consumers], shareholders... and competitors." 552 F. Supp. at 152. In addition, and also like in this case, the Court would "be able to render sound judgments" because it "ha[d] already heard what probably amounts to well over ninety percent of the parties' evidence both quantitatively and qualitatively, as well as all of their legal arguments." Id. For these reasons, Judge Greene concluded that "it does not follow that [the Court] must unquestionably accept a consent decree as long as it somehow, and, however inadequately, deals with the antitrust problems implicated in the lawsuit." Id. Instead, Judge Greene reasoned it was his responsibility to ensure the decree protected consumers, opened the relevant markets to effective competition in a timely manner, and would be readily enforceable. The Supreme Court affirmed. Maryland v. United States, 460 U.S. 1001 (1983) (per curiam); California v. United States, 464 U.S. 1013 (1983)(per curiam).
Like AT&T, this has been a long, exceedingly complex and very hard-fought case. Unlike AT&T, however, in this litigation the proposed settlement comes after the trial was completed and after the courts finally adjudicated the defendant's liability. Also' unlike AT&T, moreover, here the government has not succeeded in obtaining via settlement anything close to the relief it sought on the merits from this Court. We have submitted our view that deference to the Department of Justice is inappropriate in this unique case. The AT&T model provides a benchmark for the scope of Tunney Act judicial review which, if anything, should be exceeded given the far more advanced procedural posture here. This Court cannot err by following an expanded AT&T-like procedure. The converse may not be true.
*****
In sum, the Litigating States must be allowed to proceed free from the interference that early Court approval of the proposed decree would entail. When the Court does assess and rule on the decree, it must undertake a thorough, independent analysis of whether the settlement protects the public interest and satisfies the D.C. Circuit's mandate for effective relief. Delegating this core judicial responsibility to the Department would violate the Tunney Act, raise serious separation-of-powers concerns and leave the public without effective redress against a proven monopolist.
The proposed settlement does not meet the D.C. Circuit's remedial standard, quoted above, to terminate the monopoly, deny the defendant its ill-gotten fruits, and ensure that monopoly practices cannot arise in the future. The CIS does not even cite, let alone argue that the PFJ meets the D.C. Circuit's remedial standard. Indeed, the PFJ does not even meet the lesser standard, articulated in the CIS, to "(1) end the unlawful conduct; (2) 'avoid a recurrence of the violation' and others like it; and (3) undo its anticompetitive consequences." CIS, 66 Fed. Reg. at 59465 (citations omitted).
In fact, the proposed settlement fails to undo the competitive harm from the core antitrust violations affirmed by the Court of Appeals, and does not even address a series of additional violations of the Sherman Act upheld by the Court of Appeals.
Netscape's browser and Sun's Java were revolutionary middleware technologies which allowed Independent Software Vendors CISVs") to write programs that would run on any operating system, thus potentially making hardware platforms - and correspondingly, operating systems -- a matter of competitive and technological indifference. Microsoft both recognized and feared that this new model for software development would be an inflection point in the computer industry, 17 and accordingly launched a multi-faceted campaign to destroy the economic and technological viability of these forms of competing middleware.
United States v. Microsoft Corp., 87 F. Supp.2d 30, 38-39 (D.D.C. 2000) (Conclusions of Law), affirmed in part, 253 F.3d 34 (D.C. Cir.), cert. denied, 530 U.S. 1301 (2000).
The Court of Appeals affirmed the illegality of Microsoft's campaign to destroy the competitive threat of Internet browsers and cross-platform Java technology. Further, as the Court of Appeals explained, Sun's distribution arrangement with Netscape was key to .,"'achiev[ing] the necessary ubiquity on Windows" required for Java to serve "as the ubiquitous platform for software development." Microsoft III, 253 F.3d at 74, 75. By foreclosing Netscape from the market, Microsoft thus eliminated the ability of the Java runtime environment to develop into a ubiquitous, competitive alternative to Windows for applications development.18 Today, the anticonsumer effects are even more clear because Microsoft has integrated its own Internet browsing and Java-like runtime technologies into Windows.
No other middleware technologies introduced since Netscape and Java have evolved to the point where they could directly challenge, and substitute for, Windows. While a variety of middleware is available today, most if not all presently lack the capability to serve as major platforms for software development. As Professor Arrow explains, no middleware entrant currently exists that offers the user base, head start and technological capability to supplant Windows, characteristics enjoyed by both Netscape and Java before Microsoft eliminated them as serious competitive threats. Arrow Decl. ¶¶ 25-30. Middleware is more often a short-run complement to the operating system rather than a substitute. It is only when particularly "disruptive technologies" can achieve the distribution scale and scope of exposed APIs to permit substitution among operating systems -- the "commoditized" operating systems feared by Microsoft -- that middleware becomes a long-run competitive substitute for the operating systems. Id. ¶¶ 16-17, 33-34. Powerful middleware substitutes for Microsoft's operating systems monopoly just do not come along every week. Id. ¶ 18 ("Technological disruptions such as the middleware threat of the mid-1990s do not occur continually.")
Microsoft's anticompetitive practices destroyed the prospect that middleware could effect such a fundamental change (sometimes called a "paradigm shift') in the operating system market and, thus, have substantially entrenched its monopoly power. "Microsoft's significantly enhanced ability to stem potential middleware threats is the result, in very substantial part, of its past anticompetitive campaign against Netscape."19 As Professor Arrow explains, "[a]t times of technological disruption, the forces of dynamic competition play an especially important role." Id. ¶ 18. See Findings of Fact ¶ 377 ("Microsoft "successfully denied" Netscape status of "the standard software for browsing the Web").20 It will be "exceedingly difficult now, even with the best of remedies, to re-establish middleware fully as the kind of competitive threat to Microsoft's monopoly power that it posed in the mid-1990s." Arrow Decl. ¶¶ 5, 18, 71. Thus, as Professor Arrow concludes, it is "highly unlikely" that "market forces alone will lead to the development of innovative middleware that creates the same competitive risk to Microsoft that it faced from Navigator and Java in 1995." Id. ¶ 30.
Despite these compelling facts, the Department and the Settling States have proposed middleware provisions that ignore the core Internet browser and Java runtime technologies in favor of undefined, future middleware that may or may not present the same viable cross-platform capabilities. The Department's remedy ratifies the illegal acts that Microsoft committed, instead of moving the market forward to where it would be today had Netscape and Java been permitted to grow without illegal Section 2 constraint.21 The Supreme Court, however, has squarely rejected the proposition that "antitrust violators may not be required to do more than return the market to the status quo ante." Ford, 405 U.S. at 573 n.8.
Assistant Attorney General James explains that the settlement is designed "to recreate the potential for the emergence of competitive alternatives to Microsoft's operating system monopoly through middleware innovations."22 But without identifying any comparable middleware products today or predicting that truly competitive middleware will be introduced in the near-term future that could become substitutes for Windows, the Department does not have a verifiable basis to project that such a remedy will have any impact on competition. The Department's proposed settlement posits only hypothetical future entry to counteract the very real monopoly power of Windows today.
In addition, Microsoft's integration of Internet browsing and runtime environment technology into Windows allows Microsoft today to prevent any competing middleware technology from achieving ubiquity, thus preserving the applications barrier to entry.23 Unlike the Netscape and Java technologies that Microsoft's unlawful practices eliminated as serious competitive threats, however, Microsoft middleware is not cross-platform. Consequently, by sanctioning Microsoft's integration of middleware into Windows and by failing to redress its illegal campaign against Netscape and Java, the proposed decree enhances, rather than reduces, Microsoft's operating systems monopoly power. In short, the PFJ does not undo the competitive harm resulting from Microsoft's unlawful assault on Netscape and Java, and therefore, fails to meet the requirements of established antitrust law and the lesser standard the Department has set.
Equally importantly, in clear denial of the standards under established antitrust remedies law, the decree permits Microsoft to retain the fruits of its statutory violations. See United Shoe, 391 U.S. at 252. It "would be inimical to the purpose of the Sherman Act to allow monopolists free rein to squash nascent, albeit unproven, competitors at will -- particularly in industries marked by rapid technological advance and frequent paradigm shifts." Microsoft III, 253 F.3d at 79. Consequently, because the PFJ fails to "deny to [Microsoft] the fruits of its statutory violation," id. at 103, it cannot be approved by this Court.
There are remedial alternatives available to restore Internet browsers and cross-platform runtime technology to the position they would have achieved -- ubiquitous distribution without any "lock-in" to the Windows operating systems D in the absence of Microsoft's violations. The open source Internet Explorer licensing requirement proposed by the Litigating States does precisely that. A remedy that acts directly to undermine the applications barrier to entry, for instance by requiring "porting" of the Office suite to other operating system platforms, would act to commoditize the operating system and thus allow operating systems competition to occur on the basis of efficiency, technology and consumer demand. 24 See Arrow Decl. ¶ 46-49.25
In sharp contrast, the proposed decree is described in the CIS as encouraging the development of future technologies that "over time could help lower the applications barrier to entry." CIS, 66 Fed. Reg. at 59467 (emphasis added). As no significant platform innovations with the characteristics necessary to substitute for Windows have developed since Microsoft's multi-faceted predatory campaign was launched, there is simply no reason to believe that new Netscape and Java-like middleware competition could flourish today, especially under the decree, which not only does not lower the applications barrier to entry - it actually preserves and strengthens. Therefore, the remedy fails to meet the standard set by established antitrust remedies law by refusing to deny Microsoft the fruits of its unlawful acts, or providing any viable alternative mechanism.
The decree now proposed by the government improperly permits Microsoft to continue some of the very exclusionary practices that the Court of Appeals explicitly held were illegal. Both established antitrust remedies law and the lesser standard articulated by the Department require that the settlement terminate and redress the unlawful conduct affirmed by the Court of Appeals. The settlement does not.
The PFJ does not preclude Microsoft from integrating middleware software, or any other technology that could erode the applications barrier to entry, into its operating system products. Hence, the proposed decree not only does not end Microsoft's practice of binding competing technologies to Windows, but allows middleware integration to continue unabated in the future.
This failure is impossible to square with the Court of Appeals' decision. First, the Court specifically held that "Microsoft's decision to bind IE to Windows 98" by "commingling of code" was an unlawfully "exclusionary" practice. Microsoft III, 253 F.3d at 64-67. The Court of Appeals' discussion is worthy of close attention became it sheds light on the magnitude of the PFJ's failure with respect to product integration. The Court explained that "[t]echnologically binding IE to Windows ... both prevented OEMs from pre-installing other browsers and deterred consumers from using them," Microsoft III, 253 F.3d at 64 (citing Findings of Fact ¶ 159), and thus that "Microsoft's... commingling of browser and operating system code constitute[s] exclusionary conduct, in violation of ¶ 2." Id. at 67. Moreover, the Court of Appeals emphasized that its Section 2 holding rebuffed Microsoft's arguments "not only that its integration of IE into Windows is innovative and beneficial, but also that it requires non-removal of IE." Id. at 89.
Second, the Court summarily denied Microsoft's rehearing petition challenging both the factual basis and the legal sufficiency of the code commingling holding.26 The Court denied without opinion Microsoft's rehearing petition, in which the defendant Microsoft argued that "`commingling of code' is not 'per se pernicious or even suspicious'" and urged the D.C. Circuit to (1) reverse the applicable Findings of Fact, and (2) limit its liability holding with respect to bundling of Internet Explorer to Microsoft's refusal to permit "[r]emoval of end-user access by OEMs."27
In spite of these repeated holdings, the PFJ reverses course and adopts the position for which Microsoft argued on rehearing. The proposed settlement allows OF. Ms to remove "access to" middleware -- that is, icons w from the desktop and related areas of the Windows user interface. Conversely, it permits Microsoft to commingle any code and prohibits OEMs from deleting Microsoft middleware code from the operating system software. Thus, although the Court of Appeals expressly reiterated that technological integration of Interact Explorer violated Section 2, the PFJ fails to impose any limits whatsoever on current or future bundling of middleware and operating systems software.
Assistant Attorney General James has testified that "[t]he court of appeals ruled that, albeit with some limits, Microsoft could lawfully integrate new functions into the operating system."28 This is a mischaracterization. The D.C. Circuit remanded the tying claim for rule of reason analysis, Microsoft III, 253 F.3d at 84-95, but did not conclude that any product integration litigated at trial was "lawful." The only general statement the Court made was that the "integration of additional software functionality into an operating systems" is not a per se unlawful Section 1 offense.29
The D.C. Circuit affirmed that Microsoft's coercion of Apple, by threatening to withhold porting of Office to the Macintosh operating systems platform, was unlawful. The District Court likewise found that Microsoft attempted (this time without success) to coerce Apple into abandoning development of its QuickTime software, in order to limit "the development of multimedia content that would run cross-platform." Findings of Fact ¶ 110.
Microsoft also coerced Intel -- Microsoft's partner in the IBM-compatible PC market m into abandoning its work on creation of Java-compatible multimedia software.(30)Microsoft III, 253 F.3d at 77. In fact, the Court specifically ruled that "Microsoft's threats to Intel were exclusionary, in violation of § 2 of the Sherman Act." Id. at 78 (emphasis added). And the District Court, again without objection by the Court of Appeals, also found that Microsoft pressured Intel to cease development of "Native Signal Processing ('NSP') software, [which] would endow Intel microprocessors with substantially enhanced video and graphics performance,"31 as well as "using revenues from its microprocessor business to fund the development and distribution of free platform-level software," 32 in order to "halt the development of software that presented developers with a set of operating-system-independent interfaces." 33
The proposed decree does not constrain Microsoft's ability to engage in this sort of coercive conduct to impede competition from potential middleware or other software rivals.Section III.F of the PFJ precludes Microsoft only from "retaliating" against ISVs and IHVs that develop or use competing platform software and from entering into exclusive dealings with ISVs (but curiously not IHVs) for platform software. It does not, however, deal with the use of threats and coercion to compel adherence to Microsoft's objectives short of an actual agreement.34 As both a legal and practical matter, the PFJ fails to redress the Court of Appeals' holding that Microsoft's "threats" to its competitors and partners violated Section 2.
The Department recognizes that among the practices the D.C. Circuit ruled unlawful was Microsoft's "attempt[s] to mislead and threaten software developers in order to contain and subvert Java middleware technologies that threatened Microsoft's operating system monopoly."35 Yet the PFJ does not prohibit Microsoft from misleading developers or, as it did with Java, creating supposedly "open" software development tools that, in reality, are compatible only with Windows. See Microsoft III, 253 F.3d at 77. These sorts of practices are added in the Litigating States remedy proposal.36 By preventing Microsoft from intentionally sabotaging competing applications or middleware products, and by requiring that if Microsoft implements open industry standards it not "pollute" those standards with proprietary, Windows-specific protocols and features, such relief would constrain the exclusionary conduct held unlawful by the D.C. Circuit. The Department's proposed settlement does not.
*****
The Department's claim that the decree "ends" Microsoft's unlawful practices is incorrect. It is also wrong as a matter of remedies jurisprudence. Antitrust courts must "start from the premise that an injunction against future violations is not adequate to protect the public interest."37 In order to prevent "a recurrence of the violation" found, antitrust courts are not limited to imposing "a simple proscription against the precise conduct [the violator] previously pursued." 38
Yet Assistant Attorney General James recently testified that the government's remedy proposal is "focused on the specific practices that the court [of appeals] had ruled unlawful."39 This focus on specific practices does not eliminate those practices. In any event, it is settled that antitrust relief may prohibit even otherwise lawful conduct if it "represents a reasonable method of eliminating the consequences of the illegal conduct" or preventing its resumption. 40
The proposed decree neither provides future middleware competitors with the API information needed to develop interoperable products nor opens the OEM distribution channel to effective competition from any such new entrants. To a surprisingly large degree, the PFJ's provisions simply memorialize Microsoft's current business practices. Indeed, the PFJ would not have thwarted Microsoft's 1995-98 unlawful campaign against Net. scape and Java had the decree been in place at that time.
As a consequence, the PFJ will discourage, rather than encourage, investment and innovation in new middleware technology. Future middleware competitors, faced with the very real prospect that they may not be able to obtain necessary API information from Microsoft or access to the OEM distribution channel, will have virtually no incentive to invest in time development of new and innovative middleware technology. Moreover, even if the PFJ actually did "creat[e] the opportunity for software developers and other computer industry participants to develop new middleware products that compete directly with Microsoft," as the CIS states, the five-year term of the proposed decree is far too short to promote innovation and investment in middleware technology. In short, under the PFJ the status quo that prompted the Department of Justice and State Attorneys General to bring these actions against Microsoft will perpetuate.
As the Supreme Court emphasized in its landmark ruling in the DuPont antitrust case, "It]he proper disposition of antitrust cases is obviously of great public importance, and their remedial phase, more often than not, is crucial. For the suit has been a futile exercise if the Government proves a violation but fails to secure a remedy adequate to redress it." United States v. E.I. du Pont de Nemours & Co., 366 U.S. 316, 323 (1961). Under any appropriate standard for judging the effectiveness of antitrust remedies, the key portions of the PFJ are just such an exercise in futility.
The Department proclaims that the API disclosure provisions of the proposed decree will create middleware competition by requiring Microsoft to disclose all of the interfaces and related technical information that Microsoft's middleware uses to intemperate with the Windows operating system." CIS, 66 Fed. Reg. at 59460. 41 That is simply not accomplished by a literal reading of the proposed decree's API provisions. The proposed decree does not provide middleware competitors with the information needed to intemperate, but rather allows Microsoft itself to decide whether, when and which APIs to release to potential competitors.
There are four provisions of the proposed decree that seek to address the issues of information disclosure for the purposes of enabling interoperability. Section III.D addresses the disclosure of APIs and Section III.E addresses the disclosure of communications protocols with server operating systems products. These provisions need to be read in concert with Section HI J, which substantially narrows the scope of required disclosures, and Section HI.L5, which potentially undermines the information disclosure regime by granting to Microsoft rights to insist on cross licenses to intellectual property developed through the use of Microsoft's APIs. Lastly, these provisions are dependent on a multitude of definitions which include Sections VI.A "APIs"; VI.B "Communications Protocol"; VI.E "Documentation"; VI.J "Microsoft Middleware"; VI.R "Timely Manner"; VI.T "'Trademarked"; and VI.U "Windows Operating System Product." To understand the impact of the PFJ on information disclosure, all these provisions must be read together, along with their subordinate definitions and exceptions.
The PFJ falls short of requiting the disclosure of APIs that innovative middleware technologies might need. Section III.D requires only that Microsoft disclose: "the APIs and related Documentation that are used by Microsoft Middleware to intemperate with a Windows Operating System Product." PFJ, 66 Fed. Reg. at 59454 (emphasis added).
This obligation is plainly too narrow to support real middleware competition. If a potential competitor creates a new form of middleware that provides innovative functionalities, it will not be entitled to the necessary APIs, if those APIs are not "used by Microsoft Middleware to interoperate with a Windows Operating System Product" within the scope of Section III.D. This necessarily limits future innovation to the parameters set by the breadth of Microsoft's Middleware functionality, it creates a regime where competitors must always follow, as opposed to lead, middleware innovations. For example, when Netscape was attempting to achieve full 38 interoperability with the Windows operating system in 1995, Netscape required the APIs for Windows, not merely the APIs between Windows and Microsoft's browser, which was just in the process of development.42
Further, under Section III.D, Microsoft must disclose "for the sole purpose of interoperating with a Windows Operating Systems Product... APIs and related documentation that are used by Microsoft Middleware to interoperate with a Windows Operating System Product." PFJ, 66 Fed. Reg. at 59454. Windows Operating Systems Products are defined in Section VI.U to include Windows 2000 Professional and Windows XP for the PC. Thus, Microsoft does not have to disclose APIs its middleware uses to interoperate with Microsoft operating systems on servers or handhelds. And for those APIs that Microsoft does disclose, Microsoft is permitted to limit their use by third parties "solely for the purpose of interoperating with a Windows Operating System Product." Id. at 59454. Thus, Microsoft can distribute middleware products that interoperate with all of its client and server operating systems along with its applications such as Office, while competitors' middleware products will be limited to using any disclosed APIs to intemperate only with PC versions of Windows. This limitation certainly does not provide a level playing field for competitive middleware.
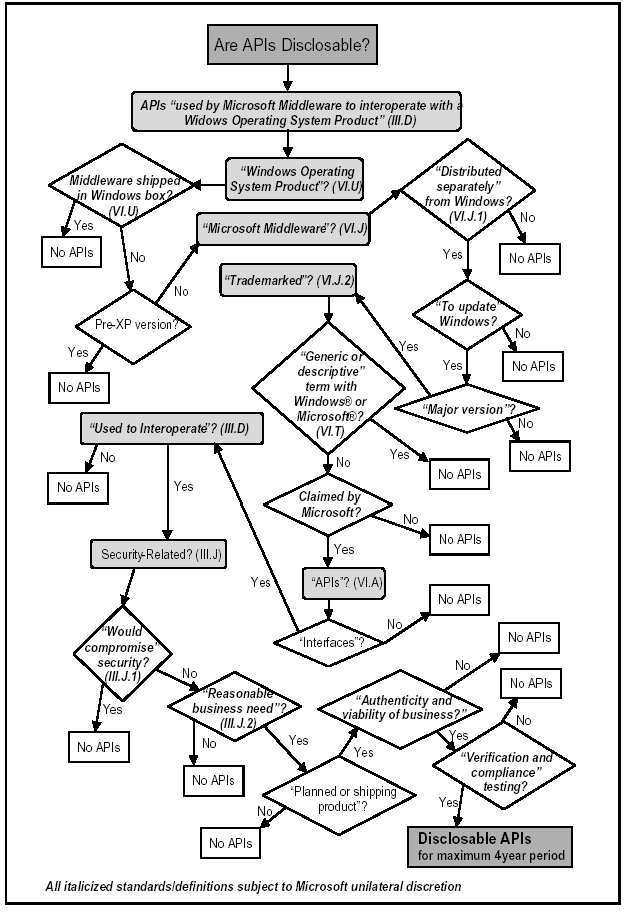
Close review of the plain language of the API disclosure provision and its subordinate definitions reveals that the provision is quite illusory. A careful examination of these complex provisions of the proposed decree -- represented graphically in Figure 1 on the next page reveals that, despite their length, they are nonetheless circular and illusory.
Figure 1
 [D] [D]
Section III.D sets forth the basic obligation that Microsoft must disclose to competitors "the APIs and related Documentation that are used by Microsoft Middleware to interoperate with a Windows Operating System Product." The PFJ therefore establishes a regime where Microsoft must disclose the "APIs," a defined tern, that are used by "Microsoft Middleware," a defined term, to intemperate with a "Windows Operating System Product," a defined term.
The defined terms within Section III.D reveal that the PFJ's API disclosure obligations are without substance. As stated, the provision calls for the disclosure of "APIs" between "Microsoft Middleware" and the "Windows Operating System Product." Taking those definitions in reverse order demonstrates that the Department cannot possibly predict precisely what information is required to be disclosed under Section III.D because most of the definitions are left to Microsoft.
First, Section VI.U provides the definition of a "Windows Operating System Product." A Windows Operating System Product is defined as:
The CIS explains that, pursuant to the proviso in the final sentence, this definition means that "the software code that comprises a Windows Operating System Product is determined by Microsoft's packaging decisions (i.e., by what it chooses to ship as 'Windows')." CIS, 66 Fed. Reg. At 59459. Under this approach, therefore, Microsoft retains the unilateral discretion to determine what constitutes Windows for purposes of its API disclosure obligations. If middleware software is included with Windows, it is thus part of a Windows Operating System Product for the purposes of this definition. It follows that if Microsoft chooses "at its sole discretion" to include middleware as part of Windows it escapes the disclosure requirements of Section III.D.
The other "bookend" of Microsoft's information disclosure requirement rests on definition VI.J, "Microsoft Middleware." First, it is critical to understand that provision III.D does not invoke definition VI.K "Microsoft Middleware Product," which clearly sets forth that "Internet Explorer, Microsoft's Java Virtual Machine, Windows Media Player, Windows Messenger, Outlook Express and their successors" are "'Microsoft Middleware Products." Id. Rather, the provision rests on the far more ambiguous definition of "Microsoft Middleware." Under definition VI.J, Microsoft Middleware means:
The weakness of this definition is immediately apparent. The first prong of the definition requires Microsoft middleware to be distributed "separately from a Windows Operating System Product." Therefore, if Microsoft decides to include middleware as part of Windows as it is entitled to do "in its sole discretion" it cannot possibly be Microsoft Middleware because it will not be "distributed separately." Alternatively, because middleware is "Microsoft Middleware" only if it is distributed "to update" Windows, Microsoft can as easily avoid any API disclosure obligations by distributing middleware as a separate application rather than as a Windows update.43
Second, in order to qualify as Microsoft Middleware, the middleware must also be "Trademarked." Section VI.T of the PFJ defines "'Trademarked" in two ways. The first clause of the definition states:
PFJ, 66 Fed. Reg. 59459.
We cannot fathom the rationale for resting the definition of Middleware on whether or not a particular technology is trademarked. The Department contends that the definition is "designed to ensure that the Microsoft Middleware ... that Microsoft distributes (either for free or for sale) to the market as commercial products are covered by the Proposed Final Judgment." CIS, 66 Fed. Reg. at 59465. Yet, again it appears that exactly the opposite is true based on the second part of the "Trademarked" definition, which states:
PFJ, 66 Fed. Reg. at 59459 (emphasis added).
Under this definition, if the product is distributed as "Windows® Media Player" as opposed to "Windows Media® Player" it would not be covered. That is because the formulation of the name "Windows® Media Player" would be "comprised of the ... [Windows®] trademarks together with a descriptive or generic term [Media Player]."
An analysis of each of Microsoft's Middleware Products demonstrates the problem. "Microsoft Internet Explorer" could easily be distributed as Microsoft® plus the generic or descriptive term "Internet Explorer" or "Windows Messenger" as Windows® plus the generic or descriptive term "Messenger." As a factual matter, "Microsoft Internet Explorer," "Microsoft Java Virtual Machine," "Windows Media Player" and. "Windows Messenger" are not currently distributed under either ® or TM nor are they registered with the United States Patent and Trademark Office. 44 Thus, in stark contrast to its purported effect, Section VI.T either currently excludes or provides a roadmap to exclude each of Microsoft's major Middleware Products from the disclosure requirements of III.D.
When the "Trademarked" provision is taken in conjunction with the additional requirement that the Middleware must be "distributed separately from a Windows Operating System Product to update that Windows Operating System Product," it is apparent that Microsoft can completely escape coverage under Definition VI.J by either altering its distribution or the nomenclature of its products. In sum, the set of "Microsoft Middleware" that interoperates with "Windows Operating System Products" appears to be a null set.
The final definition implicated by Provision III.D is that of "Application Programming Interfaces." "APIs" are defined in Definition VI.A as follows:
PFJ, 66 Fed. Reg. at 59458. (emphasis added). Thus, "interfaces" means "interfaces" because the basic API definition rests once on the Microsoft Middleware definition (described above) and three times on the definition of Windows Operating System Product, which is defined by Microsoft in its "sole discretion." The Department has proclaimed the API disclosure remedies to be the centerpiece of the PFJ. That the definition of "API" will be exclusively determined by Microsoft highlights the seriously flawed nature of the entire proposed device.
In sum, we do not believe it is possible for the Department of Justice, Microsoft or any party to know with any degree of certainty exactly what must be disclosed under Provision III.D. But there is no question that these definitional issues will be before the Court in numerous enforcement actions and dominate this Court's docket for the next five years.
Focusing on the terms of Provision III.D that are not defined yields some striking conclusions. First, the critical term "interoperate" is left undefined by the PFJ. Moreover, despite the Department's claim in the CIS that the decree's API provisions require the release of all "interfaces and related technical information," 45 these terms are neither defined nor employed in the language of Section III.D. In fact, the phrase "technical information" does not even appear in the proposed decree. In contrast, the Interim Order included a detailed definition of "Technical Information" (Section 7.dd) that the Department and Microsoft have without explanation eliminated from the proposed decree. 46 Inexplicably the PFJ has lowered the standard of interoperability supported by disclosed APIs in the Interim Order from information that software developers "require" to "interoperate effectively" with Windows to information "used by Microsoft" to "interoperate."
These terms are not peripheral. They go to the core meaning of the API disclosure provisions of the proposed decree. An injunction designed to require Microsoft to disclose interoperability information to rivals cannot possibly be effective where the scope of the information to be released is not defined with specificity. The elimination of the definition of Technical Information is thus particularly revealing, because it illustrates that the Department has crafted a remedy that is, at best, a subset of the Interim Order on which the Department claims it relied. It also demonstrates that the Department affirmatively made a determination not to define a term which was clearly central to the disclosures mandated by the Interim Order.
Finally, Section III.D does not ensure simultaneous API access for Microsoft and its competitors. While the Interim Order required disclosure of APIs at the same time they were made available to Microsoft applications developers, the PFJ does not. Instead, the proposed decree uses the very ambiguous standard that, for a "new major version" of Microsoft middleware, API disclosure "shall occur no later than the last major beta test release." PFJ, 66 Fed. Reg. at 59454. Yet "last major beta test release" is not defined, and the provision in any case begs the question of how to decide which beta release is the "last."
No less problematic are the requirements for timely disclosure of APIs exposed by new versions of Windows. Here, the proposed decree provides in Section III.D that for "a new version of a Windows Operating System Product," disclosure "shall occur in a Timely Manner." Here the definition of "Timely Manner" provides little, if any, protection for ISVs. Definition VI.R provides that Timely Manner is "the time Microsoft first releases a beta test version of a Windows Operating System Product that is distributed to 150,000 or more beta testers." We do not believe that Microsoft has ever had 150,000 "beta testers" as opposed to 150,000 "beta copies" of its new product. Regardless, all Microsoft has to do is limit distribution to 149,000 beta testers in order to frustrate the timeliness of the required disclosures.
The proposed decree also contains several broad exemptions from and preconditions to API disclosure by Microsoft. These provisions undermine whatever strength, if any, remains in Section III.D in light of the scope and definitional failings addressed above.
Section III.J of the PFJ exempts Microsoft from disclosing "portion of APIs or Documentation" related interface information "which would compromise the. security" of a "particular installation or group of installations" of any "anti-piracy, anti-virus, software licensing, digital rights management, encryption or authentication systems." 66 Fed. Reg. at 59455. These exceptions to API disclosure are extremely broad.
First, the scope of this provision implicates nearly all of Microsoft's Middleware products. For example, digital rights management is encompassed in all multimedia applications (e.g., Windows Media Player). Authentication is a function embedded in Windows software (e.g., Outlook Express and Microsoft Passport) and is required for access to Windows server operating systems. Encryption likewise is a technology that is used by Internet browsers (e.g., Internet Explorer) for e-commerce and by instant messaging middleware (e.g., Windows Messenger).
Second, because the Department acknowledges that this provision permits Microsoft to withhold from disclosure certain APIs, CIS, 66 Fed. Reg. at 59472, it must also acknowledge that this provision both narrows an already limited scope of disclosures and ensures that an alternative middleware product will never be fully interoperable in the same way as Microsoft's middleware.47
Third, the CIS either misstates the implications of the provision or the Department does not understand what was agreed to in the PFJ. For example, there is no such thing as an API that is relevant to a "particular installation [PC] or group of installations [network of PCs]." APIs are standard across all Windows installations. Moreover, the provision does not refer to "keys and tokens particular to a given installation" as stated in the CIS, 66 Fed. Reg. at 59472, but rather states that Microsoft may withhold "APIs ... the disclosure of which would compromise the security of a particular installation or group of installations ... including without limitation, keys, authorization tokens or enforcement criteria." PFJ, 66 Fed. Reg. at 59455. Therefore, the way the provision appears in the PFJ as opposed to the CIS, is that it is not limited to the user-specific security duties protecting specific computer networks that no one argument should be disclosed publicly.
Section III.J.2 also imposes onerous preconditions on ISVs for the receipt from Microsoft of APIs "related to" encryption, authentication and other security matters. In order to receive relevant APIs that relate to security technologies, competitors must meet a subjective standard of "reasonableness" which the decree appears to consign to Microsoft's discretion. Thus, an ISV is only entitled to the APIs if the competitor (1) "has a reasonable business need" for the information "for a planned or shipping product," (2) satisfies "reasonable, objective standards established by Microsoft" for "certifying the authenticity and viability of its business," and (3) submits its software for Microsoft testing to "ensure verification and compliance with Microsoft specifications for use of the API or interface."
None of these limitations seems appropriate, because they unduly rely on Microsoft to determine "reasonable business" need. As one example, Microsoft clearly views "open source" software, or a threat, but will no doubt continue to claim that it is not a "viable business".
The API section must also be read in conjunction with Section III.I of the proposed decree. This portion of the proposed decree contains a provision (Section III.5) that grants Microsoft the right to require ISVs and other API recipients to cross-license their own intellectual property back to Microsoft if it relates "to the exercise of their options or alternatives provided by this Final Judgment." PFJ, 66 Fed. Reg. at 59455. Under this approach, Microsoft can, at is own discretion, require that the products developed with APIs and related interface information -- for instance, a competing middleware program -- be licensed back to Microsoft, because they "relate[] to the exercise" of an ISV's "options or alternatives" under the proposed decree. That is not a new issue in the industry. For years Microsoft has attempted to extract cross-licensing requirements and most in the industry have successfully resisted. If this provision is exercised, Provision III.D will simply not be utilized if the result is a requirement that intellectual property resulting from competitors' own investments in software research and development. Again, the CIS purports to limit the plain meaning of Section III.I by opining that the intellectual property cross-licenses are only available if Microsoft "is required to disclose interfaces that might be used by others to support a similar feature in the same fashion." CIS, 66 Fed. Reg. at 59472. But that does not appear to be consistent with the language of the PFJ.
Finally, under Section III.D, the requirement for Microsoft to release APIs and Documentation to competitors does not commence for one year. This delay means that Microsoft's own middleware will continue to be preferred in terms of its interoperability with the Windows operating system. The one-year period in which competitors must wait for API releases is one-fifth of the decree's five-year term. Nothing in the CIS discusses or explains a rationale for this substantial delay.
The Competitive Impact Statement claims that the server provisions in Section III.E of the proposed decree will "prevent Microsoft from incorporating into its Windows Operating System Products features or functionality with which its own server software can intemperate, and then refusing to make available information about those features that non-Microsoft servers need in order to have the same opportunities to interoperate with the Windows Operating System Product."48 Like the decree's API disclosure provisions, this obligation is ephemeral.
First, Section III.E is designed only to support interoperability between Windows PCs and non-Windows servers. See CIS, 66 Fed. Reg. at 59469 (interoperability between "Windows Operating System Products and non-Microsoft servers on a network"). It expressly does not cover interoperability between Windows servers and non-Windows PCs. Thus, Apple, Linux and all other desktop operating systems competitors have no right under the proposed decree to obtain any of the technical information needed to allow PCs running such competing operating systems to intemperate with Windows servers.
Second, as with the API disclosure requirements, Microsoft can easily avoid Communications Protocol disclosure through product design. For example, Microsoft can implement protocols in other software on the desktop, such as Office, or from software it downloads over the Internet from its servers to its Windows Operating Systems Product rather than implementing those protocols directly in the Windows Operating Systems Product.49 Indeed, we understand that with Microsoft's new .Net offering, Microsoft plans to download code from the Internet to effect communications between clients and Microsoft's .Net servers. This will require no disclosure under Section III.E.
Third, the definition of "Communications Protocols" itself is extraordinarily ambiguous. The decree defines Communications Protocol in Section VI.B as:
PFJ, 66 Fed. Reg. 59458. This definition does not prescribe what "predefined tasks" are encompassed, and the phrase "format, semantics, sequencing, and error control of messages" can just as easily be read to apply only to the physical means of sending information to or from a server (the rules for transmitting information packets over a network) rather then the content of such information (the rules for structuring and interpreting information within such packets). Thus, Microsoft competitors wilt be able to learn how to construct messages that can be passed to or from Microsoft severs, but will not learn the substance of the information necessary to invoke the features and functionalities of the server.
Fourth, like the PFJ's API disclosure provisions, the key terms of Section III.E are undefined. We have addressed Windows Operating System Product, which allows Microsoft itself to define the term, above. The corresponding prong of Section III.E is that Communications Protocols are disclosable when used by a Windows Operating System Product to interoperate with "a Microsoft server operating system product." The CIS claims that
CIS, 66 Fed. Reg. at 59468-69. Amazingly, this term is nowhere defined in the PFJ, despite the fact that this language is what bounds the scope of Microsoft's obligation to disclose crucial information to rivals. Based on the plain language of the PFJ alone, there is no reason to believe that, for example, Internet Information Server is covered by the undefined PFJ term "server operating system product." Although the Department attempts to clarify this definition in the CIS, as noted above there is no reason to expect Microsoft to accept the Department's CIF definition.
Fifth, a large share of PC interactions with servers occur via the Interact browser. (For instance, all Web browsing, e-commerce and other Web functionalities are a result of the browser interoperating with a server.) Section III.E does not cover protocols that are implemented in Internet Explorer to support interoperability with Microsoft's server operating systems products. Therefore, Microsoft can easily evade the scope of this provision -- whatever that may be -- by incorporating proprietary interfaces and protocols into IE rather than Windows.
Sixth, the obligations of Section III.E appear to only apply to Communications Protocols that are "implemented ... on or after the date this Final Judgment is submitted to the Court." Read literally, all of the Communications Protocols built into Windows 2000 and Windows XP are exempt from disclosure because they were implemented before the proposed decree was submitted.
Finally, Section III.J constrains the Communications Protocol provisions of Section III.E in the same way it limits the API disclosure provisions of Section III.D. Thus, any Communications Protocols that "would compromise the security" of authentication, encryption or related technologies are exempt from disclosure. Because the heart of sever-based network interoperability is authentication and encryption, these exemptions once again swallow the rule.
For all these reasons, the decree's provisions for server interface information disclosure do not provide Microsoft competitors with the interface or protocol information necessary to enable interoperability between Windows PCs and non-Windows servers. Section III.E does not even cover interoperability between non-Windows PCs and Windows servers. The central terms establishing the scope of Microsoft's obligations are undefined and subject to Microsoft's unilateral control. In short, the PFJ has created another Venn Diagram with no intersecting circles, because the Communications Protocol provisions of the decree require nothing at all.
The Department explains that the personal computer manufacturer ("OEM") provisions of the proposed decree support "the ability for computer manufacturers and consumers to customize, without interference or reversal, their personal computers as to the middleware they install, use and feature." CIS, 66 Fed. Reg. at 59460, 59471. In reality, these measures hardly change anything in existing Microsoft-OEM relations, and do not appreciably alter the dynamics of the OEM distribution channel. Most important, Sections III.C and III.H cannot, by their very design, provide an opportunity for rival middleware products - as compared to Microsoft's middleware - to attract sufficient distribution to have any impact at all on the applications barrier to entry.
The OEM sections may actually make matters worse for middleware rivals. The PFJ limits what OEMs can remove from their PC products to just the middleware icons, euphemistically referred to as "access to" middleware in Sections III.C and III.H. In other words, OEMs are not permitted to remove the code for Microsoft Internet Explorer, Windows Media Player or any other Microsoft middleware, and the proposed decree allows Microsoft to commingle and integrate middleware with its Windows operating system software. The fact that the flexibility guaranteed to OEMs is limited to removing icons, and not the middleware itself, has major competitive significance and actually guarantees perpetuation of the applications barrier protecting Microsoft's operating systems monopoly.
To achieve its goal of "recreating the potential for the emergence" of middleware alternatives to Microsoft's monopoly operating system, the PFJ delegates the role of competitive gatekeepers to OEMs. Instead of requiting the monopolist itself to unfetter the market for entry by competitors, here the PFJ imposes that obligation on third-parties who are partners with, not competitors of, the defendant. If PC manufacturers do not act on the desktop flexibility powers provided by Sections III.C or III.H of the PFJ, there will, by definition, be no OEM-based remedy. Walter Mossberg, Personal Technology columnist for the Wall Street Journal, captured the problem elegantly. "Much" of the DOJ settlement, he explained, "pertains to the company's relations with the hapless makers of PCs, which aren't in any position to defy Microsoft."50
OEMs are captives of Microsoft for a number of reasons, beginning with the obvious fact that there are no commercially viable alternatives to the Windows operating system; there are no real alternatives to Microsoft's Office suite of personal productivity applications (Word Processing, Spreadsheets, E-Mail, etc.); and there is de minimis competition for Interact browsers. The fact that OEMs find themselves in a sole source relationship with the defendant provides Microsoft with innumerable avenues to exercise its leverage over the OEM channel. These complex relationships are built more on the subtleties of a sole source relationship than on written contracts, or overt retaliation, and thus are hardly resolved by the uniform Windows pricing obligation provided for in Section III.B.
It must also be understood that personal computer manufacturers are in the business of producing low margin commodity equipment, a business characterized by very minimal (and shrinking) R&D budgets. It is unrealistic to expect any Windows-centric OEM to develop, test, and pre-install packages of rival middleware, because that would require substantial expenditures in technical software expertise and customer support which would further narrow already shrinking profit margins in a business where competitors are currently engaged in a major price war to gain market share.
The financial burden of customer support, where a single end user service call can eliminate an OEM's profit margin on a PC, creates powerful disincentives to the inclusion of non-Microsoft middleware. See Microsoft III, 253 F.3d at 62. Judge Jackson found and the Court of Appeals affirmed that in light of their customer support obligations, which are "extremely expensive," Microsoft III, 253 F.3d at 61 (citing Findings of Fact ¶ 210), OEMs are disinclined to install multiple versions of middleware. Since OEMs "have a strong incentive to minimize costs," id., the customer confusion resulting from duplicative middleware is sufficient to preclude OEMs from installing competitive programs where comparable Microsoft middleware is included with Windows.
Under the proposed decree, however, these are precisely the circumstances faced by OEMs. There are no restrictions in the PFJ on Microsoft's ability to integrate middleware technologies into Windows; in fact Microsoft is allowed to do so at its "sole discretion." Even if an OEM wants to install a competitive non-Microsoft middleware program, it will be required to deal with the fact that the corresponding Microsoft middleware product is already present on its PCs, which it is not permitted to remove. Consequently, just as OEMs' cost minimization requirements forced them not to pre-install Netscape where IE was included with Windows, so too will these same profit pressures force OEMs to decline to install competing middleware programs under the PFJ.
This is in stark contrast to the provision of the Interim Order on which the Department claims to have based its settlement. Both the Interim Order and the remedy proposed by the Litigating States would require Microsoft to ship a version of the operating system without any middleware included, if requested by an OEM. That scheme makes it possible for an OEM to truly offer a differentiated product suite without the burden of having Microsoft's corresponding technology present on the system as well.
Even if they had an independent economic incentive to support middleware competition, however, Windows OEMs are still held captive under the proposed decree's retaliation provisions. Section III.A prohibits "retaliation" (another undefined term) by Microsoft against OEMs for developing, distributing or supporting competitive middleware or exercising their desktop icon flexibility rights.
Despite their relative length, the retaliation provisions do not at all effectively preclude retaliation. Retaliation is only prohibited under Section III.A where "it is known to Microsoft" that an OEM is undertaking a permitted, competitive action. This subjective, actual knowledge standard will be difficult if not impossible to enforce. In addition:
Section III.A also limits the prohibited forms of retaliation to "altering Microsoft's commercial relations with that OEM, or by withholding newly introduced forms of non-monetary Consideration (including but not limited to new versions of existing forms of non-monetary Consideration)." PFJ, 66 Fed. Reg. 59453. Microsoft is not precluded from denying new monetary consideration to OEMs as a means of retaliation, as that is neither an "alter[ed] commercial relation" nor a "newly introduced form of non-Monetary Consideration." Similarly, Microsoft can also reward compliant OEMs by providing concessions on license fees for non-Windows Microsoft software, including applications such as Office, server operating system software and server applications, as well as Microsoft Middleware Products. None of these types of software is covered by the pricing parity requirements of Section III.B, which apply only to "'Microsoft Operating System Products." Id.
Finally, as a general matter there is no practical way to identify and prohibit all the subtle ways Microsoft can preferentially favor some OEMs, and harm others, depending on their degree of support for Windows. For instance, the definition of Consideration in Section VI.C covets "product information" and "information about future plans." Id. at 59458. Yet Microsoft could retaliate against OEMs by denying them sufficient technical information regarding important, upcoming Windows features, for example by not inviting them to internal development conferences or presentations. Likewise, Microsoft could assign fewer or less knowledgeable technical support personnel to a specific OEM's account team, a form of retaliatory discrimination that would be difficult to detect and virtually impossible to prove.
In sum, the anti-retaliation provisions offer little shelter for OEMs desiring to respond to legitimate demands by their customers for choice among competing software products. If there is any doubt about this analysis of Sections III.C and III.H above, the Court should took no further than the OEMs' treatment of Microsoft Internet Explorer. On July 11, 2001 Microsoft announced that OEMs would be free to remove access to Internet Explorer, which they had previously been prohibited from doing.51 Since this announcement was made more than six months ago, not one OEM has actually taken advantage of this provision and removed the icon for Internet Explore from retail PCs This real-world market test is an accurate gauge of how many OEMs will likely take advantage of the exact same flexibility provided in Section III.H of the decree, albeit for a somewhat wider range of middleware products: none.
The core of the case against Microsoft rests on the theory that Netscape and Java provided an alternative development platform (middleware) for applications developers, which, if applications developers began writing applications to the middleware, would undermine the applications barrier to entry and thus Microsoft's Windows monopoly. For this to occur, developers need to view rival middleware as a more attractive development platform than Windows. Unfortunately, the PFJ provides a solution to the wrong problem and actually ensures that rival middleware applications will never be able to attract a critical mass of developers.
Sections III.C and III.H of the decree allow OEMs to install competing middleware and to "enable or remove access to" Microsoft Middleware Products from the desktop of Windows PCs that they sell to end users. However, as noted, these provisions do not authorize OEMs to delete the Microsoft middleware itself, and Microsoft is not prohibited from retaliating against OEMs that attempt to delete Microsoft middleware code from its configured PCs.
This distinction between icons and code is competitively decisive. The applications barrier exists because developers write to Windows-centric APIs. Under the terms of the decree, however, the APIs exposed by Microsoft middleware remain on every Windows PC even if OEMs and end-users exercise all of the flexibility provided by Section III.H. It is crucial to understand that an application developer can write to Microsoft middleware regardless of whether "access" to that software is removed. In other words, Microsoft's middleware APIs remain ubiquitously available on all Windows PCs under the proposed decree. The best a rival middleware provider can hope for is to be "carried" alongside Microsoft's middleware on some lesser portion of personal computers.
A critical lesson learned in this case is that, as with Netscape and Java, ubiquity trumps technology in network effects markets. Professor Arrow explains that no middleware competitor can expect any economically significant chance to compete on the merits if, as permitted under the decree, Microsoft middleware is ubiquitous. Arrow Decl. ¶ 26. The important distinction between icons and code was explained by the D.C. Court of Appeals in 1998. The court emphasized that removal of end user access "do[es] not remove the IE software code, which indeed continues to play a role in providing non-browser functionality for Windows. In fact, browser functionality itself persists, and can be summoned up by ... running any application (such as Quicken) that contains the code necessary to invoke the functionality." Microsoft II, 147 F.3d at 941.
Consequently, by limiting its effect to the removal of icons only, the proposed decree cannot achieve any appreciable effect in eroding the applications barrier. They cannot "recreate the potential for the emergence" of middleware alternatives in a way that provides an economically realistic opportunity for operating systems competition.
We explained above why it is unlikely that OEMs will expend resources to promote rival middleware products. The alternative model is that rival middleware providers would pay an OEM to feature its software and delete end-user access to Microsoft's middleware. This is consistent with the CIS, which explains that the function of the OEM provisions is to allow OEMs to "feature and promote" non-Microsoft middleware. CIS, 66 Fed. Reg. at 59460.
Section III.H does not achieve this goal, for two primary reasons. First, as detailed above, the "value" of the PC desktop is diminished by the fact that an OEM is not permitted to remove the Microsoft middleware code, and thus cannot offer a rival exclusivity.
Second, Section III.H.3 does not guarantee that a rival's middleware icon will even remain on the desktop. As the Department explains the theory of this remedy, it is to create a "marketplace" on the desktop where OEMs can "stand in the shoes" of consumers and exercise choices in which middleware technologies to feature based on price and performance. Yet, the PFJ permits Microsoft to "sweep" competing middleware icons placed on the Windows desktop by OEMs. That is, Windows may automatically remove the icons featured by an OEM just fourteen days "after the initial boot-up of a new Personal Computer." True, this section contains a proviso stating that Microsoft may not do so absent end user "confirmation," but neither the text of this provision nor the Competitive Impact Statement require that confirmation be based on any objective notice or alert by Microsoft. CIS, 66 Fed. Reg. at 59471.
The fourteen-day desktop sweep proviso directly contradicts the objective of fostering OEM flexibility to feature and promote non-Microsoft middleware, because it undermines the ability of OEMs to sell desktop placement an ISV can count on. Under Section III.H.5, the best an OEMs can offer is a guarantee of desktop placement for fourteen days.
This is critically important for the reasons stated above. As rival middleware vendors attempt to attract developers to write applications to their platforms, as opposed to Microsoft's platform, they will have to make representations as to how many PC desktops actually have the rival middleware installed and available to consumers. With the fourteen day "sweep" provision included in the PFJ, ISVs will simply not be able to make any accurate projections, which will further reduce the price they might be willing to pay for desktop placement.
In order to displace Microsoft middleware and encourage applications developers to write to their APIs, competing ISVs will need to differentiate their middleware products from Windows Media Player, Windows Messenger and the other Microsoft middleware products that are bundled with Windows. The OEM provisions affirmatively undermine the ability of ISVs to achieve any meaningful degree of product differentiation.
First, Section III.C.3 permits OEMs to launch automatically non-Microsoft middleware only at boot-up or upon making a connection to the Interact. This constrains the ability of manufacturers to configure competing middleware products and reduces the value of this flexibility for (and hence potential OEM revenues from) ISVs.
Second, auto-launch of competing middleware is permissible under Section III.C.3 only (a) "if a Microsoft Middleware Product that provides similar functionality would otherwise be launched automatically at that time," PFJ, 66 Fed. Reg. 59454, and (b) if the non-Microsoft Middleware "displays on the desktop no user interface or a user interface of similar size and shape to the user interface displayed by the corresponding Microsoft middleware product." d. These limitations allow Microsoft to gate middleware competition by reducing the role of non-Microsoft middleware to only those instances in which Microsoft's own products are launched. If Microsoft decides that its middleware products will not have a user interface, or will utilize a window of a specific size, those decisions are binding on competitors' product designs as well. Indeed, the PFJ surprisingly appears not even to contemplate a situation where Microsoft's competitors develop a middleware product for which there is no "corresponding" Microsoft middleware.
Third, the PFJ empowers Microsoft to limit the freedom of ISVs in their product design and functionality decisions on its competitors. Microsoft can also limit the placement of icons and shortcuts may appear on the desktop and elsewhere, id. at 59454, 59455, the "functionality" of middleware products whose icons and shortcuts may be included by the OEM, and the ability of end users to designate non-Microsoft middleware as default middleware on their computers. Id. at 59455.
Each of these provisions has a similar, substantial effect. By allowing middleware to be substituted by an OEM only when (a) it performs similarly to Microsoft middleware, (b) exhibits functionality defined by Microsoft, or (c) includes the same user interface as Microsoft middleware, the PFJ allows Microsoft to "gate" competition. There is no competitive justification for these provisos, all of which serve to eliminate opportunities for product differentiation and permit Microsoft to constrain middleware competition to the scope, location and even "look and feel" it determines for its own products.
Section III.H of the proposed decree allows Microsoft twelve months to modify Windows XP in order to permit OEMs to remove Microsoft middleware icons or change default settings for invoking middleware functionalities. Yet the modification necessary to allow removal of icons via the "Add/Remove Programs" utility is a trivial exercise. Demonstrable proof of this fact is that Microsoft was able to modify the beta version of Windows XP to permit removal of the Interact Explorer icon within weeks of its July 11, 2001 announcement. We can not fathom why Microsoft is now given twelve months to accomplish the same task.
Section VI.N of the decree also provides that a "Non-Microsoft Middleware Product" is software with certain functionalities "of which at least one million copies were distributed in the United States within the previous year." Because the Section III.H obligations requiring modification of Windows XP to permit addition and removal of competing middleware apply to "Non-Microsoft Middleware Products," OEMs are foreclosed from the ability to feature and promote small middleware start-up competitors in Windows XP, Section VLN is a very veal impediment to achievement of the innovative middleware market the PFJ is purportedly designed to promote.
Sections III.C and III.H also do not apply to Microsoft's Java Virtual Machine ("JVM"), or Microsoft's equivalent of the JVM, its Common Language Runtime. Despite the fact that the "Microsoft Middleware Product" definition includes the Microsoft Java Virtual Machine, it appears there is no competitive consequence to its inclusion in this definition in any of the provisions of the decree. First, Microsoft no longer ships its JVM with Windows, so there is nothing for OEMs to remove. Second, even if they did continue to ship a JVM, there is no "icon" or "end-user access" to Java. Rather, Java is invoked automatically by programs that rely on its presence.
Users today enjoy the flexibility - without the benefit of the PFJ - to add, delete or customize their own PC desktops. Users may delete icons by simply "dragging" the icon to the "recycle bin" or "right-clicking" on the icon and simply choosing "delete."
Thus, the decree's OEM provisions allowing OEM removal of icons only codify Microsoft's current business practices. In response to the Court of Appeals' opinion, Microsoft on July 11, 2001 announced that "it is offering computer manufacturers greater flexibility in configuring desktop versions of the Windows operating system in light of the recent ruling by the U.S. Court of Appeals for the District of Columbia."52 According to the Microsoft press release, under this policy OEMs can "remove the Start menu entries and icons that provide end users with access to the Interact Explorer components of the operating system," and "Microsoft will include Internet Explorer in the Add/Remove programs feature in Windows XP." Id. Thus, Microsoft stressed that "Microsoft has always made it easy for consumers to delete the icons for Interact Explorer, but will now offer consumers this additional option in Windows XP." Id.
This announcement is revealing because it confirms, from Microsoft itself, that the "flexibility" provided to end users by Section III.H of the decree has always existed. And by revising Windows XP to permit OEMs to remove the Interact Explorer icon, Microsoft has already done precisely what the decree requires. Thus, the OEM provisions of the decree succeed mostly in codifying Microsoft's current business practices and achieve minimal, if any, remedial purpose.
In sum, the relief provided by Sections III.C and III.H is fundamentally at odds with the theory of the case. These OEM "desktop" remedies will not provide any opportunity for alternative middleware platforms to attract developers and thus to challenge the applications barrier to entry. They are economically irrational since Microsoft's middleware will continue to be ubiquitously available on all PCs, regardless of the choices exercised by OEMs. These provisions allow Microsoft to dictate product design features to its rivals, to limit product differentiation and to restrict OEM deals with rivals to a brief, fourteen-day exclusivity period. And at bottom, they cannot change the economic structure of the PC distribution channel because OEMs are sole-source partners of Microsoft, not competitors.
Although the proposed decree purports to ban exclusive dealing by Microsoft with respect to Windows software, Section III.G expressly permits Microsoft to establish favored or exclusive relations with certain OEMs, ISVs, etc., if the parties enter into "any bona fide joint venture or ... any joint development or joint services arrangement." This exception all but vitiates the supposed prohibition, for it allows Microsoft to enter into the identical distribution agreements that were held unlawful at trial merely by denoting them as "joint" activities.
The Department recognizes explicitly that relief in this case must "`ensure that there remain no practices likely to result in monopolization in the future.'" Microsoft III, 253 F.3d at 103 (citations omitted); see CIS, 66 Fed. Reg. at 59465 (monopolization remedy should "avoid a recurrence of the violation" in the future). Yet by failing to address significant market and technological developments that have occurred in the period since the trial record closed, the narrow remedies of the proposed decree do not provide relief that comes even close to ensuring that Microsoft's unlawful practices will not be repeated in the future.
Since the trial, Microsoft has solidified three new chokeholds with which it can easily perpetuate its monopoly power:
-
-
-
-
-
- The Decree Does Not "Undo" the Competitive Harm Resulting from Microsoft's Anticompetitive Practices
In this case, Microsoft early on recognized middleware as the Trojan horse that, once having, in effect, infiltrated the applications barrier to entry, could enable rival operating systems to compete .... Alerted to this threat, Microsoft strove over a period of approximately four years to prevent middleware technologies from fostering the development of enough full-feature, cross-platform applications to erode the applications barrier to entry.
-
- The Proposed Settlement Fails to Deny Microsoft the Ill-gotten Fruits as Required by Established Antitrust Law
-
- The Decree Does Not Terminate or Redress Numerous Practices that the Court of Appeals Found to Violate the Sherman Act
-
-
- Integration of Windows and Middleware
-
-
- Coercion and Market Allocation
-
-
- Deception and Product Sabotage
-
-
- The Proposed Decree's Provisions for Information Disclosure Do Not Assure that Future Middleware Competitors Will Have Access to Necessary Interoperability Information
-
-
- The API Provision's Scope is Far Too Narrow.
-
-
- The API Provision of the PFJ Constructs an Illusive Framework for Disclosure of Interoperability Information
-
-
-
- Defined Terms Within the API Disclosure Provision Leave All Material Disclosure Determinations to Microsoft.
the software code (as opposed to source code) distributed commercially by Microsoft for use with Personal Computers as Windows 2000 Professional, Windows XP Home, Windows XP Professional, and successors to the foregoing, including the Personal Computer versions of the products currently code named "Longhorn" and "Blackcomb" and their successors, including upgrades, bug fixes, service packs, etc. The software code that comprises a Windows Operating System Product shall be determined by Microsoft in its sole discretion. (emphasis added)
software code that
- Microsoft distributes separately from a Windows Operating System Product to update that Windows Operating System Product;
- Is Trademarked;
- Provides the same or substantially similar functionality as a Microsoft Middleware Product; and
- Includes at least the software code that controls most or all of the user interface elements of that Microsoft Middleware.
Software code described as part of, and distributed separately to update, a Microsoft Middleware Product shall not be deemed Microsoft Middleware unless identified as a new major version of that Microsoft Middleware Product. A major version shall be identified by a whole number or by a number with just a single digit to the right of the decimal point.
"Trademarked" means distributed in commerce and identified as distributed by a name other than Microsoft® or Windows® that Microsoft has claimed as a trademark or service mark by (i) marking the name with trademark notices, such as ® or TM, in connection with a product distributed in the United States; (ii) filing an application for trademark protection for the name in the United States Patent and trademark Office; or (iii) asserting the name as a trademark in the Unites States in a demand letter or lawsuit.
Any product distributed under descriptive or generic terms or a name comprised of the Microsoft® or Windows® trademarks together with descriptive or generic terms shall not be Trademarked as that term is used in this Final Judgment. Microsoft hereby disclaims any trademark fights in such descriptive or generic terms apart from the Microsoft® or Windows® trademarks and hereby abandons any such rights it may acquire in the future.
the interfaces, including any associated callback interfaces, that Microsoft Middleware running on a Windows Operating System Product uses to call upon that Windows Operating System Product in order to obtain any services from that Windows Operating System Product.
-
-
- The API Disclosure Provision Also Leaves Critical Terms Undefined.
-
-
- Under Provision III.D, APIs Will Never be disclosed in a Timely Manner
-
-
- The Exceptions from and Preconditions to API Disclosure Further Narrow the Scope of an Already Unworkable Disclosure Provision
-
-
- Cross-Licensing of Middleware APIs
-
-
- Timing of API Disclosure Obligation
-
- The Communications Protocol Provisions of the Decree Do Not Require Release of any Server APIs and are Based on Terms the Department Failed to Include in the Settlement
the set of rules for information exchange to accomplish predefined tasks between a Windows Operating System Product and a server operating system product connected via a network, including, but not limited to, a local area network, a wide area network or the Internet. These rules govern the format, semantics, timing, sequencing, and error control of messages exchanged over a network.
[t]he term "server operating system product" includes, but is not limited to, the entire Windows 2000 Server product families and any successors. All software code that is identified as being incorporated within a Microsoft server operating system and/or is distributed with the server operating system (whether or not its installation is optional or is subject to supplemental license agreements) is encompassed by the term. For example, a number of server software products and functionality, including Internet Information Server (a "web server") and ActiveDirectory (a "directory server"), are included in the commercial distributions of most versions of Windows 2000 Server and fall within the ambit of "server operating system product."
-
- The Proposed Decree's Provisions for OEM Flexibility Do Not Open the PC Manufacturing Channel to Future Middleware Competitors
-
-
- The OEM Provisions Place Sole Responsibility for Introducing Middleware Competition on PC Manufacturers
- Microsoft is not prohibited from retaliating if an OEM removes the code for a Microsoft Middleware Product from its retail PCs.
- Nor does this provision prevent retaliation if an OEM removes either icons or code for Microsoft software that does not qualify as a "Microsoft Middleware Product" (for instance, Microsoft Movie Maker).
- And Microsoft is not prohibited from retaliating against OEMs for promoting products that fall outside of the Section III.A terms. By way of example, Microsoft could retaliate against OEMs for promoting non-Microsoft Internet services, server operating systems, server middleware or server applications. Microsoft could even retaliate against OEMs for distributing or promoting middleware that does not yet compete with Microsoft Middleware Products.
-
-
- The Provisions Allowing OEM Flexibility Do Not Address the Key Issue of Microsoft's Ubiquitous Middleware Development Platform
-
-
- The OEM Provisions Do Not Create a Level Playing Field for Middleware Desktop Competition
-
-
- Additional OEM Provisions Further Undermine the Crucial Ability of ISVs to Differentiate Competing Middleware Products
-
-
- The OEM Provisions Contain Other Superfluous Terms that Substantially Limit Any Potential Market Impact
-
-
.
- The OEM Provisions Have No Impact on Java
-
-
- The OEM Provisions Largely Codify Microsoft's Existing Business Practices.
-
- The Proposed Decree Does Not Effectively Preclude Microsoft's Exclusive Dealings
-
- Current Market and Economic Realities Demonstrate that the PFJ is Incapable of Having Any Substantial Procompetitive Impact
-
-
- New Monopolies Enable Microsoft to Protect its Operating System Monopoly Despite the PFJ
However, the PFJ does not require the disclosure of APIs exposed by IE, Office the low-end server operating systems. Microsoft can develop middleware programs that utilize these APIs -- which are as ubiquitous as the Windows APIs themselves -- and thus evade the API disclosure provisions of the PFJ. Similarly, although Section III.E of the PFJ requires the disclosure of Communications Protocols used for interoperability with Microsoft server operating systems, by controlling the client (IE), Microsoft can control the server irrespective of these provisions.54 That is, Microsoft's monopoly control over IE allows it unilaterally to implement proprietary standards and protocols within IE, that are not disclosable under the PFJ because they are not "implemented in a Windows Operating System Product installed on a client computer" within the scope of Section III.E.
The primary competitive threat to the Windows OS/IE platform is the emergence of applications and services provided over the Internet, where the application or service is independent of the computing platform employed by the user. The recent spread of high-speed Internet service has further spurred the development of this category of distributed applications or web services that take advantage of Internet's underlying architecture.
Two features of distributed applications in particular constitute a revolutionary change from the previous "client-server" model. First, rather than residing principally on one machine (either a client or a server), distributed applications effectively reside on the network itself. It is therefore possible to access these services from any computer or device connected to the Internet. From the user's perspective, although the application itself resides on the network, it is accessible as rapidly and seamlessly as if it resided on the user's own PC.
Second, because the applications and data are accessible from different machines, access to these services depends critically upon being able to establish the identity of the user seeking access to those services. Web identity and authentication services accordingly take on extraordinary importance in the world of distributed applications.
These changes in the market reveal a picture of today's PC industry that is radically different from the Department's placid vision of "recreating the potential" for middleware competition by opening the OEM channel to possible future middleware innovations. The critical question, however, is whether distributed web-based applications, which do not need to be compliant with any particular operating system, will be able to remain independent of Windows and in the process bring down the applications barrier to entry.
The PFJ does not protect the Internet-based competition for the Windows operating systems monopoly in the future because the proposed decree does nothing to prevent Microsoft from continuing to shift from one anticompetitive activity to another in order to maintain its monopoly. Instead of bundling middleware code into Windows and creating exclusive dealing arrangements with ISVs and OEMs, Microsoft today is attempting to defeat the threat from Web-based services by bundling its Web services technologies into Windows and entering into exclusive vertical distribution arrangements with Web-based content and e-commerce providers. See Passport to Monopoly: Windows XP, Passport, and the Emerging World of Distributed Applications at 25 (ProComp June 21, 2001) and Microsoft's Expanding Monopolies: Casting A Wider .Net (ProComp May 15, 2001).
As would be expected, Microsoft now attempts to create a proprietary equivalent to the distributed applications paradigm by bundling its latest operating system with certain applications and technologies in order to secure dominance in distributed applications. For example, Microsoft Passport, a proprietary authentication technology built on the .NET Framework, is bundled with Windows XP. This bundling allows Microsoft's own authentication services to have a ubiquitous distribution base -- and deny rival technologies ubiquity -- in the same way that its bundling practices extinguished the middleware threats from Netscape and Java. A monopoly in web identity services will enable Microsoft to control the means by which users access distributed applications from the Internet. Nonetheless, the PFJ does nothing to restrict Microsoft's practices in this area. The API disclosure provisions only mandate the release (if at all) of APIs used by a Microsoft Operating System product to interoperate with Microsoft Middleware, which excludes Passport.
Similarly, Microsoft's broader .NET initiative is replacement of the Java and Netscape technologies that it unlawfully crippled with Microsoft proprietary technology. Microsoft defines .NET as its "platform for XML web services."55 The services which .NET offers are a combination of pre-designed applications, some of which come under the rubric "Hailstorm," and a set of tools, under the rubric of Visual Studio Integration Program, designed to allow developers to create web applications which rely on the all-important APIs exposed by Microsoft programs. At the core of .NET stands the Common Language Runtime environment ("CLR"). CLR is Microsoft's answer to the Java runtime environment, with a key difference. CLR provides the developer with a device that is similar to the JVM, but that lacks the element so destructive to Microsoft's hegemony--freedom from reliance on Microsoft's APIs. Of course, CLR will take full advantage of Microsoft's vast distribution network via bundling with future versions of Windows (including Windows XP) as well as with IE and Microsoft Network.
Microsoft's monopolization strategy has not changed at all. Bill Gates has explained that "there's a very strong analogy here between what we're doing now [with Web-based services] and what we did with Windows."56 Since Microsoft will pursue the same tactics and strategies found unlawful in the instant case, any remedy that does not prohibit a repeat of these practices in new markets and new contexts is facially flawed.
In sum, the proposed decree fails to address identifiable market and technological developments since the trial record closed that allow Microsoft both to protect its operating systems monopoly against current potential rivals and to engage in the same types of conduct adjudged unlawful by the Court of Appeals. Consequently, the proposed decree does not and cannot "ensure that there remain no practices likely to result in monopolization in the future," Microsoft III, 253 F.3d at 103 (citations omitted), and must be rejected by this Court.
The proposed settlement not only does not achieve the procompetitive effects that the Department claims, it increases Microsoft's dominance of the operating systems market and actually worsens competitive conditions across the entire software industry. Among other things, the proposed decree rewards Microsoft for its illegalities, promoting future defiance of antitrust laws and intransigent tactics by dominant firms. Many of the deficiencies of the proposed decree have been outlined in this submission. These deficiencies will allow Microsoft to perpetuate its monopoly position. In addition, the decree represents a step back from the current state of affairs notably because it sanctions continued bundling or commingling by Microsoft of middleware technologies with Windows, thus increasing rather than decreasing Microsoft's power to sustain the applications barrier to entry protecting its operating systems monopoly while disadvantaging non-Microsoft middleware providers. By enhancing Microsoft's ability to buttress the applications barrier to entry, the proposed settlement harms competition, and increases, rather than terminates, Microsoft's monopoly power.
One appropriate measure for assessing whether the PFJ is adequate is whether it would preclude today the same conduct Microsoft used to foreclose Netscape and Java, and thus preserve its monopoly power, in 1995-98. It would not.
As a fundamental matter, this is because Microsoft is not required to disclose the APIs needed for new and innovative forms of middleware. When Netscape was launched in late 1994, Microsoft did not have an Internet browser and was focused on Chairman Gates' vision of interactive television, rather than the Internet. Thus, there were no APIs exposed by Windows that were "used by Microsoft Middleware to interoperate" within the scope of Section III.D of the proposed decree. Had the decree been in place when Jim Barksdale, former CEO of Netscape, met with Microsoft in 1995, Netscape would not have been entitled to APIs or any other interoperability information under the express terms of the decree. "For the same reasons, no interoperability information would have been disclosable to Sun in order to enable interoperability of Java runtime technology with Windows.
Most of the distribution tactics Microsoft used to cut off Netscape's air supply and to "pollute the market for cross-platform Java" are also permissible under the decree. Microsoft can still force OEMs to take its own middleware through bundling. Microsoft can still coerce or threaten partners like Intel and rivals like Apple and can still refuse to port its monopoly Office suite in order to protect the applications barrier to entry. Microsoft can still throttle middleware innovations because the PFJ gives it the ability to "gate" the functionality and product design of rival middleware products. Microsoft can still prohibit OEMs from removing its middleware, or applications, and is free to retaliate against OEMs that do so. Microsoft can still deceive middleware developers and can still introduce application development tools that pollute open standards by producing only Windows-compatible programs. And Microsoft can still protect the applications barrier by utilizing the very same practices through its monopoly IE and Office products that the PFJ purportedly outlaws for Windows.
In short, the PFJ does not even foreclose the means of foreclosure that were proved at trial and affirmed by the Court of Appeals. Under any Tunney Act standard of review, it must be rejected.
The proposed decree is fiddled with ambiguities and loopholes and grants unilateral, essentially unreviewable, power to Microsoft to define the scope of its own ambiguous obligations. As such, the PFJ is an illusory contract, and unenforceable as a matter of well-settled contract law.
As the Court emphasized in Microsoft I, a proposed settlement cannot be entered, at least without substantive modification, if it is ambiguous or if there are "foresee[able] difficulties in implementation." 56 F.3d at 1462. The proposed decree here is the epitome of such a case.
Twenty-four different sections of the PFJ provide that specific actions by Microsoft, or standards for assessing whether its practices are permissible, must be "reasonable."57 In a decree purportedly drafted to provide a "certain" remedy, this is anything but. As just two examples, in addition to the reasonable scope of "bona fide," exclusive joint ventures discussed in the preceding section, Microsoft is expressly permitted to adopt "reasonable technical requirements" on which to override an OEM's or end user's choice of non-Microsoft middleware (Section III.H) and to enter into concerted refusals to deal with ISVs -- requiring them not to develop software for competing platforms -- that are "of reasonable scope and duration" (Section III.F.2). Consent decrees are interpreted as contracts, and it is black letter contract law that illusory contracts, those that give one party the fight to decide the scope of its own obligations, are not enforceable. See Rest. Contracts 2d . 77.
The judge in the first instance for all of these reasonableness clauses is Microsoft itself. In short, it is difficult to conceive of a more loosely drafted decree than the PFJ, which allows the defendant, without any practical constraint except lengthy contempt proceedings, to establish unilaterally the extent of its own decree obligations. Due to the inherent ambiguity in "reasonableness" terms, these disputes will be complex, tedious and time-consuming exercises for the Court.
The "Technical Committee" and so-called "Crown Jewel" provisions are equally inefficacious. The Technical Committee ("TC") established by Section IV.B of the proposed decree does not help enforcement matters appreciably. Most significantly, nothing that the Technical Committee does is binding and nothing that it investigates, analyzes or recommends is permitted to see the light of day. The TC reports only to the plaintiffs (Section IV.B.8.e) and "all information" gathered by the TC is subject to confidentiality and non-disclosure agreements and a protective order (Section IV.B.9). The members of the TC may "communicate" with third-parties, but only about "how their complaints or inquiries might be resolved with Microsoft" (Section IV.B.8.g). Furthermore, "[n]o work product, findings or recommendations by the TC may be admitted in any enforcement proceeding before the Court for any purpose, and no member of the TC shall testify by deposition, in court or before any other tribunal regarding any matter related to the decree" (Section IV.D.4.d).
Rather than a vehicle for prompt resolution of enforcement disputes, the TC provisions are a charter for delay and obfuscation. By denying the Court any access -- whether or not in camera -- to the work product of the TC, the proposed decree simply creates another hoop through which third-party complainants, and the government itself, must pass in order to enforce violations of the decree b5, the defendant It also denies the Court the benefit of the unbiased, objective technical expertise of the TC, which is the principal criterion on which its members are to be selected. Coupled with the sheer number of "reasonableness" provisions in the decree itself, the TC process will therefore delay enforcement and make clean resolution of decree interpretation issues more costly and burdensome for all affected parties and non-parties.
Finally, Section V.B of the PFJ provides that if the Court finds Microsoft "has engaged in a pattern of willful and systematic violations," on application of the plaintiffs a "one-time extension" of the decree may be granted, for up to two years. Although presented as a "Crown Jewel" provision, this section does little to ensure compliance. The function of a Crown Jewel clause is to provide such an onerous penalty that the defendant's compliance with its substantive obligations can be coerced, and deliberate evasion avoided, without ever having to invoke the penalty. Here, the "threat" Microsoft is being presented with is that of being forced for two more years to decide at its "sole discretion" what constitutes Windows, to constrain exclusive joint ventures to "reasonable" duration, to gain access to intellectual property developed by middleware competitors, and to dictate to those competitors the functionality and user interface of their products. This is plainly something Microsoft should welcome with open arms rather than fear.
The vagueness of the terms, the ineffectiveness of the Technical Committee and the lack of a meaningful deterrent Crown Jewel provision will plague the courts for years to come. In the absence of any deterrent, Microsoft will no doubt interpret the "reasonableness" standards generously incorporated in the proposed settlement in its own favor. The enforcement agencies and numerous competitors will witness the ill effects of future Microsoft actions and challenge these practices. However, without the proper dispute resolution mechanisms in place, it will be up to the courts to resolve all these "reasonableness" issues arising out of the proposed settlement.
ProComp and its members have consistently supported structural relief in this case. In our view, divestiture remains the most effective remedy for Microsoft's wide-ranging unlawful practices. Conduct remedies like the proposed decree are a second-best solution, because they rely on the defendants good will to comply. An injunctive decree in a Section 2 monopolization case "does no more than encourage the monopolist to look for some new way of exercising its dominance that is not covered by the current injunction." 58 Comprehensive behavioral decrees inevitably require interpretation and application as the defendant introduces new products, moves into new markets, or changes its business strategies in its traditional markets.
That does not mean, however, that conduct remedies will necessarily be ineffective here, but rather that they must be targeted and broad enough to redress the core practices used to maintain Microsoft's monopoly and to eliminate the barriers to entry protecting that monopoly power. The proposed decree does not even purport to satisfy this goal, which we submit is compelled by the Ford/United Shoe standard required for assessing relief in this case.
The relief proposed by the Litigating States achieves these objectives. We respectfully submit that the Court adopt a crown jewel divestiture provision to deter Microsoft from engaging in further unlawful conduct.
There are several circumstances in which it is established that district courts must engage in rigorous scrutiny of proposed antitrust settlements under the Tunney Act. This case epitomizes those circumstances. If ever there was a case in which a full, independent judicial assessment should be conducted, it is this one.
Even in the pretrial context with its more limited review, Tunney Act courts will rigorously scrutinize proposed settlements when an antitrust case is complex, subject to considerable controversy, and affects large segments of the public.59 Especially rigorous scrutiny is also undertaken when the proposed decree departs substantially from the relief sought in the government's complaint,60 or otherwise represents a sharp reversal in the government's prior position. 61 Each of these situations is present in this case
This is certainly a highly complex case that has preoccupied the political, technology and business communities for years. These are precisely the circumstances in which the Tunney Act's genesis reveals a major policy concern with the appearance of the government settling for too little "because of the powerful influence of antitrust defendants and the complexity and importance of antitrust litigation." SENATE REPORT, supra, at 147 (statement of Judge J. Skelly Wright).
Microsoft plainly "wield[s] great influence and power" and has brought "significant pressure to bear on [the] Government" throughout the litigation. Id. Thus, the Court needs to consider whether this is a case, such as Cascade, where the Department "knuckled under" to an economically and politically powerful antitrust defendant. Cascade Natural Gas Corp. v. El Paso Natural Gas Co., 386 U.S. 129, 136, 142 (1967). 62
Courts have also refused to enter proposed antitrust consent decrees where the Government or the defendant did not comply with its procedural responsibilities under the Tunney Act. Even technical and formalistic failures have been deemed grounds to deny entry of a proposed judgment. United States v. Central Contracting Co., 527 F. Supp. 1101 (E.D. Va. 1981).
The procedural irregularities in this case are far greater, and are of substantive importance to the Court's review. First, the Tunney Act requires the Department to provide an explanation of "alternatives" to the proposed decree considered in evaluating a settlement proposal. 15 U.S.C. § 16(b)(6). Here, however, the Department simply offers a laundry list of other conduct remedies proposed by third-parties, dismissing all of them collectively with the terse statement that the PFJ "provide[s] the most effective and certain relief in the most timely manner." CIS, 66 Fed. Reg. at 59475. The Department's assertion is unexplained.
The CIS recites only that the Department considered intervening changes "in the computer industry, as well as the decision of the Court of Appeals, which reversed certain of the District Court's liability findings."63 Nothing in the CIS offers any useful guidance to the Court, or the public, as to why the rejected conduct remedies are inappropriate; thus, the Department fails to come forward with the "detailed notice to the public" the Tunney Act was intended to require.64 This violates the Government's duty not just to "describe" the alternatives (which the CIS does), but also to provide an "explanation" of their adequacy (which the CIS does not). This is an improperly narrow view of the government's Tunney Act responsibilities is incompatible with the purpose of the Tunney Act to ensure that all relevant issues are subject to maximum "ventilation."65
The government's "predictive judgments" about market structure and competitive effect should be accorded a presumption of regularity, Microsoft I, 56 F.3d at 1460 (quoting United States v. Western Elec. Co., 993 F.2d 1572, 1577 (D.C. Cir.), cert. denied 510 U.S. 984 (1993), but only when tile circumstances are regular. Where, as here, the Department's exposition of the reasons for its settlement and its legal interpretation of the Court of Appeals' mandate are woefully lacking, such a presumption of regularity should not apply. In these circumstances, the Court cannot "carefully consider the explanations of the government in the competitive impact statement." CIS, 66 Fed. Reg. at 59476 (citation omitted).
Second, the Tunney Act mandates that the government make available all "materials and documents which the [it] considered determinative in formulating [a settlement] proposal." 15 U.S.C. . 16(b). The CIS responds to this requirement with a blanket statement that
CIS, 66 Fed. Reg. at 59476. That cannot be accurate. Even in antitrust cases that are not the length and complexity of the Microsoft litigation, courts have found similar disclaimers "to be almost incredible." Central Contracting Co., 527 F. Supp. at 1104. It defies credulity to suggest that there does not exist even one document, memorandum or analysis that the Department considered "determinative" in selecting the relief package presented to this Court.
Third, the CIS misstates many provisions of the PFJ. We address these in detail in Section III above, and will not repeat that analysis here. Where, as here, the government presents a document that seeks to justify provisions that on close examination arc illusory, it has in effect challenged the legitimacy of statute. Under even the strictest interpretations of Tunney Act deference, this Court cannot permit the Tunney Act process to "make a mockery of judicial power." Microsoft I, 56 F.3d at 1462.
Fourth, the Tunney Act requires that the defendant file a list of "all" written or oral communications "by or on behalf of such defendant ... with any officer or employee of the United States concerning or relevant to such proposal, except [for] communications made by counsel of record alone with the Attorney General or the employees of the Department of Justice alone." 15 U.S.C. § 16(g). Remarkably, Microsoft's Section 16(g) filing indicates that only two such communications occurred, both in connection with negotiations together with Microsoft and the Court-appointed mediator. This cannot be true It has been publicly confirmed by numerous public officials, and acknowledged by Microsoft, that a large number of Microsoft-retained lawyers and lobbyists have advocated its position on this case before countless officials in Congress and the Executive Branch. The Court should require Microsoft to fully comply with Section 16(g).66
The government's about-face on its remedy proposals provides another reason why heightened judicial scrutiny is required. While the government now says that the PFJ will provide effective relief, this reflects a marked abandonment of its earlier position. Indeed, the Justice Department's position just 18 months ago was that only structural relief was adequate, and conduct decrees like the proposed PFJ were inherent failures. As emphasized in one of the cases cited by the Justice Department, less deference is warranted when "the government has requested broad relief at the outset, represented to the courts that nothing less would do, and then abruptly knuckled under." United States v. National Broad. Co., 449 F. Supp. 1127, 1144 (C.D. Cal. 1978).
The point is not that the Department has decided not to seek divestiture, but instead that the conduct remedies it now proposes contradict its prior representations to this Court on their effectiveness. The earlier DOJ position was also consistent with its prior settlement decisions in this litigation itself. In the mediations supervised by Chief Judge Richard Posner in March 2000, the Department and the State plaintiffs demanded settlement terms that would have gone far beyond the limited provisions of the PFJ in eradicating Microsoft's ability to act anticompetitively. Indeed, the plaintiffs' last settlement proposal in the mediations -- dubbed "Mediator's Draft 18 (Attachment B) -- would have included provisions requiring Microsoft to license the actual source code for Windows, to permit ISVs to modify Windows itself, and to allow OEMs to "display[] a middleware user interface" in lieu of the Windows desktop. None of these or similar provisions is included in the proposed decree. Thus, the PFJ is considerably weaker in several key respects than the very conduct relief which the Department demanded in settlement before Microsoft's Sherman Act liability had been established. 67
Given the importance of this case, and Court's obligation to look to the Supreme Court and the D.C. Circuit for guidance rather than the Justice Department, the Court must decide for itself whether the settlement would give the public effective relief against Microsoft's proven wrongdoing.
The drafting of an antitrust decree necessarily "involves predictions and assumptions concerning future economic and business events."68 It is a "cardinal principle" of our system of justice that "factual disputes must be heard in open court and resolved through trial-like evidentiary proceedings." Microsoft III, 253 F.3d at 101. This mandate for evidentiary hearings applies not just to liability determinations, but also to determinations concerning the "appropriate [form of] relief." Id.; see also, d. at 107 (vacating and remanding Judge Jackson's remedy decree in large part due to his "fail[ure] to hold an evidentiary hearing despite the presence of remedies-specific factual disputes," and holding that a remedies decree must be vacated whenever there is "a bona fide disagreement concerning the substantive items of relief which could be resolved only by trial" Id. (quoting Interim Order at 62).
The Tunney Act contemplates an evidentiary hearing in these circumstances. As the Justice Department recognizes, this court must permit the use of the "additional procedures" authorized by 15 U.S.C. § 16(f)" -- which include live hearings with fact and expert testimony -- if "the [public] comments have raised significant issues and ... further proceedings would aid the court in resolving those issues." CIS, 66 Fed. Reg. at 59476. It strains credulity to suggest, as the Justice Department does, that the remedial phase of the most complicated antitrust case in decades will not involve "significant issues" that would benefit from "further proceedings."
Evidentiary hearings are critically important in complex antitrust cases because the assessment of antitrust remedies necessarily requires the Court to determine a number of facts relevant to both the degree of anticompetitive harm and the likely future condition of the market in which competition must be restored. United States v. United States Gypsum Co., 340 U.S. 76, 89 (1950); see also United States v. Glaxo Group, Ltd., 410 U.S. 52, 64 (1973). In particular, any proposed settlement decree must reach forward in time to "assure the public freedom from" continuance of the monopolistic practices. Id. As such, this Court must make "`predictions and assumptions concerning future economic and business events.'" Microsoft III, 253 F.3d at 102 (quoting Ford, 405 U.S. at 578). Although courts retain wide discretion in fashioning such forward-looking relief, they must base that relief on a sound evidentiary record. International Salt, 332 U.S. at 401.
In this case it is especially important to heed Congress's instruction to "resort to calling witnesses for the purpose of eliciting additional facts," HOUSE REPORT, supra, at 5, because the record has not yet been developed on remedies. See Associated Milk Producers, Inc., 394 F. Supp. 34 (W.D. Mo. 1975).69 Indeed, the procedural posture that the Court now faces is more closely akin to a contested summary judgment motion or administrative consent decree, for which hearings are the standard method of resolution. E.g., Celotex Corp. v. Catrett, 477 U.S. 317 (1986); Citizens for a Better Environment v. Gorsuch, 718 F.2d 1117 (D.C. Cir. 1983); United States v. Trucking Employers, Inc., 561 F.2d 313 (D.C. Cir. 1977). 70
Only by permitting third parties, such as ProComp and its members, to participate fully in such a proceeding can the Court assure that there will be adequate evidentiary attention to facts and circumstances that contradict the Department's views on the market, competition and other issues relevant for remedy purposes. Otherwise, this Court would repeat the very error that led the D.C. Circuit to reverse the last judgment in this case.
For all the foregoing reasons, the Court must find that the Proposed Final Judgment is not in the public interest. At a minimum, the Court should defer any judgment on the PFJ until the upcoming remedies hearing in the ongoing litigation is conducted. This is necessary to avoid inconsistent remedies. Indeed, many of the remedies proposed by the Litigating States are irreconcilable with those proposed by the PFJ. When the Court does consider the PFJ, it is obliged in the discharge of its Article III duties to make an independent determination whether the PFJ adequately fulfills the mandate of the D.C. Circuit.
FOOTNOTES
1 Microsoft Corp. v. United States, 530 U.S. 1301 (2000) (denying appeal); Microsoft Corp. v. United States, 122 S. Ct. 350 (2001) (denying certiorari).
2 Like AT&T, "It]his is not an ordinary case." 552 F. Supp. at 151
3 A Tunney Act court is authorized to "take testimony of Government officials," appoint a "special master and such outside consultants or expert witnesses as the court may deem appropriate," hear evidence and argument from other interested persons and organizations, and "take such other action in the public interest as the court may deem appropriate." 15 U.S.C. § 16(f). These procedures are so important to a careful assessment of the public interest that courts routinely employ them, even in pretrial Tunney Act cases. See, e.g.. United States v. Bechtel Corp., 1979-1 Trade Cas. (CCH) ¶ 62,430 (N.D. Cal. 1979), aff'd 648 F.2d 660 (9th Cir. 1981); Dillard v. City of Foley, 166 F.R.D. 503 (M.D. Ala. 1996); United States v. Westinghouse Elec. Corp., 1988-1 Trade Cas. (CCH) ¶ 68,012 (D.D.C. 1988); United States v. ARA Serves., 1979-2 Trade Cas. (CCH) ¶ 62,861 (E.D. Mo. 1979); United States v. Mid-America Dairymen, Inc., 1977-1 Trade Cas. (CCH) ¶ 61,508 (W.D. Mo. 1977).
4 Based on the deadlines set forth in the Court's November 8, 2001 Order and Section 16(b) of the Tunney Act, comments on the PFJ and the Department's responses to those comments are not due until February 26, 2002. Thus, the remedy trial, scheduled to begin on March I 1, 2002, will start only two weeks after the Justice Department is scheduled to submit its Response-to-Comments on the PFJ. Even if the Justice Department files its Response-to-Comments early, deferring judgment on the PFJ will cause little if any delay, no prejudice, and great benefits to the parties and the Court.
5 Phoenix Renovation Corp. v. Gulf Coast Software, F.R.D. 580, 582 (E.D. Va. 2000) (quoting Fed. R. Civ. P. 54(b)); see also Dana Corp. v. Celotex Asbestos Settlement Trust, 251 F.3d 1107, 1120 (6th Cir. 2001) (affirming the district court's condemnation of a reorganization plan provision that unnecessarily "raise[d] a likelihood of inconsistent judgments").
6 "[A] remedies decree in an antitrust case must seek to 'unfetter a market from anticompetitive conduct," to 'terminate the illegal monopoly, deny to the defendant the fruits of its statutory violation, and ensure that there remain no practices likely to result in monopolization in the future." Microsoft III, 253 F.3d at 103 (citations omitted).
7 The legislative history of the Tunney Act indicates that Congress was clearly aware of Cascade and intended the Act's public interest standard to codify that rule of antitrust remedies. Judge L Skelly Wright, former Chief Judge for the D.C. Circuit, discussed the Cascade problem at length in his Senate appearance, explaining that "the Supreme Court felt compelled to say that -- and I am quoting -- 'The United States knuckled under to El Paso and settled this litigation' -- close quote, rather than fully protecting the public interest by getting a decree which fully insured future competition." SENATE REPORT, supra, at 147.
8 See Microsoft L 56 F.3d at 1452 (no claim that "Microsoft obtained its alleged monopoly in violation of the antitrust laws") (emphasis in original); Microsoft III, 253 F.3d at 58 (Microsoft "violated . 2 by engaging in a variety of exclusionary acts ... to maintain its monopoly").
9 Statement of Charles F. (Rick) Rule, Fried Frank Hams Shriver & Jacobson, Prepared for the Committee on the Judiciary, United States Senate, at 5 (Dec. 12, 2001) ("Rule Senate Testimony").
10 This self-evident proposition becomes even more clear when the relief in this case is compared with that adopted by the Department, approved by this Court under the Tunney Act and affirmed on the merits by the Supreme Court in the AT&T antitrust case. United States v. AT&T, 552 F. Supp. 131. There, like here, the Section 2 claim was monopoly maintenance, not unlawful acquisition of monopoly power. Furthermore, unlike Microsoft, AT&T's monopoly was in part a de jure consequence of regulatory and legal protections. Id. at 135-41. Had there in fact been a difference for antitrust remedy purposes between monopoly maintenance and monopoly acquisition, use of the ultimate relief of divestiture in AT&T would have been impermissible. Thus, only by ignoring the largest antitrust settlement of the generation preceding Microsoft can the settling litigants here escape the conclusion that termination of a defendant's monopoly power is the principal remedial objective of Section 2 monopoly maintenance cases.
11 United States v. Microsoft Corp., No. 00-5212, Order (Aug. 2, 2001) (per curiam).
12 The Department's reliance on United States I,. BNS, Inc., 858 F.2d 456 (9th Cir. 1988), is especially problematic. CIS, 66 Fed. Reg. at 59476. In BNS, a merger case, the public interest "could be harmed irreparably by permitting a merger to become a fait accompli" while the district court deliberated on the adequacy of the decree's provisions. 858 F.2d at 462. The proposed Microsoft settlement could not be more different. This is not a merger proceeding. Indeed, the public interest would be harmed profoundly if the Court accepts a relief proposal, like the PFJ, that is plainly inadequate to restore competition or eliminate the widespread anticompetitive practices whose illegality was squarely affirmed by the Court of Appeals. Accordingly, the Department's citation to BNS for the proposition that this Court cannot "engage in an unrestricted evaluation of what relief would best serve the public," id., is both highly misleading and inapplicable.
13 The Court of Appeals admonished and reversed the prior District Judge in this case, in part, for entering a decree based largely on the relief proposed by the government. Although the Justice Department's officers "are by reason of office obliged and expected to consider w and to act -- in the public interest," Microsoft III. 253 F.3d at 34 (quoting Judge Jackson), that did not excuse the District Court from its independent obligation to consider and explain how the relief proposed would meet the sealed objectives of antitrust remedies. Microsoft III. 253 F.3d at 34. Nothing less is warranted now.
14 H.R. REP. NO. 93-1463 (1974) ("HOUSE REPORT"). Note, The ITT Dividend: Reform of Department of Justice Consent Decree Procedures, 73 colum. L. Rev. 594 (1973).
15 The purposes of the Tunney Act are not implicated in a proposed post-trial settlement of a Government. Section 2 prosecution that has already been affirmed on appeal. There is no risk of excessive secrecy, because the remedy phase of a litigated antitrust case necessarily takes place in an open judicial process dining which, based on the trial record and l/ability findings, the district determines whether the government's requested relief adequately remedies the defendant's violations of the antitrust laws. Nor is there any risk that judicial review of a proposed post-appeal consent decree will discourage government antitrust settlements, as the Department retains the power -- which it exercised long ago in this case -whether to initiate an antitrust prosecution or settle.
16 The courts have therefore distinguished between a court's involvement in "the executive branch's decision to abandon litigation," which "might impinge upon the doctrine of separation of powers," and "[j]udicial approval of consent decrees under the [Tunney] Act," which is "an entirely distinct proposition because the decree is entered as the court's judgment." In re IBM Corp., 687 F.2d 591,602 (2d Cir. 1982).
17 Microsoft accepts the concept of inflection points in technology markets, and unsuccessfully argued to the D.C. Circuit that the possibility of inflection points meant that it did not enjoy monopoly power in the operating systems market. Brief of Appellant Microsoft Corporation, United States v. Microsoft Corp., at 16 (D.C. Cir. filed Nov. 27, 2000) ("Microsoft D.C. Circuit Brief').
18 The CIS agrees that distribution of Java by Netscape "creat[ed] the possibility that Sun's Java implementation would achieve the necessary ubiquity on Windows to pose a threat to the applications barrier to entry." CIS at 16, 66 Fed. Reg. at 59463
19 Henderson Decl., supra, ¶ 73.
20 "Microsoft's campaign succeeded in preventing -- for several years, and perhaps permanently -- Navigator and Java from fulfilling their potential to open the market for Intel-compatible PC operating systems to competition on the merits." United States I,. Microsoft Corp., 87 F.Supp.2d 30, 38 (2000) (Conclusions of Law).
21 The Competitive Impact Statement explains that the objective of the proposed decree is "to restore the competitive threat that middleware products posed prior to Microsoft's unlawful conduct." CIS, 66 Fed. Reg. at 59463-64.
22 James Senate Testimony, supra, at 10.
23 See Findings of Fact ¶ 397 ("By bundling its version of the Windows JVM with every copy of Internet Explorer and expending some of its surplus monopoly power to maximize the usage of Interact Explorer at Navigator's expense, Microsoft endowed its Java runtime environment with the unique attribute of guaranteed, enduring ubiquity across the enormous Windows installed base.").
24 Assistant Attorney General James has suggested that such relief would be improper because no "essential facilities" claim was made by the government. James Senate Testimony, supra, at 10 (emphasis added). But a monopoly maintenance "must cant" remedy designed to redress artificial applications barriers to entry does not need to be supported by an essential facilities claim. To the contrary, in its 1998 Complaint to this Court, the government expressly sought as one form of injunctive relief that Microsoft be required to "include with [the Windows] operating system the most current version of the Netscape Internet browser." Complaint, . VII.2.e.1 (Prayer for Relief). Thus, the very "must-carry" obligations that the Department now opposes were the precise relief it initially sought.
25 Professor Rebecca Henderson of the MIT Sloan School of Management, a remedies expert for the government, testified by affidavit in 2000 that "[t]he availability of the world's most popular office productivity suite on alternative platforms would serve to reduce the barriers to entry protecting Microsoft's monopoly, which will, in turn, increase the potential for competition in the PC operating systems market." Declaration of Rebecca M. Henderson, United States v. Microsoft Corp., No. 98-1232 (TPJ), at ¶ 22 (D.D.C. filed April, 28, 2000).
26 United States v. Microsoft Corp., No. 00-5212, Order (Aug. 2, 2001) (per curiam).
27 Microsoft Corporation's Petition for Rehearing, United State v. Microsoft Corp., Nos. 00-5212, 5213, at 2, 4 (D.C. Cir. filed July 18, 2001) (quoting United States v. Microsoft Corp., 147 F.3d 935, 958 (D.C. Cir. 1998) (Wald, J., concurring in part and dissenting in part)) ("Microsoft D.C. Cir. Rehearing Petition").
28 James Senate Testimony, supra, at 14 (emphasis added).
29 For Section I purposes, the D.C. Circuit ruled that technological innovation is subject to an efficiency-harm balancing test under the rule of reason. Microsoft III, 253 F.3d at 90, 93. Given the lack of an efficiency justification by Microsoft for having commingled the browser with the operating system, it is highly likely that the Government would have prevailed on the Section I claim under the "rule of reason" test. See id. at 66 (Microsoft does not "argue that either excluding IE from the Add/Remove Programs utility of commingling code achieves any integrative benefit").
30 See also Findings of Fact ¶ 388 ("Gates told Intel's CEO in June 1996 that he did not want the Inter Architecture Labs cooperating with Sun to develop methods for calling upon multimedia interfaces in Windows."); id. ¶ 404 ("Microsoft used threats to withhold Windows operating-system support from Intel's microprocessors and often to include Intel technology in Windows in order to induce Intel to stop aiding Sun in the development of Java classes that would support innovative multimedia functionality.").
31 Findings of Fact ¶ 95.
32 Findings of Fact ¶ 102.
33 Findings of Fact ¶ 94.
34 Under the antitrust laws, a firm has not as a matter of law entered into an "agreement" with a distributor or other party where it unilaterally declares its position and by virtue of its economic power compels distributors to adhere to those conditions. See Monsanto Co. v. Spray-Rite Svc. Corp., 465 U.S. 752, 764 ¶ n.9 (1984).
35 CIS, 66 Fed. Reg. at 59460. In related private antitrust litigation, courts similarly have found that Microsoft "create[d] the illusion that [a competing product] was incompatible with Windows by inserting error messages conveying to the user that either [the competing product] was incompatible with Windows that [Microsoft's product] was the only environment in which Windows could properly function." Caldera, Inc. v. Microsoft Corp.. 72 F. Supp. 2d 1295, 1314 (D. Utah 1999).
36 Litigating States' Remedy Proposal, supra, at 12.
37 Schine Chain Theatres, Inc. v. United States, 334 U.S. 110, 128 (1948)
38 National Soc'y of Prof. Eng'rs v. United States, 435 U.S. 679, 698 (1978).
39 James Senate Testimony, supra, at 6.
40 National Soc'y of Prof Eng'rs, 435 U.S. at 698; United States v. U.S. Gypsum Co., 340 U.S. 76, 90 (1950) (Section 2 relief may "go beyond the narrow limits of the proven violation"). Accord International Salt, 334 U.S. at 400; DuPont, 366 U.S. at 327.
41 See also CIS, 66 Fed. Reg. at 59468 (decree "requires Microsoft to disclose to ISV, IHVs, LAPs, ICPs and OEMs all of the interfaces and related technical information that Microsoft Middleware uses to intemperate with any Windows Operating System Product").
42 The district court's "Internet Order" did not suffer from this problem because Section 3.b of its API disclosure provisions broadly required the release of APIs that Microsoft employs to enable (i) Microsoft applications to interoperate with Microsoft Platform Software (defined as both operating systems and middleware), (ii) Microsoft middleware to interoperate with a Microsoft operating systems product (or Microsoft middleware distributed with a Microsoft operating systems product, and (iii)any Microsoft software installed on one computer to interoperate with a Microsoft operating systems or middleware product installed on another computer. The proposed decree's use of "Microsoft Platform Software" is confined to Sections III.A and III.F.I (retaliation) and Section III.F.2 and III.G.I (exclusivity), but has no application to API disclosure. United States v. Microsoft, Final Judgment (D.D.C. 2000) ("Interim Order").
43 The Competitive Impact Statement flatly mischaracterizes this section in contending that the definition of Microsoft Middleware captures what it calls "`redistributable[s]' associated with Microsoft Middleware Products." CIS, 66 Fed. Reg. at 59464. The Department claims that "[i]f such a redistributable exists, as they currently do for most Microsoft Middleware Products, then the redistributable is Microsoft Middleware" because it is "distributed separately" from Windows. Id. This explanation, however, ignores the clause specifying that separate distribution must be "to update" Windows under Section VI.J.
44 A complete list of Microsoft trademarks is posted on the Web at http://www.microsoft.com/trademarks/docs/mstmark.rtf. The description in the test is taken from the document at that location titled "Microsoft Corporate Trademarks," dated December 2001. That document advises that other companies should "not use any trademark symbols ... for those products that are not listed above as trademarks, such as `Microsoft® Excel,' `Microsoft® Internet Explorer.'"
45 CIS, 66 Fed. Reg. at 59460, 59468.
46 The Interim Order defined "Technical Information" as "all information regarding the identification and means of using APIs and Communications Interfaces that competent software developers require to make their products running on any computer interoperate effectively with Microsoft Platform Software running on a Personal Computer. Technical information includes but is not limited to reference implementations, communications protocols, file formats, data formats, syntaxes and grammars, data structure definitions and layouts, error codes, memory allocation and deallocation conventions, threading and synchronization conventions, functional specifications and descriptions, algorithms for data translation or reformatting (including compression/decompression algorithms and encryption/decryption algorithms), registry settings, and field contents." In contrast, the PFJ requires only disclosure of related "Documentation," defined in Section VI.E as "information" that is "of the sort and to the level of specificity, precision and detail that Microsoft customarily provides for APIs it documents in the [MSDN]." PFJ, 66 Fed. Reg. at 59459.
47 The CIS appears to limit the extent of Microsoft's ability to withhold APIs under Section 1113 of the PFJ. But the CIS description is either unclear or inconsistent with the terms of Section III.J. At a minimum, the Department should reconcile these two documents in order to mitigate the risk of future anticompetitive conduct and litigation over the interpretation of this section. There is no reason to believe that Microsoft will endorse the CIF interpretation, and no doubt Microsoft will argue in any future action that where these two documents conflict, the plain language of the PFJ controls.
48 CIS, 66 Fed. Reg. at 59469. See also CIS, 66 Fed. Reg. at 59460 (decree "prevent[s] Microsoft from incorporating into the Windows operating system features or functionality with which only its own servers can interoperate by requiring Microsoft to disclosure the communications protocols that are necessary for software located on a computer server to interoperate with the Windows operating system").
49 The CIS makes clear that this ploy avoids the Section III.E obligations, stating that disclosure is not required if Microsoft "only distributes code that implements that protocol along with its server software or otherwise separately from the client operating system ..." CIS, 66 Fed. Reg. At 59469.
50 Walter S. Mossberg, Microsoft Has Good Year, At Expense of Customers, Wall Street J., Dec. 27, 2001, at B1.
51 We note that at the time of the announcement, Microsoft had already achieved significantly greater than 80 percent of the browser market as a result of its six-year anticompetitive campaign, so it is hard to view this as a concession.
52 Available at www.microsoft.com/MSCorp/presspass/Press/2001/Jul01/07-11OEMFlexibilityPR.asp.
53 Microsoft's resulting power over Internet browsers and personal productivity applications provides it with alternative vehicles with which to achieve the same anticompetitive foreclosure of middleware threats that it accomplished in 1995-98 through Windows itself.
54 As Microsoft executive (and trial witness) Paul Maritz put it, "the most important thing we can do is not lose control of the Web client," because "[b]y controlling the client, you also control the server." Gov't Ex. 498. Microsoft can suppress competition by adding proprietary features and protocols to the IE browser that are necessary to generate actions by its server operating systems products or by refusing to add features and protocols that would similarly support a competitor. Professor Schmalensee acknowledged this incentive at trial: "[I]f one company controlled the browser and its look and feel and how it presented applications, it could severely enhance or detract from the application functionality of programs or applications running on the server." 6/24/99 (p.m.) Tr. 46-47; see also id. at 48; Henderson Decl. ¶ 82 (quoting Rasmussen Dep., 12/15/98 (a.m.), at 67-68).
55 .NET Defined, available at www.Microsoft.com/net/whatis.asp.
56 "So for every element of Windows -- user interface, the APIs ... for each one of those things there's an analogy here." Bill Gates, Forum 2000 Keynote, Bill Gates Speaks About the .NET Platform. (Available at www.microsoft.com/BUSINESS/vision/gates.asp)
57 Substantive "reasonable" provisions are III.B.2, III.C.5, III.E, III.F2 (two), III.G, III.H.2, III.I, III.J.2.b and III.J.2.C. Procedural "reasonable" provisions are IV.A.2, IV.A.2.b, IV.A.2.c, IV.A.4, IV.A.6, IV.A.7 (two), IV.A.8.b (three), IV.A.8.h and IV.A.8.l (three).
58 3 P. AREEDA & H. HOVENKAMP ANTITRUST LAW ¶ 704.3, at 213 (1999 Supp). See William K. Kovacic, Designing Antitrust Remedies for Dominant Firm Misconduct, 31 Conn. L. Rev. 1285, 1311 (1999) ("By blockading recourse to certain commercial tactics, a remedial decree will inspire the defendant to pursue other paths that circumvent the judicially imposed constraints."). As the Supreme Court cautioned in the landmark DuPont antitrust case, "the policing of an injunction would probably involve the courts and the Government in regulation of private affairs more deeply than the administration of a simple order of divestiture. United States v. E.I. du Pont de Nemours & Co., 366 U.S. 316, 334 (1961); accord, AT&T, 552 F.Supp. at 167-68.
59 Cascade Natural Gas Corp. v. El Paso Natural Gas Co., 356 U.S. 129, 136, 141 (1967); AT&T, 552 F. Supp. at 152; Associated Milk Producers, 394 F. Supp. 35, 42 (W.D. Mo. 1975).
60 United States v. Automobile Mfrs. Ass'n, 307 F. Supp. 617, 621 (C.D. Cal. 1969), aff'd mem. sub nom. New York v.United States, 90 S. Ct. 1105 (1970).
61 Cascade, 386 U.S. at 137; Automobile Mfrs. Ass'n, 307 F. Supp. at 621.
62 In Cascade, the Department refused to implement an antitrust divestiture decree affirmed on appeal by the Supreme Court. The Court eventually directed the Department to oversee "divestiture without delay" and instructed the district court to prepare "meticulous findings ... in light of the competitive requirements" of the remedy. 386 U.S. at 137.
63 CIS, 66 Fed. Reg. at 59475.
64 The CIS was intended, rather, to be "detailed notice to the public what the case is all about. Further than that, the public impact statement makes the lawyers for the Department of Justice go through the process of thinking and addressing themselves to the public interest consideration in the proposed decree. There is no better exercise for determining whether you are right or not than trying to put it down on paper to see how it writes." SENATE REPORT, supra, at 8 (remarks of Judge J. Skelly Wright).
65 See Central Contracting, 527 F. Supp. at 1103 (quoting 119 Cong. Rec. 24597 (1973) (remarks by Senator Tunney)).
66 The company apparently takes the unsupportable position that lobbying communications on the subject of the Microsoft litigation occurring before the September 2001 negotiations resumed are not "relevant" to the settlement. Microsoft also claims many communications were protected by the "counsel of record" exception. "Counsel of record" for purposes of these disclosures is intended to differentiate between lawyers actively appearing before the trial court and those undertaking related, but non-judicial "lobbying" functions. Central Contracting Co., 527 F. Supp. at 1105. The House Report discusses Congress's intent to distinguish "lawyering contacts," which warrant protection, from "lobbying contacts," which must be disclosed. It states that a lobbying contact is performed by "counsel of record accompanied by corporate officers; or by attorneys not counsel of record.'" HOUSE REPORT, supra, at 6 (emphasis added). Congress requires their disclosure in order to guarantee "that the Government and its employees in fact avoid practicing political justice.'" Id. (quoting Civil Service Comm'n, 414 U.S. 906 (1973)).
67 The barrier to introduction into evidence of settlement offers under Rule 408 of the Federal Rules of Evidence does not apply where the settlement is not used to show liability but instead, as here, to illuminate the policy considerations governing fashioning of a remedy. E.g., Carney v. American Univ., 151 F.3d 1090, 1095 (D.C. Cir. 1998). Rule 408 precludes proof of settlements and settlement offers only "to prove liability for or invalidity of" a claim. Fed. R. EvId. 408. Indeed, evidence of settlements is expressly permitted by Rule 408 "when the evidence is offered for another purpose." Id.
68 Ford, 405 U.S. at 578.
69 To the contrary, the D.C. Circuit reversed and remanded precisely because the prior District Judge did not permit an evidentiary hearing on remedies. The court stressed that "a full exploration of the facts is usually necessary to properly draw an antitrust decree so as to prevent future violations and eradicate existing evils," and remanded for such an exploration of facts. Microsoft III, 253 F.3d at 101 (quoting United States v. Ward Baking Co., 376 U.S. 327, 330-31 (1964) (internal quotations and brackets omitted)).
70. In summary judgment practice, complex legal issues are frequently presented to courts on the basis of affidavits and other "paper" evidence. But, unless the papers reveal no "genuine issue" of "material fact," a standard that cannot be met here, summary judgment motions must be denied and a case set for trial so that the Court can adduce whether the parties have met their respective burdens of proof on the disputed factual issues. E.g., Celotex Corp., 477 U.S. at 323; Thompson Everett, Inc. v. National Cable Adver., 57 F.3d 1317, 1322 (4th Cir. 1995) (applying Celotex to review of a motion for summary judgment of antirust conspiracy claim). Indeed, where the credibility of an affiant is at issue, as it undoubtedly will be here with respect to the reliability of expert opinions and projections of future economic and technological developments, it is difficult to conceive of any basis on which the Court would be permitted to resolve such controverted issues without availing itself of ordinary, trial-type evidentiary procedures.
Attachment A
IN THE UNITED STATES DISTRICT COURT
FOR THE DISTRICT OF COLUMBIA
DECLARATION OF KENNETH J. ARROW
Kenneth J. Arrow declares under penalty of perjury as follows:
1. I am the Joan Kenney Professor of Economics Emeritus and Professor of Operations Research Emeritus at Stanford University. I received the degrees of B.S. in Social Science from The City College in 1940, M.A. in mathematics from Columbia University in 1941, and Ph.D. in economics from Columbia University in 1951. I have taught economics, statistics, and operations research at the University of Chicago, Harvard University, and Stanford University, and I have written more than 200 books and articles in economics and operations research. I am the recipient of numerous awards and degrees, including the Nobel Memorial Prize in Economic Science (1972). A significant part of my writing and research has been in the area of economic theory, including the economics of innovation and its relation to industrial organization. My curriculum vitae is attached.
2. I have been asked by ProComp to comment on various economic issues related to the Revised Proposed Final Judgment ("PFJ" or the "decree") proposed by the United States, various settling States and Microsoft Corporation ("Microsoft").
3. My review of the PFJ begins with the fact that Microsoft has been found liable for violating Section 2 of the Sherman Act by engaging in a widespread series of practices that illegally maintained its monopoly in Intel-compatible PC operating systems. These practices were focused on eliminating the threat posed to Microsoft's PC operating system monopoly by the combination of Netscape Navigator and cross-platform Java technology ("middleware competition").
4. Given that Microsoft has been found liable for illegal monopoly maintenance, the remedies in this case should be designed to eliminate the benefits to Microsoft from its illegal conduct. To the extent possible, the remedies should be designed to restore the possibility of competition in the market where monopoly was illegally maintained (i.e., the market for PC operating systems). In addition, the remedies should strengthen the possibilities for competition and deter the exercise of monopoly power in the present and future, taking account of the special problems of an industry in which network effects are important.
5. It is my opinion that the PFJ fails to accomplish these objectives. First, the PFJ is unduly focused on attempting to re-create an opportunity for future middleware competition. Because of network effects and path dependencies, Microsoft's monopoly power in PC operating systems is more entrenched than it was in the mid-1990s. It will be exceedingly difficult now, even with the best of remedies, to re-establish middleware fully as the kind of competitive threat to Microsoft's monopoly power that it posed in the mid-1990s. Additional remedial steps need to be taken to ensure that Microsoft does not benefit from its illegal conduct and the consequences of that conduct on dynamic competition in the OS market. Second, the PFJ does not address the fact that no effort to restore competition in the market for PC operating systems will be successful without measures designed to lower the applications barrier to entry that currently protects Microsoft's position in this market. Third, the enforcement mechanism described in the PFJ seems likely to be ineffective, even with respect to the inadequate remedies in the PFJ. Fourth, the PFJ pays insufficient attention to the ways in which Microsoft is currently attempting to protect its monopoly power by using its illegally maintained monopoly in PC operating systems against current and future competitive threats, such as server operating systems and Web services.
6. This affidavit has six pans and is organized as follows. After this introduction (Part I), Part II reviews the threat that Netscape, Java and the Internet posed in the mid-1990s to Microsoft's monopoly power in PC operating systems. Part HI then reviews the illegal conduct that Microsoft used in defeating this threat. Part III also analyzes the state of the computer industry today following this illegal conduct and explains why it seems unlikely, at this stage, that the middleware threat can be re-created. With this as background, Parts IV and V review and assess the remedies proposed in the PFJ. Part IV critiques the remedies designed to restore middleware competition. In addition, Part IV discusses the lack of attention in the PFJ to the applications barrier to entry that protects Microsoft's monopoly power in PC operating systems. It also notes certain deficiencies in the enforcement mechanism proposed in the PFJ. Part V follows with a discussion of Microsoft's efforts to protect its existing monopoly power by using its illegally maintained monopoly in PC operating systems to gain advantages in other markets that threaten to reduce the scope of its current market power. Part V explains that the PFJ gives insufficient attention to this important subject -- a subject that bears on the future of competition in the computing industry. The affidavit concludes in Part VI with a summary of conclusions
7. Network externalities have been central to Microsoft's ability to maintain its monopoly power in the market for PC operating systems. Both the District Court and the U.S. Court of Appeals for the District of Columbia Circuit referred to the "applications barrier to entry," the process by which a large installed base induces the development of applications and other complementary goods designed for the dominant operating system, which further reinforces the position of the dominant operating system. I described this process in a declaration that I submitted in 1995 on behalf of the government in a prior settlement with Microsoft:
8. The applications barrier to entry implies that it is likely that a single platform (or programming environment) will dominate broad segments of the computer software industry at any point in time. This does not necessarily imply that there will be monopoly; that depends on the extent to which the dominant platform is proprietary or closed. However, if the dominant platform is proprietary (which is certainly the case with Windows), then the interdependence of applications and operating systems creates a barrier against any new entrant. A new entrant would need to create both an operating system and the applications that make it useful.
9. In addition, any customer of a new entrant would have to incur considerable costs in switching to a new system. In the first place, the customer would have to learn new operating procedures. Second, there would be a problem of compatibility of files. These factors constitute a natural obstacle to change, so that a system with a large installed base will have a tendency to retain its users.
10. The special nature of operating systems and software also gives Microsoft, because of its large installed base of operating system, a great advantage in the markets for complementary software. Specifically, it can distribute the software much more easily than its competitors. Since virtually every new PC ships with Windows, Microsoft can put its software into the hands of users by including it with the operating system. Any other vendor of complementary software that wanted to distribute through OEMs would have to cut a separate deal with each OEM, and would face the task of persuading OEMs to carry software products that may be directly competitive with products offered by Microsoft. As a result, complementary software from other vendors typically either has to be downloaded (which imposes added costs on users) or distributed separately to users in "shrink wrap." In addition, Microsoft has the ability to allow Microsoft developers of complementary software access to "hidden APIs" -- application programming interfaces in the PC operating system that Microsoft developers know about but which are not disclosed fully to competing developers of complementary software.
11. A threat to Microsoft's monopoly in PC operating systems arose in the mid-1990s with the nearly simultaneous emergence of the Internet browser developed by Netscape and the Java programming environment. These are both examples of middleware -- application software designed to run on multiple operating systems and which has its own set of APIs. Middleware that provides extensive functionality through a broad set of APIs has the potential to become an alternative platform for application development. If many applications valued by PC users were written to middleware APIs, and if the middleware were ported to other operating systems (existing or to be created), then the applications barrier to entry in the market for PC operating systems would be weakened.
12. Netscape Navigator was a browser that also had the potential to become a platform for application programs. Netscape's browser had its own set of APIs to which developers could write application programs.
13. The initial success of Netscape Navigator was dramatic. Netscape shipped its first browser in September 1994.1 In July 1995, less than a year later, its share of the browser market was 74%. 2 By mid-1996, Netscape's Share had reached 85%.3
14. The threat that Netscape pored to Microsoft's monopoly power in PC operating systems was made even greater by the nearly simultaneous development of Java. The Java technology has several pieces. It is a programming language that I understand has features well suited for writing "distributed applications" - applications that run on networks, calling upon resources located on different computers in the network. Java technology also includes the Java Virtual Machine ("JVM") and Java Class Libraries. The JVM and Java Class Libraries am forms of middleware. They are software programs that have been implemented on Windows and many other operating systems. A JVM is software that converts Java code into instructions that can be processed by the operating system on which the JVM sits. The Java Class Libraries are software that performs specific functions that developers can call upon, and build into, their Java application programs. The JVM and Java Class Libraries are sometimes referred to collectively as the "Java runtime environment." The Java technology has been licensed in a way designed to encourage its implementation on a variety of different operating systems. The Java ideal was captured in the phrase, "write once, run anywhere."
15. Java added to the threat posed by Netscape because it extended the set of middleware APIs to which developers could write application programs. It increased the chances that developers could write sophisticated PC application programs written to middleware APIs instead of Windows APIs. Netscape also complemented Java by serving as a distribution mechanism. The Java technology could not succeed without widespread distribution of the Java runtime environment. Because Netscape supported Java and included the Java runtime environment with every copy of its browser, growth in the share of PCs that used the Netscape browser also meant growth in the share of PCs with a Java runtime environment that supported Java's "write once, run anywhere" ideal.
16. The economic relationship between middleware and the OS is unusual among the commodities that economic theory usually deals with. Middleware is a complement to any OS in the short run, but it facilitates substitution among operating systems in the long run. Middleware is a complement in the short run because it adds functionality to the existing OS, but it is in a sense a substitute in the long run, because applications can be written to it rather than to the OS. Middleware therefore permits substitution among operating systems, since the applications are not specific to any one OS. Therefore, an OS monopolist will have an incentive to control middleware in order to maintain its OS monopoly. The short-run complementarity becomes an instrument by which this incentive can be realized. The middleware has to be ported to the OS, and the OS producer's control of the needed APIs can be used to restrict the spread and use of the middleware.
17. Middleware is naturally thought of as a disruptive technology, and the emergence of middleware in 1995 created what is frequently referred to as an "inflection point." Put simply, this means that the then well-defined organization of the software market for personal computers might be altered substantially, or at least such a risk existed. As that organization was centered on the Microsoft Windows operating system and its productivity application suite Microsoft Office, Microsoft had the most at risk from any disrupting change that resulted from middleware.
18. Technological disruptions such as the middleware threat of the mid-1990s do not occur frequently. They only arise when there is an important innovation that allows technology to evolve and create new products or functionality that has widespread appeal. At times of technological disruption, the forces of dynamic competition can play an especially important role. The Netscape browser and the cross-platform Java technology separately and in combination had the potential to develop into an alternative platform for application programs that could run on any operating system and which could transform PC operating systems into a commodity business. Bill Gates, in his memorandum of May 26, 1995 on the "Internet Tidal Wave," described just this sort of dynamic competitive threat when he realized that, if successful, Netscape could "commoditize" the operating system.
19. There is no easy method by which an economist can determine exactly how significant a threat Java and Netscape actually represented to Microsoft's operating system monopoly. A precise determination of whether Netscape and Java could have succeeded in eroding Microsoft's monopoly power absent Microsoft's illegal conduct would require a counterfactual analysis that addressed a variety of complex interrelations. However, even without this kind of analysis, we have evidence that a reasonably expert onlooker felt the threat was serious, namely, the statements and behavior of Microsoft. Bill Gates, in his memorandum on the "Internet Tidal Wave," explained:
20. In the same memorandum, Gates made clear that he understood how Microsoft should leverage its Windows advantage to bolster its Internet position:
21. To summarize, in an industry marked by network externalities, there is a strong tendency to monopoly (at least when the dominant platform is proprietary or closed). The consumer welfare and efficiency losses associated with monopoly are well known, but the one most relevant here is the decreased incentive to technological innovation. It is all the more important to encourage what may be called dynamic competition, the entry of new firms and new products. At certain periods, whether due to technological innovation or to a transient situation in which the tendency to monopoly has not yet worked to its completion, the market will be confronted with alternative lines of development; Netscape Navigator and Java as against Microsoft products in 1995, client-server networks and web services today. At these periods, there may be opportunities for a new platform to compete with and possibly take over from the existing one. In view of the strong tendency to monopoly in this industry (because of network externalities), it is all the more important to keep the competition as viable as possible when the opportunity presents itself. In particular, illegal anticompetitive steps by existing monopolists should be prevented to the maximum extent possible. Such a policy prevents the stagnation of existing monopolists and encourages the expansion of the number of alternatives among which the buyers can choose.
22. Microsoft made a concerted effort to eliminate the threat from middleware competition. Microsoft was found to have engaged in illegal conduct exactly at the moment that dynamic competition might have flourished. As the D.C. Circuit concluded, Microsoft took illegal steps to exclude the middleware threat, and in particular, took anticompetitive actions directed against Netscape Navigator and Java. In particular, the D.C. Circuit judged illegal significant elements of Microsoft's strategy:
23. As of 1995, Microsoft's share was of the installed base of PC operating systems was 87% 4 while its share of the Internet browser market was less than 5%.5 Today, those figures stand at 92% for PC operating systems6 and 91% for browsers. 7 Thus Microsoft's position in PC operating systems remains strong, while its share in Internet browsers has risen dramatically.
24. Microsoft's illegal practices were successful in helping to minimize the threat that middleware posed for the creation of a programming environment outside of Microsoft's control. I am aware of no middleware today that poses a risk to Microsoft comparable to that posed by Navigator and Java in 1995. Nor does the government's Competitive Impact Statement suggest that such a threat exists today or is likely to emerge over the five-year duration of the PFJ.
25. Microsoft today has substantial advantages in middleware that make it unlikely the market itself will generate new entrants into middleware capable of re-creating the competitive risk faced by Microsoft in 1995. As noted earlier, through its control over Windows, Microsoft has had--and under the PFJ will continue to have--an enormous advantage in the distribution of software that is complementary to Windows. Since every new PC ships with Windows, Microsoft has a very easy way to get software into the hands of users: it can include it with the operating system. Microsoft can simply bundle the middleware with Windows or it can integrate the code into Windows itself.
26. This ensures the ubiquity of Microsoft middleware and operates as a barrier to entry for competing middleware. Any entrant would have to make a substantial investment to achieve comparable widespread distribution. A firm considering entry should understand that its inability to guarantee a universally exposed set of APIs means that, all other things equal, developers would prefer to write to the APIs exposed by Microsoft middleware. The ubiquity of Microsoft middleware and its ability to integrate middleware into Windows - which the PFJ does not constrain - therefore operate as economic disincentives for the development of competing middleware by potential entrants.
27. Microsoft also has complete freedom in how it prices its middleware. In bundling middleware with Windows, Microsoft need not charge an incremental price for the middleware. It can simply fold into the price of Windows whatever price it would charge for the middleware were it distributed separately. This would not be an option available for a potential entrant who will expect that it would need to establish a separate, discrete positive price for any middleware that it might create. The ability of Microsoft to set an apparent price of zero for its middleware operates as a barrier to entry in middleware.
28. Even if competing middleware were created, the ubiquity of Microsoft middleware would operate as a direct barrier of the distribution of that middleware. As the D.C. Circuit affirmed, OEMs are reluctant to install two products that perform the same function, as this raises support costs. Twice as many products will be supported for the same function, plus consumers may be confused by the presence of both products.
29. Moreover, Microsoft's ability to "embrace and extend" any middleware created by an entrant also operates as a barrier to entry. Again, it will take a substantial amount of time for an entrant to distribute innovative middleware. During that time, Microsoft will likely be able to imitate that middleware and distribute updated" versions of Microsoft middleware over the Internet to end users through its Windows Update feature. Given this, entry into middleware is less likely and this may reduce innovation in and development of middleware.
30. In sum, Microsoft took substantial steps to eliminate the threat posed to it by Netscape and Java. The D.C. Circuit affirmed that a substantial number of those actions constituted impermissible monopoly maintenance and therefore monopolization in violation of Section 2 of the Sherman Act. Today, Microsoft's illegally maintained monopoly operates as a substantial barrier to new entry into middleware. The monopoly operates as a disincentive for entry and thereby likely reduces innovation in middleware. Given this market structure, it is highly unlikely that market forces alone will lead to the development of innovative middleware that creates the same competitive risk to Microsoft that it faced from Navigator and Java in 1995.
31. No remedy can turn back the clock to 1995 and re-create the competitive threat that existed at that crucial time of technological disruption. Technological disruptions of the magnitude that Bill Gates called "the Internet tidal wave" cannot be created by judicial proceedings. Even so, one of the objectives of the remedies should be to attempt to restore, to whatever extent possible, the possibility of competition in the market where the illegal monopoly was maintained (i.e., the market for PC operating systems). The restrictions on Microsoft's behavior in the PFJ fall well short of this objective.
32. Following its years of illegal conduct, Microsoft's position in the core middleware products (Internet browsers and Java technology) is totally different today than it was in 1995. Microsoft has a dominant share of the browser market, IE has caught up to and surpassed Navigator's technical capabilities, and the prospect of large numbers of desktop applications written in "write once, run anywhere" Java seems remote.
33. There are two features of the industry that made the threat from Netscape and Java so significant. First, the technological disruption of the Internet made the functionality of the browser sufficiently important that it could become a platform for large numbers of applications. Second, the head start that Netscape and Java had over Microsoft middleware provided a substantial first-mover advantage, a particularly important element for competitive success in network industries prone to "tipping." Probably the only chance a competitor has to overcome the inherent advantages that Microsoft has in distribution is to create a large installed base of users before Microsoft can develop and launch a competitive product.
34. The market position that Microsoft has today makes it difficult for any set of conduct remedies to lead to significant middleware competition. Neither the PFJ nor any other set of conduct remedies can re-create the technological disruption or competitive head start that existed before Microsoft acted illegally. However, for the reasons explained below, the middleware remedies in the PFJ seem especially likely to be ineffective.
35. The PFJ relies heavily on competition in the OEM distribution channel as the key mechanism for overcoming the competitive harm created by Microsoft's actions. The same was true in the government's prior settlement with Microsoft, as I noted in my 1995 declaration:
36. Seven years later, it is clear that little was accomplished in the prior consent decree in relying on the OEM channel to facilitate competition in PC operating systems. Unimpeded access to this channel may indeed be necessary for effective competition. However, it is far from sufficient to create effective competition for middleware given the current state of the industry.
37. One obstacle to competition in middleware, which the PFJ does not address, is the applications barrier that now protects the position of Microsoft middleware. ISVs have a strong incentive to write applications to Microsoft middleware, since Microsoft middleware will be present on every Windows machine that is shipped. The PFJ does not restrict Microsoft's ability to commingle code and include middleware APIs in with its Windows operating system. The PFJ permits OEMs to remove Microsoft middleware icons, but the middleware itself, and its associated API set, will remain. Thus, the ubiquity of Microsoft's middleware will encourage ISVs to write applications to these APIs.
38. The PFJ restricts Microsoft's ability to discriminate against OEMs that also ship competing middleware, but this does not create an incentive for OEMs to ship competing middleware. For the reasons explained by the District Court and the Court of Appeals, OEMs are reluctant to include software that provides similar functionality to other software on the machine - it increases confusion among users and raises support costs.
39. If ISVs do not write applications to the competing middleware, OEMs will not distribute it. If OEMs do not distribute it, ISVs will not write applications to it. The current dominance of Microsoft middleware thus makes it very unlikely that this circle can be broken by the non-discrimination restrictions in the PFJ.
40. The PFJ also seeks to increase the role of OEMs in defining the Windows desktop. This is also insufficient to create significant middleware competition. Even if OEMs had complete control over the icons that would appear on the Windows desktop--and they would not under the PFJ--this would not alter in any way the software that would actually be present on the computer. Removing an icon from the desktop just removes the most obvious point of consumer access to the software, but the ability of ISVs to write to the APIs presented by the software remains unchanged.
41. The PFJ also attempts to prohibit Microsoft from discriminating against OEMs that distribute competing middleware. It does this by requiring Microsoft to provide uniform licensing terms to the 20 largest OEMs and preventing specific retaliation against OEMs that distribute competing middleware. It is not clear to me that these restrictions are sufficient to prevent Microsoft from exercising influence over the behavior of OEMs towards products that compete with Microsoft. First, I understand that the non-discrimination provisions apply only to certain Windows desktop operating systems (Windows XP and Windows 2000 Professional) and not to other Microsoft products that an OEM might purchase. Second, the relationships between Microsoft and OEMs are complex and multi-faceted. For example, Microsoft provides marketing and promotion support to OEMs; its provides technical assistance; its provides allowances for product development. Microsoft may provide these services differently to OEMs. Since the PFJ does not prohibit all forms of discrimination across OEMs, Microsoft may have sufficient ability to influence OEM decision-making.
42. The PFJ also contains limited disclosure requirements. The exact scope of these disclosures depends on careful interpretation of the complex language of the PFJ. I do not attempt such an interpretation but comment only on the limited impact of the disclosure remedies under any reasonable interpretation. There is a requirement to disclose interfaces that permit competing middleware to interoperate with Windows operating systems. I understand, however, that Microsoft is only required to make these disclosures if the interface is already in use by a Microsoft middleware product. A disclosure requirement limited in this manner pushes potential middleware competitors in the direction of "me too" products and does little to create incentives for significant innovation in middleware.
43. There are alternative middleware remedies that could have a more significant effect. More aggressive remedies with respect to that middleware threat would be open source Internet Explorer and a requirement for Microsoft to distribute the most current version of the standard Java runtime environment with IE and Windows. Even these remedies are likely to be insufficient to turn back the clock to the level of competition that existed before Microsoft's illegal conduct. But they are likely to have more impact than the remedies in the PFJ.
44. Open source IE is the most effective way to fully expose the links between IE and Windows as well as the IE APIs. This creates the possibility of interoperability between competing products and it furthers the possibility of operating system competition. It also allows anyone who wants to develop a competitive browser to be fully compatible with applications that are written to IE APIs. This way it limits the extension of the applications barrier to entry created by Microsoft's dominance in the browser.
45. The Java must-carry remedy works to erode the application barrier to entry by helping to overcome reluctance of ISVs to develop programs that require Java on the client. It is only by assuring sufficient ubiquity of Java and browser functionality that there is any chance that Microsoft may lose control of the applications barrier through competing middleware.
46. The applications barrier to entry identified by the D.C. Circuit consists in part of the large number of applications available on the Windows platform. As discussed above, successful entry in middleware of the type commenced by Netscape Navigator and Java could have substantially eroded the applications barrier to entry and facilitated entry into the operating systems market.
47. Microsoft controls the most economically important set of applications in its Microsoft Office suite. Office accounts for nearly 30% of Microsoft's annual revenue.8 Software suites consisting of personal productivity applications such as word processing, spreadsheets, presentation software, electronic mail, and calendar and contact management constitute a distinct and relevant product market. Microsoft's share of that market today is in the mid-90s9 and Microsoft almost certainly holds substantial market power.
48. As found by the D.C. Circuit, Microsoft has used its control over Office to maintain its OS monopoly. Microsoft threatened to cancel the Macintosh version of Office if Apple did not distribute Internet Explorer, Microsoft's Interact browser. It is clear that Microsoft's ability to make such threats would be diminished if Microsoft had an obligation to license the rights to port Office to competing OS platforms.
49. Since remedies focused entirely on middleware will not re-create the threat to Microsoft's monopoly power in PC operating systems that existed prior to Microsoft's illegal conduct, additional actions need to be taken to ensure that Microsoft does not benefit from its illegal conduct. These additional actions should be targeted at further reducing the underlying source of Microsoft's market power, namely the applications barrier to entry. Porting Office to other platforms would be a remedy of this type that could have a significant impact on the applications barrier. One factor that limits the demand for Unix workstations, which have computational advantages over Intel-based PCs, is the inability to interoperate with Office. The thin-client model of computing, where most computing occurs on the server, not the client, represents one of the most important threats to Windows desktop computing. The switching costs of adopting new personal productivity software with files not compatible with Office represents a significant barrier to Unix-based thin client networks. A requirement to license the rights to port Office may be one of the most effective ways to create competition for Windows, something which can probably no longer be achieved by remedies exclusively related to middleware.
50. The remedies in the PFJ are too limited in scope to re-create past competitive conditions even if they are enforced perfectly. However, the enforcement mechanisms in the PFJ are far from perfect and will likely lead to delays and costs that further limit the effectiveness of the remedies. The PFJ relies on a technology committee to oversee Microsoft's compliance with the PFJ. The membership in the committee is controlled 50% by the company whose past illegal activities have been the subject of the Circuit Court's decision. The committee lacks both resources and the power to enforce the PFJ. The committee must rely on information provided to it by Microsoft and has little ability to engage in its own investigations. Furthermore, if it uncovers a violation, it must rely on lengthy litigation to enforce it.
51. The implication is that failures by Microsoft to comply may go undetected and if they are detected, it may take a great deal of time and effort to impose a change on Microsoft's behavior. Delays can greatly limit the effectiveness of any particular remedy in a dynamic industry subject to network effects. If enforcement will be ineffective, it may create an incentive for Microsoft to violate the terms of the decree.
52. Other consent decrees have used special masters with sufficient resources and expedited judicial review to enforce their terms. Given the complex, dynamic nature of the software industry, it is especially important that the resources are in place to monitor the terms of the decree and that swift enforcement is possible.
53. The PFJ focuses on the PC desktop as the central space in which competition will take place going forward. It does this by creating limited new operating rights for OEMs coveting the appearance of the desktop and greater protections for installing middleware that competes with Microsoft. As I have discussed above, given the substantial advantages in middleware that Microsoft has through its illegally maintained monopoly, I think that it is unlikely that these desk-top-oriented remedies will spur economically meaningful entry in middleware and that there is therefore little reason to think that those remedies will re-create the competitive risk Microsoft's desktop monopoly faced from middleware entrants in 1995.
54. The PFJ therefore needs to be augmented with remedies that take a forward-looking approach. The PFJ needs to focus on the current and future threats to Microsoft's market power and ensure that Microsoft is not allowed to use its illegally maintained monopoly in PC operating systems to dilute these current and future competitive threats. A PFJ focused on desktop remedies not only will not jump start competition now, but by allowing Microsoft to keep the benefits of its illegal activities, such remedies will fail to deter future illegal anticompetitive actions by Microsoft. Instead, additional remedies should naturally be directed at ensuring competition going forward uninfected by Microsoft's illegally maintained monopoly. In particular, these remedies should seek to re-create the same risks faced by Microsoft in 1995 when the middleware threat arose. "
55. A forward-looking remedy should seek to limit Microsoft's ability to use its illegally maintained monopoly power to bias competition in complementary products that have the potential to develop into substitutes for desktop computers. Server operating systems and Web services are two prime examples. These products intersect at the middle of two related trends. To date, the Internet has been a PC Interact. Most Interact users access the Internet through a PC or workstation. The first trend is a probable shift to the use of many devices to access the Interact, including cell phones, handhelds such as the Palm Pilot and other personal digital assistants, and thin clients. As these devices themselves are not as powerful as a typical PC, they will demand more work from the servers and sewer operating systems delivering the information. The implication is that, in the future, a significant amount of computing will bypass the desktop -- which in turn implies that Microsoft has an incentive (if it can) to extend its monopoly from the desktop into servers.
56. The second trend is a related shift in how software is owned and managed. Prior to the Internet, PC software and content was largely locally owned and locally managed. The software was installed directly on the user's PC, from a floppy disk and then later a CO. The rise of the Interact makes it possible to move the location of software off of the PC and onto a remote device--a server--with much of the work done remotely. This gives rise to the generalized notion of a web service, where software is no longer a thing like a CD but instead a service delivered to a connecting device, much the way electricity is delivered to many devices.
57. On November 29, 2001, Steve Ballmer, Microsoft's CEO, discussed these trends and how Microsoft was approaching them through its .NET initiative:10
58. Ballmer also discussed the Microsoft business model and how .NET fits within it.
He sees Microsoft as targeted on seven business areas, including, unsurprisingly, PC operating systems, PC productivity solutions "anchored" by Office, and server software for building and deploying these applications. All of these are now being organized around .NET:
59. A computing world in which Web services, hosted on servers, are delivered on demand over the Internet is a world that has negative implications for Microsoft's near-monopoly in desktop operating systems. In such a world, there is no longer the same need for desktop computers to have "fat" operating systems such as Windows. In many respects, the Web services model is simply a more developed version of the thin-client, "network computer" model advocated by Oracle and Sun in the mid/late-1990s. As such, the Web services model is a threat to Microsoft's desktop monopoly and Microsoft therefore has an incentive (if it can) to use its existing monopoly to gain control over this possible threat. It has an incentive to ensure that Windows remains at the center of the Web services model and/or to migrate its monopoly from the desktop to Web services.
60. Microsoft's illegally maintained monopoly in the market for PC operating systems provides it with important advantages in server operating systems, in particular operating systems for workgroup servers. Workgroup servers are the servers in a "client-server" network that interoperate directly with desktop clients. Workgroup servers provide services such as authentication and authorization, directory, and file and print. Very importantly, they are also the point of contact or gateway between an organization's network of servers and the Interact. Workgroup servers are distinct from enterprise servers, which are more powerful, reliable and expensive servers that handle databases and other "mission critical" applications.
61. Some of Microsoft's advantages in workgroup server operating systems arise because of the distribution advantage provided by its monopoly in PC operating systems. Suppose a vendor of workgroup operating systems develops a new feature (such as a new directory service for keeping track of the users and resources on a network or a new security system for authentication and authorization). In the usual case, the network cannot make use of the new service in a server operating system unless certain new code (supplied by the vendor of the server operating system) is also installed on the clients in the network. In large networks, this can be a costly and time-consuming exercise - unless the network is running Windows on its servers. A network that runs Windows on its servers does not face this kind of problem because Microsoft ensures that the client-side pieces of server-side technologies are built into its Windows desktop operating system. This gives Microsoft a competitive advantage over other vendors of workgroup server operating systems. But it is an advantage that derives from Microsoft's illegally maintained monopoly in PC operating systems. Moreover, there may be significant long-run costs through the adverse effect that Microsoft's distribution advantages (derived from its illegally maintained monopoly in desktop operating systems) may have on incentives to invest in server-side innovation.
62. There are other ways in which Microsoft's past illegal conduct has provided it with advantages today in the market for workgroup server operating systems - advantages that help protect and enhance Microsoft's existing market power. For example, one of the benefits to Microsoft from the defeat of Netscape's browser was the resulting reduction in demand for Netscape application programs for servers. These server-side applications were designed to interoperate with the Netscape browser and certain client-side applications, such as e-mail, written to the Netscape Navigator APIs. Unlike Microsoft's server-side applications (such as Exchange) that run only on Windows, Netscape's server-side applications were implemented on multiple platforms, including Unix and Novell's NetWare. As Netscape's share of the browser market declined following Microsoft's illegal conduct, the demand for Netscape's server applications also declined. Thus a consequence of Microsoft's illegal conduct has been an increase in the demand for Microsoft server-side applications such as Exchange that, as mentioned above, run only on Windows server operating systems. Put differently, Microsoft's past illegal conduct towards Netscape is helping Microsoft establish an applications barrier that will protect and enhance its future position in the market for workgroup server operating systems.
63. Another way in which Microsoft's past illegal conduct affects the market for workgroup operating systems today involves distributed application programs. As I mentioned before, Java is a programming language with features that I understand make it well suited for distributed applications, i.e., applications that call upon resources located on multiple different computers located around a network. As I understand it, for distributed applications to work, they need to conform to a particular set of protocols, and these protocols need to be supported by the operating systems of the computers involved in executing the distributed application. Java had protocols for distributed applications (RMI and CORBA) that were supported by multiple operating systems. Microsoft had an alternative, proprietary set of protocols called DCOM. By interfering with the development of cross-platform Java, Microsoft gave an advantage to its framework for distributed applications (DCOM) and promoted the development of distributed applications written to protocols that run only on Windows operating systems. In addition, since the programs that are written to these Microsoft protocols are targeted for computers using the Windows operating system, such programs also make use of Windows APIs. This means that even if rival operating systems were given the ability to support DCOM, they could not run most of the distributed applications written to this protocol because these applications also make use of Windows APIs. Thus this is another example of how Microsoft's past illegal conduct, this times towards Java, is helping Microsoft establish an applications barrier that will protect and enhance its future position in the market for server operating systems.
64. Microsoft's past illegal conduct has also given it advantages today in Web services. For example, one of the Web services that Microsoft has promoted heavily is Passport, its Internet authentication and authorization service. In a network environment, key issues are verifying the identity of users or computers ("who are you?") and determining the resources to which you are entitled to have access ("what are you authorized to do?"). Passport is an authentication and authorization service targeted, at least initially, at e-commerce. Consumers who subscribe to Microsoft's Passport service will have their name and credit card information on file on servers controlled by Microsoft. E-commerce vendors who participate in Passport will have back office connections with the Microsoft servers so that, when a consumer who subscribes to Passport wants to purchase something, the e-commerce vendor can check with Microsoft's Passport servers to authenticate and authorize the purchase (and debit the consumer's credit card). The theory is that Passport will simplify e-commerce transactions.
65. For Passport to be successful, Microsoft needs to have a large base of consumers who subscribe to the service. A large base of consumers will make firms engaged in e-commerce interested in joining Passport on the vendor side, which in turn will make Passport more attractive to consumers. Thus there are potential network effects which, if they get started, may result in Passport being in the middle of a very large volume of Internet transactions.
66. Microsoft is actively using its illegally maintained monopoly in PC operating systems as a vehicle for enrolling consumers in Passport. Every time a consumer boots up a new copy of Windows, the consumer is asked multiple times whether he or she would like to sign up with Passport. In addition, the consumer is told that he or she will not receive information about product upgrades unless the consumer signs up for Passport. Thus this is an example in which Microsoft is using the distribution advantages that it has by virtue of its illegally maintained monopoly in PC operating systems to gain advantages in Web services. In so doing, Microsoft helps protect its existing monopoly power and/or helps migrate its market power from the desktop to Web services.
67. The implications of these trends are significant. Microsoft's monopoly in desktop operating systems provides it with advantages in adjacent markets that Microsoft is able to use to protect and enhance its illegally maintained monopoly power. By migrating its monopoly from desktop operating systems into server operating systems and Web services, Microsoft can help ensure that its future market power is comparable to (or greater than) the market power it possessed when the desktop was the principal hub of computing activity.
68. Given these links between Microsoft's past illegal conduct and Microsoft's future market power, an appropriate remedy should be focused on limiting Microsoft's ability to use its illegally maintained monopoly to gain advantages in products in other markets that have the potential to become substitutes for the Windows desktop operating system. Disclosure remedies have the potential to be an important step in this direction. For example, if Microsoft were required to fully disclose the interfaces and protocols used by its server and client operating systems, then vendors of non-Microsoft server operating systems could design their products so that they could interoperate smoothly in networks populated by Windows clients and servers. The resulting competition among vendors of server operating systems would help ensure that servers remain a threat to Microsoft's illegally maintained monopoly in desktop operating systems.
69. The PFJ does, not ignore completely issues related to adjacent markets. The PFJ does require disclosure for communication protocols that allow for servers to interoperate with Windows operating systems. This requirement, in contrast with the other provisions of the PFJ, appears to focus more on the server operating system market than competition in middleware. I understand, however, that the disclosure requirements proposed in the PFJ are exceedingly narrow and ultimately inadequate to allow full and equal interoperability for competitive server operating systems or Web services architectures.
70. In designing disclosure remedies (or any other remedy), it is important to remember that one is try to cure the consequences of past illegal conduct. As a result, there is no reason to be troubled by remedies that impose obligations that one would be reluctant to impose on other firms. Against this background, it seems reasonable to consider a remedy that requires disclosure sufficient to allow competitive products to interoperate with Microsoft software on an equal basis as Microsoft's own products. It is not clear that even this would be enough to offset the advantages that Microsoft has gained for itself in adjacent markets through past illegal conduct and which serve to protect and enhance its existing market power. But it scans like a reasonable step.
71. As the D.C. Circuit found, Microsoft violated Sec. 2 of the Sherman Act in impermissibly maintaining its monopoly through actions designed to eliminate the threat to that monopoly posed in the mid 1990s by competition from Netscape Navigator and Java middleware. Given that finding, the remedies in this case should eliminate the benefits to Microsoft of its illegal conduct; should restore, if possible, the possibility of competition in operating systems; and should not allow Microsoft to protect its illegally maintained monopoly from current and future competition in related markets, such as server operating systems and Web services. In my opinion, the PFJ fails to accomplish these objectives.
72. The PFJ focuses on the desktop and on re-creating the possibility for middleware competition by giving OEMs freedom with regard to icon display and more limited freedom in installing and using non-Microsoft middleware. In doing so, it ignores the reality that Microsoft's market position in browsers and other middleware is substantially stronger today than it was in 1995. I know of no competing middleware today--and none is suggested in the Competitive Impact Statement--that begins to enjoy the time-to-market and market presence advantages held by Netscape Navigator and Java in the mid-1990s. The PFJ does nothing to address the powerful distributional advantage that Microsoft alone has and which ensures that its middleware will be ubiquitous. That ubiquity operates as an unchecked barrier to entry and reduces the incentive for others to create innovative, competitive middleware. I therefore see no reason to think that the PFJ will succeed in spurring a new middleware threat to the Microsoft operating system or in denying Microsoft the fruits of its illegally maintained monopoly.
73. The PFJ ignores remedies that could have a more significant effect in middleware markets, in particular, remedies that require Internet Explorer to be open source and that require Microsoft to distribute the most current version of the Java runtime environment with IE and Windows. Although these remedies are unlikely to fully restore the competitive threat posed by middleware before Microsoft's illegal activities took place, these remedies would likely have a greater impact than those set forth in the PFJ.
74. More fundamentally, the PFJ does nothing to address the applications barrier to entry that defines Microsoft's monopoly in PC operating systems. Microsoft also controls the most economically important set of applications for Windows through its control over Microsoft Office. As the D.C. Circuit found, Microsoft used that control to protect its operating system monopoly through threats against Apple. It is clear that Microsoft's ability to make such threats would be diminished if Microsoft has an obligation to license the rights to port Office to competing operating systems. Indeed, porting Office to other operating systems is a remedy that could have a significant impact on the applications barrier to entry.
75. In addition, the PFJ should focus on the current and future threats to Microsoft's market power and ensure that Microsoft cannot use its illegally maintained monopoly to stifle such threats. This ease makes clear that those threats are likely to come from products that are complements to Windows in the short run and potential competitors in the long run. That was precisely the position of Netscape Navigator and Java in 1995; today, based on Microsoft's?? public statements, that may be the position of server operating systems and Web services. Both of these represent a move away from a computing structure organized around desktop computers using "fat" operating systems such as Windows. Server operating systems and Web services represent an evolution of the thin-client model of computing, and as such, represent a threat to Microsoft's desktop monopoly. Microsoft is currently attempting to defeat this threat by using its illegally maintained monopoly in PC operating systems as a vehicle for expanding its market share in servers and attaching consumers to its Web services infrastructure. The PFJ is missing forward-looking remedies that address such efforts by Microsoft to protect and enhance its existing market power by using its illegally maintained monopoly in PC operating systems to defeat competitive threats in adjacent markets. This is a significant hole in the PFJ that bears on the future of competition in the computing industry.
I hereby affirm under penalty of perjury that the foregoing is true and correct to the best of my knowledge, information and belief. Executed this 25th day of January, 2002 in Palo Alto, California.
| |
__________________________
Kenneth J. Arrow |
ATTACHMENT A FOOTNOTES
1 "A Software Giant's March Onto the Internet," New York Times (Jan. 12, 1998) at C4.
2 "Browser Usage: How It's Trending," Interactive Age (Jul. 31, 1995) (citing figures compiled by Interse Market Focus).
3 "Microsoft v Netscape: Freer than Free," The Economist (Aug. 17, 1996, U.S. Edition).
4 Dataquest, "All Platform Operating Systems Sales History and Forecast Summary," Table 12 (Mar. 1997).
5 "Microsoft v Netscape: Freer than Free," The Economist (Aug. 17, 1996, U.S. Edition).
6 IDC, "'Worldwide Client and Server Operating Environments, Market Forecast and Analysis, 2001-2005" (Aug. 2001).
7 "AOL Files Suit Against Microsoft For Damages Inflicted on Netscape," Wall Street Journal (Jan. 23, 2002) (citing data compiled by WebSideStory, a market research firm).
8 Dresdner Kleinwort Wasserstein, "Microsoft Corporation," Figure 4 (1 Aug. 2001).
9 In 1999, Microsoft accounted for 96.1% of the revenues of office suites designed for Windows. Since 98.1% of all sales of office suites in 1999 were for the Windows platform, these figures by themselves imply an industry share of 94%. But Microsoft also accounted for a large share of the revenues of office suites designed for Apple's Macintosh OS -- a platform that accounted for nearly all of the non-Windows sales of office suites. IDC Office Suite Market Review and Forecast, 1998-2003 (Aug. 1999).
10 S. Ballmer speech, Credit Suisse First Boston Technology Conference (Nov. 29, 2001) (http://www.microsoft.com/msft/speech/BallmerCSFB112901.htm).
BIOGRAPHICAL SKETCH
KENNETH J. ARROW
Personal
Born: 23 August, 1921
Wife's name: Selma
Children: David Michael and Andrew Seth
Education
B.S. in Social Science, City College, New York, 1940. Major: Mathematics.
M.A., Columbia University, 1941. Field: Mathematics.
Ph.D., Columbia University, 1951. Field: Economics.
Positions
Captain, U. S. Army Air Corps, 1942-46 (Weather Officer).
Research Associate, Cowles Commission for Research in Economics, 1947-49.
Assistant Professor of Economics, University of Chicago, 1948-49.
Consultant, the RAND Corporation, 1948-date.
Acting Assistant Professor of Economics and Statistics, Stanford University, 1949-50.
Associate Professor of Economics and Statistics, Stanford University, 1950-53.
Professor of Economics, Statistics, and Operations Research, Stanford University, 1953-68
Economist, Council of Economic Advisers, U. S. Government, 1962.
Visiting Professor of Economics, Massachusetts Institute of Technology, Fall, 1966.
Fellow, Churchill College (Cambridge, England), 1963-64, 1970, 1973, 1986.
Guest Professor, Institute for Advanced Studies, Vienna, June 1964, June 1970.
Professor of Economics, Harvard University, 1968-74.
James Bryant Conant University Professor, Harvard University, 1974-79.
Joan Kenney Professor of Economics and Professor of Operations Research, Stanford University, 1979 to 1991.
Senior Fellow by Courtesy, Hoover Institution on War, Revolution and Peace, 1981-94.
Part-time Professor, European University Institute, 1986.
External Professor, Santa Fe Institute, 1988 to date.
Joan Kenney Professor of Economics Emeritus and Professor of Operations Research Emeritus, 1991 to date
Fulbright Professor, University of Siena, Spring 1995.
Visiting Fellow, All Souls College (Oxford, England), 1996.
University and Faculty Administration at Stanford University
Executive Head, Department of Economics, 1953-6
Member and Chair, Executive Committee of the Academic Council
Acting Executive Head, Department of Economics, 1962-3
Member and Chair, Advisory Board
Member and Chair, Senate of the Academic Council
Director, Stanford Institute for Theoretical Economics, 1993-98
Director, Stanford Center on Conflict and Negotiation, 1993-5
Honors and Awards
Gold Pell Medal (highest grades), City College, New York, 1940.
Phi Beta Kappa.
Social Science Research Fellow, 1952.
Fellow, Center for Advanced Study in the Behavioral Sciences, 1956-57.
John Bates Clark Medal, American Economic Association, 1957.
LL.D. (honorary), University of Chicago, 1967.
M.A. (honorary), Harvard University, 1968.
Marshall Lecturer, Cambridge University, Spring 1970.
D.Soc/Eco.Sci. (honorary), University of Vienna, 1971.
LL.D. (honorary), City University of New York, 1972.
Nobel Memorial Prize in Economic Science, 1972.
John R. Commons Lecture Award, Omicron Delta Epsilon, 1973.
D.Sci. (honorary), Columbia University, 1973.
D.Soc.Sci. (honorary), Yale University, 1974.
Dr. (honorary), Universite Rene Descartes, 1974.
LL.D. (honorary), Hebrew University of Jerusalem, 1975.
LL.D. (honorary), University of Pennsylvania, 1976.
D.Pol.Sci. (honorary), University of Helsinki, 1976.
Member, National Academy of Sciences (Chairman, Section 54, 1976-1979, Council member 1990 to date).
Fellow, American Academy of Arts and Sciences (Vice President, 1979-80, 1991-94).
Member, American Philosophical Society.
Member, Institute of Medicine.
Foreign Honorary Member, Finnish Academy of Sciences.
Corresponding Member, British Academy.
Sigma Xi (President, Stanford Chapter, 1981-82).
Tanner Lecturer, Oxford University, Spring 1983.
2nd Class Order of the Rising Sun, Japan, 1984.
Tanner Lecturer, Harvard University, Spring 1985.
Dr. of Letters, University of Cambridge, 1985.
Dr. Honoris Causa, Universite d'Aix-Marseille III, 1985.
von Neumann Prize of The Institute of Management Sciences and the Operations Research Society of America, 1986.
LL.D. (honorary), Washington University in St. Louis, 1989.
Clarendon Lectures, Oxford University, November 1989.
LL.D. (honorary), Ben-Gurion University of the Negev, 1992.
Member, Pontifical Academy of Social Sciences
Laurea (honoris causa) Universita Cattolica del Sacro Cuore (Milan)
Dr. (hon causus) University of Uppsala, 1995.
Publication of Enduring Quality Award 1995, Association of Environmental and Resource Economics (with Anthony C. Fisher)
Kampe de Feriet Award (Information Processing for Management under Uncertainty), 1998
Medal of the University of Paris, 1998
Dr. (hon.) University of Buenos Aires, 1999
LL.D. (hon.) Harvard University, 1999
Dr. (hon. Causus) University of Cyprus, 2000.
50th Anniversary Medal, School of Humanities, Arts, and Social Sciences, Massachusetts Institute of Technology
Ph.D. (h.c.) University of Tel Aviv, 2001
Professional Societies
Econometric Society (Fellow; Vice President, 1955, President, 1956, Member of the Council, 1983).
Institute of Mathematical Statistics (Fellow).
American Statistical Association (Fellow).
American Economic Association (Member, Executive Committee, 1967-1969; President-elect, 1972; President, 1973; Distinguished Fellow).
The Institute of Management Sciences (President, 1963; Chairman of the Council, 1964).
Western Economic Association (President, 1980-1981).
American Association for the Advancement of Science (Fellow; Chair, Section K, 1982).
International Society for Inventory Research (President, 1983-1988).
Honorary President, International Economic Association; President 1983-1986; Member, Executive Committee, 1986-1992.
The Society for Social Choice and Welfare, Caen, France, First President, 1992-93.
Economists Allied for Arms Reduction, Co-Chair, 1990-1995
Business Positions
Member, Board of Directors, Varian Associates, Inc., 1973-1991
Member, Board of Directors, Abt Associates, Inc., 1975-1985
Member, Board of Directors, Fireman's Fund Insurance Company, 1980-1991
Member, Board of Directors, Strategies for a Global Environment, Inc., 1998-
Member, Board of Directors, Unext, Inc., 2000-
PUBLICATIONS OF KENNETH J. ARROW
BOOKS
1. [1951] Social Choice and Individual Values. New York: Wiley.
2. [1958] (with S. Karlin and H. Scarf) Studies in the Mathematical Theory of Inventory and Production. Stanford, California: Stanford University Press.
3. [1958] (with L. Hurwicz and H. Uzawa) Studies in Linear and Non-Linear Programming. Stanford, California: Stanford University Press.
4. [1959] (with M. Hoffenberg and the assistance of H. Markowitz and R. Shephard) A Time Series Analysis of Interindustry Demands. Amsterdam: North-Holland Publishing Co.
5. [1963] Social Choice and Individual Values. Wiley: New York, 2nd edition.
6. [1965] Aspects of the Theory of Risk-Bearing. Yrjo Jahnssonin saatio Helsinki, Finland.
7. [1970] (with M. Kurz) Public Investment, the Rate of Return, and Optimal Fiscal Policy. Baltimore and London: The Johns Hopkins Press.
8. [1971] (with F. H. Hahn) General Competitive Analysis. San Francisco: Holden-Day; Edinburgh: Oliver & Boyd.
9. [1971] Essays in the Theory of Risk-Bearing. Chicago: Markham; Amsterdam and London: North-Holland.
10. [1974] The Limits of Organization. New York: W. W. Norton.
11. [1976] (with S. Shavell and J. Yellen) The Limits of the Market Economy, (in Japanese). Memorandum for Ministry of International Trade and Industry, Japan.
12. [1976] The Viability and Equity of Capitalism. E. S. Woodward lecture, Department of Economics, University of British Columbia.
13. [1977] (with L. Hurwicz) Studies in Resource Allocation Processes. Cambridge, London, New York, and Melbourne: Cambridge University Press.
14. [1983] Collected Papers of Kenneth J. Arrow, Volume 1, Social Choice and Justice. Cambridge, Massachusetts: The Belknap Press of Harvard University Press.
15. [1983] Collected Papers of Kenneth J. Arrow, Volume 2, General Equilibrium. Cambridge, Massachusetts: The Belknap Press of Harvard University Press.
16. [1984] Collected Papers of Kenneth J. Arrow, Volume 3, Individual Choice under Certainty and Uncertainty. Cambridge, assachusetts: The Belknap Press of Harvard University Press.
17. [1984] Collected Papers of Kenneth J. Arrow, Volume 4, The Economics of Information. Cambridge, Massachusetts: The Belknap Press of Harvard University Press.
18. [1985] Collected Papers of Kenneth J. Arrow, Volume 5, Production and Capital. Cambridge, Massachusetts: The Belknap Press of Harvard University Press.
19. [1985] Collected Papers of Kenneth J. Arrow, Volume 6, Applied Economics. Cambridge, Massachusetts: The Belknap Press of Harvard University Press.
20. [1986] (with Herve Raynaud) Social Choice and Multicriterion Decision-Making. Cambridge, Massachusetts: The MIT Press.
22. [2000] Theorie de l'information et des organisations. Edited by T. Granger. Paris: Dunod.
BOOKS EDITED
1. [1960] (with S. Karlin and P. Suppes) Mathematical Methods in the Social Sciences, 1959: Proceedings of the First Stanford Symposium. Stanford, California: Stanford University Press.
2. [1962] (with S. Karlin and H. Scarf) Studies in Applied Probability and Management Science. Stanford, California: Stanford University Press.
3. [1969] (with T. Scitovsky) Readings in Welfare Economics. American Economic Association Series of Republished Articles in Economics. Homewood, Illinois: Richard D. Irwin, Vol. XII.
4. [1971] Selected Readings in Economic Theory from Econometrica. Cambridge, Massachusetts, and London: MIT Press.
5. [1978] (with S. J. Fitzsimmons and R. Wildenmann) Zukunftsorientierte Planung und Forschung fur die 80er Jahre. Koningstein/Ts., German Federal Republic: Athenaum Verlag.
6. [1981] (with C. C. Abt and S. J. Fitzsimmons) Applied Research for Social Policy: The United States and the Federal Republic of Germany. Cambridge, Massachusetts: Abt.
7. [1981] (with M. Intriligator) Handbook of Mathematical Economics, Volume I. Amsterdam, New York and London: North-Holland.
8. [1982] (with M. Intriligator) Handbook of Mathematical Economics, Volume 11. Amsterdam, New York and London: North-Holland.
9. [1985] (with Seppo Honkapohja) Frontiers of Economics. Oxford and New York: Basil Blackwell Ltd.
10. [1986] (with M. Intriligator) Handbook of Mathematical Economics, Volume III. Amsterdam, New York and London: North-Holland.
11. [1988] (with M. J. Boskin) The Economics of Public Debt. Basingstoke and London: Macmillan in association with The International Economic Association.
12. [1988] (with P. W. Anderson and D. Pines) The Economy as an Evolving Complex System. Redwood City, California: Addison-Wesley.
13. [1988] The Balance between Industry and Agriculture in Economic Development. Volume 1: Basic Issues. Basingstoke and London: Macmillan in association with The International Economic Association.
14. [1991] Issues in Contemporary Economics. Volume I, Markets and Welfare. Basingstoke and London: Macmillan for International Economic Association.
15. [1994] (with R. Arnott, A.B. Atkinson, and J. Dreze) Public Economics, by William Vickrey. Cambridge, U.K., New York, and Oakleigh, Victoria: Cambridge University Press.
16. [1995] (with R.H. Mnookin, L. Ross, A. Tversky, and R. Wilson) Barriers to Conflict Resolution. New York and London; W.W. Norton.
17. [1996] (with E. Colombatto, M. Perlman, and C. Schmidt) The Rational Foundations of Economic Behavior. Basingstoke and London: Macmillan for the International Economic Association.
18. [1996] (with R.W. Cottle, B.C. Eaves and I. Olkin) Education in a Research University. Stanford, CA: Stanford University Press.
19. [1996-7] (with Amartya Sen and Kotaro Suzumura) Social Choice Re-examined. Basingstoke and London: MacMillan in association with the International Economic Association. 2 vol.
20. [1998] (with Yew-Kwang Ng and Xiaokai Yang) Increasing Returns and Economic Progress. Basingstoke, UK: Macmillan, and New York: St. Martin's.
22. [2000] (with S. Bowles and S. Durlauf) Meritocracy and Economic Inequality. Princeton, NJ: Princeton University Press.
23. [2001] (with G. Debreu) Landmark Papers in General Equilibrium Theory, Social Choice, and Welfare Economics. Cheltenham, UK, and Northampton, MA: Edward Elgar.
COLLECTIVE STUDIES
1. [1971] (as member of Climatic Impact Committee of the National Research Council, National Academy of Sciences, National Academy of Engineering) Environmental Impact of Stratospheric Flight. Washington, D. C.: National Academy of Sciences.
2. [1977] (as member of Nuclear Energy Policy Study Group) S. M. Keeny, Jr., et al, Nuclear Power Issues and Choices. Cambridge, Massachusetts: Ballinger.
3. [1979] H.H. Landsberg, et al, Energy: The Next Twenty Years. Cambridge, Massachusetts: Ballinger.
4. [1981] (as Chairman of the Committee for a Planning Study for an Ongoing Study of Costs of Environment-related Health Effects, Institute of Medicine) Costs of Environment-related Health Effects. Washington, D. C.: National Academy Press.
5. [1991] (as member of the Oversight Review Board of the National Acid Precipitation Assessment Program) The Experience and Legacy of NAPAP. Washington, DC: National Acid Precipitation Assessment Program.
6. [1993] (as Co-chair) Report of the NOAA [National Oceanic and Atmospheric Administration] Panel on Contingent Valuation. Federal Register, 58, No. 10 (January 15, 1993): 4602-4614.
7. [1995] (with B. Bolin, R. Constanza, P. Dasgupta, C. Folke, C.S. Holing, B.-O. Jansson, S. Levin, K.-G. Maler, C. Perrings, and D. Pimentel) Economic growth, carrying capacity, and the environment. Science 268.28 April 1995, 520-521.
8 [1996] (with M.L. Cropper, G.C. Eads, R.W. Hahn, L.B. Lave, R.G. Noll, P.R. Portney, M. Russell, R. Schmalensee, V.K. Smith, and R.N. Stavins) Benefit-Cost Analysis in Environmental, Health, and Safety Regulations: A Statement of Principles. La Vergne, TN: The AEI Press, c/o Publisher Resources, Inc.
9 [2000] (with G. Daily, P. Dasgupta, S. Levin, K.-G. Maler, E. Maskin, D. Starrett, T. Sterner, and T. Tietenberg) Managing ecosystem resources. Environmental Science and Technology 34: 1401-1406.
NONTECHNICAL ARTICLES
1. [1961] "Does the Majority Ever Rule?" introductory notes. Portfolio and Art News Annual 4:76-78.
2. [1974] "Taxation and Democratic Values." The New Republic 171:18:23-25.
3. [1975] "How Much to Fear from OPEC?" Moment 1:2:32-34.
4. [1978] "Capitalism, Socialism, and Democracy," (symposium). Commentary 65:4:29-31.
5. [1978] "A Cautious Case for Socialism." Dissent, Fall, 472-480.
6. [1979] "The Economy and the Economist." Partisan Review 1:113-116.
7. [1981] "Two Cheers for Regulation." Harper's 262:18-22.
8. [1982] "Why People Go Hungry." New York Review of Books 29:12:24-26.
9. [1983] "The Economics of 1984." In P. Stansky (ed.) On Nineteen Eighty-Four. San Francisco: W.H. Freeman, pp. 43-48.
10. [1984] "The International Economic Order of the Twenty-First Century." In Osaka Junior Chamber, Inc., Wisdom Toward the 21st Century. Tokyo: YMCA Press, pp. 173-227 (in Japanese).
11. [1984] "The Economy as Order and Disorder." In P. Livingston (ed.) Disorder and Order. Saratoga, California: ANMA Libri., pp. 162-172.
12. [1986] "Kenneth J. Arrow." In W. Breit and R. W. Spencer (eds.) Lives of the Laureates: Seven Nobel Economists. Cambridge, Massachusetts, and London, pp. 43-57.
13. [1987] "Redistribution to the Poor: A Collective Expression of Individual Altruism." In F. Jimenez (ed.) Poverty and Social Justice. Tempe, Arizona: Bilingual Press, pp. 39-46.
14. [1989] "The Multiple Responsibilities of the Corporation." In J. E. Weiler (ed.), The First International Symposium on Stakeholders. Dayton, Ohio: Center for Business and Economic Research, School of Business Administration, University of Dayton, pp. 53-62.
15. [1989] Chapter 1. In W. Sichel (ed.) The State of Economic Science. Kalamazoo, Michigan: W.E. Upjohn Institute for Employment Research.
16. [1991] "Economic Forecasting." In G. E. Gaull (ed.) New Technologies and the Future of Food and Nutrition. New York: Wiley. Chapter 25, pp. 135-140.
17. [1992] "Decision Making by Individuals and Systems." In Office of Naval Research: Forty Years of Excellence. Arlington, Virginia: Office of Naval Research. Pp. 123-127.
18. [1992] "I Know a Hawk from a Handsaw." In M. Szenberg (ed.) Eminent Economists. Cambridge and New York: Cambridge University Press. Pp. 42-50.
19. [1992] "Moral Thinking and Economic Interaction." In Pontifical Council for Justice and Peace, Social and Ethical Aspects of Economics. Vatican City. Pp. 17-22.
20. [1994] "Gli Obblighi Etica del Mercato." Etica degli Affari e delle Professioni, VII: 1/94: 34-38.
21. [1996] "Environmental Aspects of Environmental Challenges," in H.W. Kendall et. al., Meeting the Challenges of Population, Environment, and Resources: The Costs of Inaction. Washington, D.C.: The World Bank. Environmentally Sustainable Development Proceedings Series No. 14, pp. 29-31.
22. [1996] What Does the Present Owe the Future: An Economic and Ethical Perspective on Climate Change. Grace A. Tanner Lecture on Human Values XVII. Cedar City, Utah: Southern Utah University.
23. [1998] Tribute to Michael Bruno. The Economic Quarterly 45:473-477 (in Hebrew).
24. [2000] Globalization and its implications for international security. ECAAR Bulletin 12(3): 1,7.
25. [2001] Is capitalism good for democracy? In J. Cohen and K. R Manning (eds.) Asking the Right Questions: A Colloquium Celebrating the 50th Anniversary. Massachusetts Institute of Technology, School of Humanities, Arts, and Social Sciences. Pp. 90-96.
26. [2001] John C. Harsanyi, 1920-2000. Biographical Memoirs of the National Academy of Sciences 80: 3-14.
27. [2001] Armen Alchian's contributions of NIE. Newsletter International Society for New Institutional Economics 3 (Number 2): 5-8.
PAPERS
1. [1949] On the Use of Winds in Flight Planning. Journal of Meteorology 6:150-159.
2. [1949] (with D. Blackwell and M. A. Girshick) Bayes and Minimax Solutions of Sequential Decision Problems. Econometrica 17:213-44.
3. [1950] Homogeneous Systems in Mathematical Economics: A Comment. Econometrica 18:60-62.
4. [1950] A Difficulty in the Concept of Social Welfare. Journal of Political Economy 58:328-46.
5. [1951] Alternative Proof of the Substitution Theorem for Leontief Models in the General Case. In T. C. Koopmans, (ed.) Activity Analysis of Production and Allocation. New York: Wiley, Chapter IX.
6. [1951] (with T. E. Harris and J. Marschak) Optimal Inventory Policy. Econometrica 19:250-72.
7. [1951] Alternative Approaches to the Theory of Choice in Risk-Taking Situations. Econometrica 19:404-37.
8. [1951] Little's Critique of Welfare Economics. American Economic Review 41:923-34.
9. [1951] Mathematical Models in the Social Sciences. In D. Lerner and H. D. Lasswell (eds.), The Policy Sciences. Stanford, California: Stanford University Press, pp. 129-54.
10. [1951] An Extension of the Basic Theorems of Classical Welfare Economics. In J. Neyman (ed.), Proceedings of the Second Berkeley Symposium on Mathematical Statistics and Probability. Berkeley and Los Angeles: University of California Press, pp. 507-32.
11. [1952] The Determination of Many-Commodity Preference Scales by Two-Commodity Comparison. Metroeconomica IV: 107-15.
12. [1952] Le principe de rationalite dans les decisions collectives. Economie Appliquee V:469-84.
13. [1953] Le role des valeurs boursieres pour la repartition la meilleure des risques, Econometrie. Colloques Internationaux du Centre National de la Recherche Scientifique, Vol. XI, pp. 41-47.
14. [1953] (with E. W. Barankin and D. Blackwell) Admissible Points of Convex Sets, Contributions to the Theory of Games, II. Princeton: Princeton University Press, pp. 87-91.
15. [1954] (with G. Debreu) Existence of Equilibrium for a Competitive Economy. Econometrica 22:265-90.
16. [1954] Import Substitution in Leontief Models. Econometrica 22:481-492.
17. [1956] (with L. Hurwicz) Reduction of Constrained Maxima to Saddle-Point Problems. In J. Neyman (ed.) Proceedings of the Third Berkeley Symposium on Mathematical Statistics and Probability. Berkeley and Los Angeles: University of California Press, Vol. V, pp. 1-20.
18. [1956] (with A. C. Enthoven) A Theorem on Expectations and the Stability of Equilibrium. Econometrica 24:288-93.
19. [1957] Statistics and Economic Policy. Econometrica 25:523-31.
20. [1957] (with L. Hurwicz) Gradient Methods for Constrained Maxima. Operations Research 5:258-65.
21. [1957] Decision Theory and Operations Research. Operations Research 5:765-74.
22. [1958] Utilities, Choices, Attitudes: A Review Note. Econometrica 26:1-23.
23. [1958] Tinbergen on Economic Policy. Journal of the American Statistical Association 53:89-97.
24. [1958] The Measurement of Price Changes. In Joint Economic Committee, The Relationship of Prices to Economic Stability and Growth. Washington, D.C.: U.S. Government Printing Office, pp. 77-88.
25. [1958] (with M. Nerlove) A Note on Expectations and Stability. Econometrica 26:297-305.
26. [1958] (with A. Alchian and W. M. Capron) An Economic Analysis of the Market for Scientists and Engineers. Santa Monica, California: The Rand Corporation, RM 2190-RC.
27. [1958] (with M. McManus) A Note on Dynamic Stability. Econometrica 26:448-54.
28. [1958] (with L. Hurwicz) On the Stability of the Competitive Equilibrium. Econometrica 26:522-52.
29. [1959] Toward a Theory of Price Adjustment. In M. Abramovitz and others, The Allocation of Resources. Stanford, California: Stanford University Press, pp. 41-51.
30. [1959] (with W. M. Capron) Dynamic Shortages and Price Rises: The Engineer-Scientist Case. Quarterly Journal of Economics 63:292-308.
31. [1959] Rational Choice Functions and Orderings. Economica, N. S. 26:121-27.
32. [1959] (with H. D. Block and L. Hurwicz) On the Stability of the Competitive Equilibrium, II. Econometrica 27:82-109.
33. [1959] Functions of a Theory of Behavior Under Uncertainty. Metroeconomica 11:12-20.
34. [1960] (with L. Hurwicz) Competitive Stability Under Weak Gross Substitutability: The "Euclidean Distance" Approach. International Economic Review 1:38-49.
35. [1960] Optimization, Decentralization, and Internal Pricing in Business Firms. In Contributions to Scientific Research in Management. Western Data Processing Center, Graduate School of Business Administration, University of California, Los Angeles, pp. 9-18.
36. [1960] Decision Theory and the Choice of a Level of Significance for the t-Test. In I. Olkin and others (eds.), Contributions to Probability and Statistics. Stanford, California: Stanford University Press. pp. 70-78.
37. [1960] The Work of Ragnar Frisch, Econometrician. Econometrica 28:175-92.
38. [1960] Price-Quantity Adjustments in Multiple Markets with Rising Demands. In K. J. Arrow, S. Karlin, P. Suppes (eds.) Mathematical Methods in the Social Sciences, 1959. Stanford, California: Stanford University Press, pp. 3-16.
39. [1960] (with L. Hurwicz) Decentralization and Computation in Resource Allocation. In R. W. Pfouts (ed.), Essays in Economics and Econometrics. Chapel Hill: University of North Carolina Press, pp. 34-104.
40. [1960] (with L. Hurwicz) Stability of the Gradient Process in N-Person Games. Journal of the Society for Industrial and Applied Mathematics 8:280-94.
41. [1960] (with L. Hurwicz) Some Remarks on the Equilibria of Economic Systems. Econometrica 28:640-46.
42. [1961] Additive Logarithmic Demand Functions and the Slutsky Relations. Review of Economic Studies 28:176-81.
43. [1961] (with H. B. Chenery, B. Minhas and R. M. Solow) Capital-Labor Substitution and Economic Efficiency. Review of Economics and Statistics 43:225-50.
44. [1961] (with L. Hurwicz and H. Uzawa) Constraint Qualifications in Maximization Problems. Naval Research Logistics Quarterly 8:175-91.
45. [1961] (with A. C. Enthoven) Quasi-Concave Programming. Econometrica 29:779-800.
46. [1962] Case Studies: Comment. In National Bureau of Economic Research, The Rate and Direction of Inventive Activity: Economic and Social Factors. Princeton: Princeton University Press, pp. 335-38.
47. [1962] Economic Welfare and the Allocation of Resources for Invention. In National Bureau of Economic Research, The Rate and Direction of Inventive Activity: Economic and Social Factors. Princeton: Princeton University Press, pp. 609-25.
48. [1962] Optimal Capital Adjustment. In K. J. Arrow, S. Karlin, and H. Scarf (eds.), Studies in Applied Probability and Management Science. Stanford, California: Stanford University Press, pp. 1-17.
49. [1962] (with M. Nerlove) Optimal Advertising Policy Under Dynamic Conditions. Economica N. S., 29:129-42.
50. [1962] The Economic Implications of Learning by Doing. Review of Economic Studies 29:155-73.
51. [1962] (with L. Hurwicz) Competitive Stability Under Weak Gross Substitutability: Nonlinear Price Adjustment and Adaptive Expectations. International Economic Review 3:233-55.
52. [1963] Conference Remarks. In M. Astrachan and A. S. Cahn (eds.), Proceedings of RAND'S Demand Prediction Conference, January 25-26, 1962. Santa Monica, California: The RAND Corporation, RM-3358-RP, pp. 125-34.
53. [1963] Utility and Expectation in Economic Behavior. In S. Koch (ed.), Psychology: A Study of a Science. New York: McGraw-Hill, Vol. 6, pp. 724-52.
54. [1963] The Economic Cost to Western Europe of Restricted Availability of Oil Imports: A Linear Programming Computation. Appendix D in H. Lubell, Middle East Oil Crises and Western Europe's Energy Supplies. Baltimore: John Hopkins Press, pp. 214-220.
55. [1963] Comment on Duesenberry's "The Portfolio Approach to the Demand for Money and Other Assets." Review of Economics and Statistics 45, Supplement, pp. 24-27.
56. [1963] Uncertainty and the Welfare Economics of Medical Care. American Economic Review 53:941-73.
57. [1963-4] Control in Large Organizations. Management Science 10:397-408.
58. [1964] Optimal Capital Policy, the Cost of Capital, and Myopic Decision Rules. Annals of the Institute of Statistical Mathematics 16:21-30.
59. [1964] Research in Management Control: A Critical Synthesis. In C. P. Bonini, R. K. Jaedicke, and H. M. Wagner (eds.), Management Controls: New Directions in Basic Research. New York: McGraw-Hill, Chapter 17, pp. 317-327.
60. [1965] Connaissance, Productivite et Pratique. Bulletin SEDEIS, Etude No. 909 Supplement.
61. [1965] Statistical Requirements for Greek Economic Planning. Center of Planning and Economic Research, Lecture Series No. 18. Athens, Greece.
62. [1965] Uncertainty and the Welfare Economics of Medical Care: Reply (The Implications of Transaction Costs and Adjustment Lags). American Economic Review 55:154-58.
63. [1965] Criteria for Social Investment. Water Resources Research 1:1-18.
64. [1965] The Economic Context. In S. T. Donner (ed.) The Future of Commercial Television, 1965-1975. (privately printed) pp. 116-39.
65. [1966] Discounting and Public Investment Criteria. In A. V. Kneese and S. C. Smith (eds.), Water Research. Baltimore: Johns Hopkins Press, pp. 13-32.
66. [1967] Values and Collective Decision-Making. In P. Laslett and W. G. Runciman (eds.), Philosophy, Politics and Society, Third Series. Oxford: Basil Blackwell, Chapter 10, pp. 215-232.
67. [1967] The Place of Moral Obligation in Preference Systems. In S. Hook (ed.) Human Values and Economic Policy. New York: New York University Press, Part II, 3, pp. 117-19.
68. [1967] Samuelson Collected. Journal of Political Economy 85:506-13.
69. [1968] Economic Equilibrium. In International Encyclopedia of The Social Sciences. New York: The Free Press, Vol. 4, pp. 376-386.
70. [1970] Meyer A. Girshick. In International Encyclopedia of the Social Sciences. New York: The Free Press, Vol. 6, pp. 191-93.
71. [1968] The Economics of Moral Hazard: Further Comment. American Economic Review 58:537-39.
72. [1968] (pseudonym of Archen Minsol; joint with H. B. Chenery, B. S. Minhas, and R. M. Solow) Some Tests of the International Comparisons of Factor Efficiency with the CES Production Function: A Reply. Review of Economics and Statistics 50:477-9.
73. [1968] Optimal Capital Policy with Irreversible Investment, in J. N. Wolfe (ed.), Value, Capital, and Growth, Edinburgh: Edinburgh University Press, pp. 1-20.
74. [1968] Applications of Control Theory to Economic Growth, in American Mathematical Society, Mathematics of the Decision Sciences, Providence: American Mathematical Society, Part 2, pp. 85-119.
75. [1969] Classificatory Notes on the Production and Transmission of Technological Knowledge. American Economic Review Papers and Proceedings 59:29-35.
76. [1969] The Organization of Economic Activity: Issues Pertinent to the Choice of Market Versus Nonmarket Allocation. In Joint Economic Committee, U. S. Congress, The Analysis and Evaluation of Public Expenditures: The PPB System, Vol. 1; pp. 47-66.
77. [1969] (with M. Kurz) Optimal Consumer Allocation Over an Infinite Horizon. Journal of Economic Theory 1:68-91.
78. [1969] Tullock and an Existence Theorem. Public Choice VI: 105-112.
79. [1969] (with M. Kurz), Optimal Public Investment Policy and Controllability with Fixed Private Savings Ratio. Journal of Economic Theory 1:141-77.
80. [1969] (with D. Levhari) Uniqueness of the Internal Rate of Return with Variable Life of Investment. Economic Journal 79:560-66.
81. [1969] The Social Discount Rate. In G. G. Somers and W. D. Wood (eds.) Cost-Benefit Analysis of Manpower Policies. Kingston, Ontario: Industrial Relations Centre, Queen's University.
82. [1970] The Effects of the Price System and Market on Urban Economic Development. In K. J. Arrow et al, Urban Processes As Viewed by the Social Sciences. Washington, D. C.: The Urban Institute, pp. 11-20.
83. [1970] (with M. Kurz) Optimal Growth with Irreversible Investment in a Ramsey Model. Econometrica 38:331-344.
84. [1970] New Ideas in Pure Theory: Discussion. American Economic Review Papers and Proceedings 60:462-3.
85. [1970] (with R. C. Lind) Uncertainty and the Evaluation of Public Investment Decisions. American Economic Review 60:364-78.
86. [1970] Criteria, Institutions, and Function in Urban Development Decisions. In A. H. Pascal (ed.) Thinking About Cities. Belmont, California: Dickenson.
87. [1970] Induced Technical Change and Patterns of International Trade: Comment. In R. Vernon (ed.) The Technology Factor in International Trade. New York: National Bureau of Economic Research, pp. 128-32.
88. [1971] The Firm in General Equilibrium Theory. In R. Marris and A. Wood (eds.) The Corporate Economy: Growth, Competition, and Innovative Potential. Cambridge, Massachusetts: Harvard University Press, and London: Macmillan, pp.68-110.
89. [1971] A Utilitarian Approach to the Concept of Equality in Public Expenditures. Quarterly Journal of Economics 85:409-415.
90. [1972] (with L. Hurwicz) An Optimality Criterion for Decision-Making Under Ignorance. In C.F. Carter and J. L. Ford (eds.), Uncertainty and Expectations in Economics: Essays in Honour of G. L. S. Shackle. Oxford: Basil Blackwell, pp. 1-11.
91. [1972] (with R. C. Lind) Uncertainty and the Evaluation of Public Investment Decisions: Reply. American Economic Review 62:171-2.
92. [1972] Problems of Resource Allocation in United States Medical Care. In R. M. Kurz and H. Fehr (eds.), The Challenge of Life. Basel and Stuttgart: Birkhauser, pp. 392-408.
93. [1972] Models of Job Discrimination. In A. H. Pascal (ed.) Racial Discrimination in Economic Life. Lexington, Massachusetts, Toronto and London: D. C. Heath, Chapter 2, pp. 83-102.
94. [1972] Some Mathematical Models of Race in the Labor Market. In A. H. Pascal (ed.), Racial Discrimination hi Economic Life. Lexington, Massachusetts, Toronto and London: D. C. Heath, Chapter 6, pp. 187-204.
95. [1972] Gifts and Exchanges. Philosophy and Public Affairs 1:343-62.
96. [1972] (with D. Levhari and E. Sheshinski) A Production Function for the Repairman Problem. Review of Economic Studies 39:241-9.
97. [1972] Exposition of the theory of choice under uncertainty. In C.B. McGuire and R. Radner (eds.) Decision and Organization. Minneapolis: University of Minnesota Press. Chapter 2, pp. 19-56.
98. [1972] Value of and demand for information. In C.B. McGuire and R. Radner (eds.) Decision and Organization. Minneapolis: University of Minnesota press. Chapter 6, pp. 131-140.
99. [1973] Some Ordinalist-Utilitarian Notes on Rawl's Theory of Justice. Journal of Philosophy 70:245-63.
100. [1973] (with D. Starrett) Cost- and Demand- Theoretical Approaches to the Theory of Price Determination. In J. R. Hicks and W. Weber (eds.) Carl Menger and the Austrian School of Economics. Oxford: The Clarendon Press, Chapter 7, pp. 129-148.
101. [1973] Higher Education as a Filter. Journal of Public Economics 2:193-216.
102. [1973] General Economic Equilibrium: Purpose, Analytic Techniques, Collective Choice. In Les Prix Nobel en 1972. Stockholm: The Nobel Foundation, pp. 206-231.
103. [1973] Social Responsibility and Economic Efficiency. Public Policy 21:303-318.
104. [1973] Formal Theories of Social Welfare. In P. P. Wiener (ed.) Dictionary of the History of Ideas. New York: Scribner, Volume IV, pp. 276-284.
105. [1973] Information and Economic Behavior. Stockholm (lecture): Federation of Swedish Industries.
106. [1973] The Theory of Discrimination. In O. Ashenfelter and A. Rees (eds.) Discrimination in Labor Markets. Princeton: Princeton University Press, pp. 3-33.
107. [1973] (with F. J. Gould and S. M. Howe) A General Saddle Point Result for Constrained Optimization. Mathematical Programming 5:225-234.
108. [1973] Rawls's Principle of Just Saving. Swedish Journal of Economics 75:323-335.
109. [1974] The Measurement of Real Value Added. In P. A. David and M. W. Reder (eds.) Nations and Households in Economic Growth. New York and London: Academic Press, pp. 3-19.
110. [1974] Stability Independent of Adjustment Speed. In G. Horwich and P. A. Samuelson (eds.) Trade, Stability, and Macroeconomics. New York and London: Academic Press, pp. 181-202.
111. [1974] Capitalism, for Better or Worse. In L. Silk (ed.) Capitalism: The Moving Target. New York: Quadrangle/New York Times Company, pp. 105-113.
112. [1974] Unbounded Utility Functions in Expected Utility Maximization: Response. Quarterly Journal of Economics 88:136-138.
113. [1974] Limited Knowledge and Economic Analysis. American Economic Review 64:1-10.
114. [1974] Optimal Insurance and Generalized Deductibles. Scandinavian Actuarial Journal 1974:1-42.
115. [1974] (with A. C. Fisher) Environmental Preservation, Uncertainty, and Irreversibility. Quarterly Journal of Economics 88:312-319.
116. [1974] On the Agenda of Organizations. In R. Marris (ed.) The Corporate Society. New York and Toronto: Wiley, pp. 214-234.
117. [1974] The Combination of Time Series and Cross-Section Data in Interindustry Flow Analysis. European Economic Review 5:25-32.
118. [1974] Government Decision Making and the Preciousness of Human Life. In L. R. Tancredi (ed.) Ethics of Health Care. Washington, D. C.: National Academy of Sciences, Chapter II, pp. 33-47.
119. [1975] Vertical Integration and Communication. The Bell Journal of Economics 6:173-183.
120. [1975] Thorstein Veblen as an Economic Theorist. The American Economist 19:5-9.
121. [1975] On a Theorem of Arrow: Comment. Review of Economic Studies 62:487.
122. [1975] Economic Development: The Present State of the Art. Papers of the East-West Communication Institute, No. 14.
123. [1976] Economic Dimensions of Occupational Segregation: Comment I. Signs 1, No. 3, Part 2, pp. 233-237.
124. [1976] Quantity Adjustments in Resource Allocation: A Statistical Interpretation. In R. E. Grierson (ed.) Public and Urban Economics, Lexington, Massachusetts, Toronto and London: Lexington Books, Chapter 1, pp. 3-11.
125. [1976] Theoretical Issues in Health Insurance. The University of Essex, Noel Buxton lecture for 1973.
126. [1976] Welfare Analysis of Changes in Health Coinsurance Rates. In R. N. Rossett (ed.) The Role of Health Insurance in the Health Services Sector. New York: National Bureau of Economic Research, Chapter 1, pp. 2-23.
127. [1976] Evaluation of Social Experiments: Discussion. In C. G. Abt (ed.) The Evaluation of Social Programs. Beverly Hills and London: Sage Publications, pp. 49-54.
128. [1976] The Rate of Discount for Long-Term Public Investment. In H. Ashley, R. L. Rudman, and C. Whipple (eds.) Energy and the Environment: A Risk-Benefit Approach. New York: Pergamon, pp. 113-140.
129. [1976] The Genesis of Dynamic Systems Generated by Metzler Matrices. In R. Henn and O. Moeschlin (eds.) Mathematical Economics and Game Theory: Essays in Honor of Oskar Morgenstern. Berlin, Heidelberg, and New York: Springer-Verlag, pp. 629-644.
130. [1977] Extended Sympathy and the Possibility of Social Choice. American Economic Review Papers and Proceedings 67, No. 1:219-225.
131. [1977] Current Developments in the Theory of Social Choice. Social Research 44:607-622.
132. [1978] The Future and the Present in Economic Life. Economic Inquiry 16:157-170.
133. [1978] Nozick's Entitlement Theory of Justice. Philosophia 7:265-279.
134. [1978] Risk Allocation and Information: Some Recent Theoretical Developments. The Geneva Papers on Risk and Insurance, No. 8, June 1978 (Association Internationale pour l'Etude de l'Economie de l'Assurance).
135. [1978] Jacob Marschak's Contributions to the Economics of Decision and Information. American Economic Review, Papers and Proceedings, Vol. 68, pp. xii-xiv.
136. [1978] Jacob Marschak. In International Encyclopedia of the Social Sciences. New York: The Free Press, Vol. 18, Biographical Supplement, pp. 500-507.
137. [1979] (with R. Radner) Allocation of Resources in Large Teams. Econometrica 47:361-385.
138. [1979] The Economics of Information. In M. L. Dertouzos and J. Moses (eds.) The Computer Age: A Twenty-Year View. Cambridge, Massachusetts: MIT Press, pp. 306-317.
139. [1979] (with J. P. Kalt) Petroleum Price Regulation. Washington, D.C.: American Enterprise Institute for Public Policy Research.
140. [1979] The Property Rights Doctrine and Demand Revelation under Incomplete Information. In M. Boskin (ed.) Economics and Human Welfare. New York and London: Academic Press, pp. 23-39.
141. [1979] The Trade-Off Between Growth and Equity. In H. I. Greenfield, A. M. Levenson, W. Hamovitch, and E. Rotwein (eds.) Theory for Economic Efficiency: Essays in Honor of Abba P. Lerner. Cambridge, Massachusetts: MIT Press, pp. 1-11.
142. [1980] (with S. Chang) Optimal Pricing, Use and Exploraton of Uncertain Natural Resource Stocks. In P. T. Liu (eds.) Dynamic Optimization and Mathematical Economics. New York: Plenum, pp. 105-16.
143. [1980] Microdata Simulation: Current Status, Problems, Prospects. In R. Haveman and K. Hollenback (eds.) Microeconomic Simulation Models for Public Policy Analysis. New York and London: Academic Press, Vol. 2, pp. 253-265.
144. [1980] Real and Nominal Magnitudes in Economics. Journal of Financial and Quantitative Analysis 25:773-783.
145. [1981] Futures Markets: Some Theoretical Perspectives. Journal of Futures Markets 1:107-113.
146. [1981] Optimal and Voluntary Income Distribution. In S. Rosefielde (ed.) Economic Welfare and the Economics of Soviet Socialism: Essays in Honor of Abram Bergson, Cambridge, United Kingdom: Cambridge University Press, pp. 276-88.
147. [1981] (with L. Pesotchinsky and M. Sobel) On Partitioning a Sample with Binary-Type Questions in Lieu of Collecting Observations. Journal of the American Statistical Association 76:402-9.
148. [1981] Pareto Efficiency with Costly Transfers. In J. Los (ed.) Studies in Economic Theory and Practice. Amsterdam: North-Holland Publishing Company, Chapter 6.
149. [1981] The Social Choice Perspective. Hofstra Law Review 9:1373-80.
150. [1981] The Response of Orthodox Economics. In H. E. Daly and A. F. Umana (eds.) Energy, Economics, and the Environment. Boulder, Colorado: Westview Press, pp. 109-113.
151. [1981] On Finance and Decision Making. In R. Vernon and Y. Aharoni (eds.) State-Owned Enterprise in the Western Economies. London: Croom Helm, pp. 63-69.
152. [1982] Risk Perception in Psychology and Economics. Economic Inquiry 20:1-9.
153. [1982] Income Testing and Social Welfare: An Optimal Tax-Transfer Model: Discussion. In I. Garfinkel (ed.) Income-Tested Transfer Programs: The Case for and Against. New York and London Academic: Press, pp. 319-323.
154. [1982] The Rate of Discount on Public Investments with Imperfect Capital Markets. In R. C. Lind and others, Discounting for Time and Risk in Energy Policy. Washington, D. C.: Resources for the Future, pp. 115-136.
155. [1982] Comment on Evolutionary Models in Economics and Law: Cooperative versus Conflict Strategies, by Jack Hirshleifer. In F. Zerbe (ed.) Research in Law and Economics, Volume 4: 81-87.
156. [1983] Contributions to Welfare Economics. In E. C. Brown and R. M. Solow (eds.) Paul Samuelson and Modern Economic Theory. New York: McGraw-Hill, pp. 15-30.
157. [1983] Innovation in Large and Small Firms. In J. Ronen (ed.) Entrepreneurship. Lexington, Massachusetts: Lexington Books, pp. 15-28.
158. [1983] Team Theory and Decentralized Resource Allocation: An Example. In P. Desai (ed.) Marxism, Central Planning, and the Soviet Economy. Cambridge, Massachusetts, and London: The MIT Press, Chapter 4, pp. 63-76.
159. [1983] Behavior under Uncertainty and Its Implications for Policy. In B. Stigum and F. Wentst??p (eds.) Foundations of Utility and Risk Theory with Applications. Dordrecht: D. Reidel, pp. 19-32.
160. [1984] Permanent and Transitory Substitution Effects in Health Insurance Experiments. Journal of Labor Economics, 2:259-267.
161. [1985] The Informational Structure of the Firm. American Economic Review Papers and Proceedings 75: No. 2, 303-307.
162. [1985] Maine and Texas. American Economic Review Papers and Proceedings 75: No. 2, 320-323.
163. [1985] The Economics of Agency. In J. W. Pratt and R. J. Zeckhauser (eds.) Principals and Agents: The Structure of Business. Boston: Harvard Business School Press, Chapter 2, pp. 37-51.
164. [1986] Rationality of Self and Others in an Economic System. Journal of Business 59: $385-$399.
165. [1986] Planning and Uncertainty. In I. Adelman and J. E. Taylor (eds.) The Design of Alternative Development Strategies. Rohtak, India: Jan Tinbergen Institute of Development Planning, Chapter 9.
166. [1986] Comments, in R. G. Cummings, D. S. Brookshire, and W. D. Schulze (eds.) Valuing Environmental Goods: An Assessment of the Contingent Valuation Method, Totawa. New Jersey: Rowman and Allanheld, pp. 180-185.
167. [1987] The Demand for Information and the Distribution of Income. Probability in the Engineering and Informational Sciences 1:3-13.
168. [1987] Technical Information, Returns to Scale, and the Existence of Competitive Equilibrium. In T. Groves, R. Radner, and S. Reiter (eds.) Information, Incentives, and Economic Mechanisms. Minneapolis: University of Minnesota Press, Chapter 7, pp. 243-255.
169. [1988] Ricardos Werk aus der Sicht der modernen Okonomie. In K. J. Arrow, M. Ricardo, and H. Recktenwald, David Ricardo: Eine moderne Wurdigung. Dusseldorf: Verlag Wirtschaft und Finanzen, pp. 43-59.
170. [1988] L'Informazione come Industria di Servizi. In G. Tamburini (ed.) Verso L'Economia dei Nuovi Servizi: I Settore Finanziario. Bologna: Il Mulino, Chapter 1, pp. 29-38.
171. [1988] Presidential address: General Economic Theory and the Emergence of Theories of Economic Development. Chapter 2 in K. J. Arrow (ed.) The Balance between Industry and Agriculture in Economic Development, Volume 1: Basic Issues. Basingstoke and London: Macmillan for the International Economic Association, pp. 22-32.
172. [1988] Overview of the Conference. In S. Borner (ed.) International Finance and Trade in a Polycentric World. London: Macmillan in association with the International Economic Association, pp. 392-396.
173. [1989] Joan Robinson and Modern Economic Theory: An Interview. In G. Feiwel (ed) Joan Robinson and Modern Economic Theory. New York: New York University Press, Chapter 3, pp. 147-185.
174. [1989] Von Neumann and the Existence Theorem for General Equilibrium. In M. Dore, S. Chakravarty, and R. Goodwin (eds.) John yon Neumann and Modern Economics. Oxford: Clarendon Press, Chapter 2, pp. 15-28.
175. [1989] A "Dynamic" Proof of the Frobenius-Perron Theorem for Metzler Matrices. In T. W. Anderson, K. B. Atheyra, and D. L. Iglehart (eds.) Probability, Statistics, and Mathematics: Papers in Honor of Samuel Karlin. Boston: Academic Press, pp. 17-26.
176. [1991] Certainty Equivalence and Inequivalence for Prices. In L. W. McKenzie and S. Zamagni (eds.) Value and Capital: Fifty Years Later. Basingstoke, U.K.: Macmillan for the International Economic Association, pp. 41-63.
177. [1991] Cowles in the History of Economic Thought. In Cowles Fiftieth Anniversary. New Haven: Cowles Foundation for Research in Economics, pp. 1-24.
178. [1991] The Dynamics of Technological Change. In Organization for Economic Co-operation and Development, Technology and Productivity: The Challenge for Economic Policy. Paris: OECD, pp. 473-6.
179. [1991] Panel Contribution: The Transition from Communism to an Alternative Economic Organisation. In A. B. Atkinson and R. Brunetta (eds.) Economics for the New Europe. Basingstoke and London: Macmillan, in association with the International Economic Association, pp. 377-382.
180. [1991] Scale Returns in Communication and Elite Control of Organizations. Journal of Law, Economics, and Organization 7, Special Issue, 1-6.
181. [1992] Informational Equivalence of Signals. In P. Dasgupta, D. Gale, O. Hart, and E. Maskin (eds.) Economic Analysis of Markets and Games. Cambridge, Massachusetts, and London: The MIT Press. Pp. 169-183.
182. [1992] Transition from Socialism. Estudios Economicos 6: No. 1,5-22.
183. [1992] Sex Differentiation in Annuities: Reflections on Utilitarianism and Inequality. In R. Selten (ed.) Rational Interaction. Berlin: Springer-Verlag. Pp. 333-336.
184. [1992] The Basic Economics of Arms Reduction. In W. Isard and C. H. Anderton (eds.)Economics of Arms Reduction and the Peace Process. Amsterdam: Elsevier. Chapter 2. Pp. 57-61.
185. [1992] Excellence and Equity in Higher Education, Education Economics 1: 5-12.
186. [1993] Economic Integration and the Future of the Nation-State. Contemporary Policy Issues XI: 1-6.
187. [1993] Contingent Valuation of Nonuse Values: Observations and Questions. In J. Hausman (ed.) Contingent Valuation: A Critical Assessment. Amsterdam: North-Holland, Chapter XIV, pp. 479-484.
188. [1993] Does A Good Place Value News? In A. B. Atkinson (ed.) Alternatives to Capitalism: The Economics of Partnership. New York, St. Martin's Press, Chapter 3, pp. 33-44.
189. [1993] (with J. Edward Li) A Note on the Peace Dividend and Reallocation of Knowledge Skills. In J. Brauer and M. Chatterji (eds.) Economic Issues of Disarmament. Basingstoke and London: Macmillan, Chapter 3, pp. 26-32.
190. [1994] Methodological individualism and social knowledge. American Economic Review Papers and Proceedings 84: no. 2, 1-9.
191. [1994] General Economic Theory and Income Distribution. In J.H. Bergstand, T.F. Cosimano, J.W. Houck, and R.G. Sheehan (eds.) The Changing Distribution of Income in an Open U.S. Economy. Amsterdam, London, New York, and Tokyo: North Holland, 1994, Chapter 12, pp. 343-347.
192. [1994] The production and distribution of knowledge. In G. Silverberg and L. Soete (eds.), The Economics of Growth and Technical Change: Technologies, Nations, Agents. Aldershot, U.K., and Brookfield, Vt.: Edward Elgar. Chapter 2, pp. 9-20.
193. [1994] (with Timothy Kehoe) Distinguished Fellow: Herbert Scarf's contributions to economics. Journal of Economic Perspectives 8:161-181.
194. [1994] International peace-keeping forces: economics and politics. In M. Chatterji, H. Jager and A. Rima (eds.) The Economics of International Security. Basingstoke: Macmillan, and New York: St. Martin's. Pp 81-86.
195. [1994] Information and the organization of industry. Rivista internazionale di scienze sociali 52; 111-124.
196. [1995] Foreword to, M. McFaul and T. Perlmutter (eds.) Privatization, conversion, Enterprise Reform in Russia. Boulder, San Francisco, and Oxford: Westview Press.
197. [1995] A note on freedom and flexibility. In K. Basu, P. Pattanaik, and K. Suzumura (eds), Choice, Welfare, and Development. Oxford: Clarendon Press. pp. 7-16.
198. [1995] Some general observations on the economics of peace and war. Peace Economics, Peace Science, and Public Policy 2 (Winter): 1-8.
199. [1995] Information acquisition and the resolution of conflict, K.J. Arrow, R.H. Mnookin, L. Ross, A. Tversky, and R. Wilson (eds) Barriers to Conflict Resolution. New York and London: Norton.
200. [1995] Economics as it is and as it is developing: a very rapid survey. In H. Albach and S. Rosenkranz (eds.) Intellectual Property Rights and Global Competition: Towards a New Systhesis. Berlin: Edition Sigma. Pp. 11-32.
201. [1995] The use of genetic and other medical information: ethical and market dilemmas. George Seltzer Distinguished Lecture, Industrial Relations Center, University of Minnesota.
202. [1995] Effet de serre et actualisation. Revue de L'Energie No. 471 (Octobre): 631-636.
203. [1995] (With D.W. Carlton and H.S. Sider) The competitive effects of line-of-business restrictions in telecommunications. Managerial and Decision Economics 16:301-321.
204. [1996] Information, responsibility, and human services. In V.R. Fuchs (ed.), Individual and Social Responsibility: Child Care, Education, Medical Care and Long-Term Care in America. Chicago and London: The University of Chicago Press. Chapter 8, pp. 229-239.
205. [1996] Inequalities in income and wealth. In E. Malinvaud and M. Archer (eds.) The Study of the Tensions Between Human Equality and Social Inequalities from the Perspective of the Various Social Sciences. Vatican City: Pontifical Academy of Social Sciences. Pp. 115-124.
206. [1996] Comment on M. Kurz, "Rational preferences and rational beliefs." In K.J. Arrow, E. Colombatto, M. Perlman, and C. Schmidt (eds.) The Rational Foundations of Economic Behavior. New York: St. Martin's Press, and Basingstoke and London: Macmillan, in association with the International Economic Association. Pp 363-363.
207. [1996] The impact of operations research and decision theory on teaching and research in economics. In K.J. Arrow, R.W. Cottle, B.C. Eaves, and I. Olkin (eds.) Education in a Research University. Stanford, CA: Stanford University Press, P; 353-369.
208. [1996] The theory of risk-bearing: small and great risks. Journal of Risk and Uncertainty 12:101-111.7.
209. [1996] (with J. Parikh and G. Pillet as Principal Lead Authors) Decision-making frameworks for addressing climate change. In J.P. Bruce, H. Lee, and E.F. Haites (eds) Climate Change 1995: Economic and Social Dimensions of Climate Change, Contribution of Working Group III to the Second Assessment of Intergovernmental Panel on Climate Change. Cambridge University Press: Cambridge, UK, New York, and Melbourne. Pp 53-78.
210. [1996] (with W.R. Cline, K-G. Maler, M. Munasinghe, R. Squitieri, and J.E. Stiglitz as Principal Lead Authors) Intertemporal equity, discounting and econonmic efficiency. In J.P. Bruce, H. Lee, and E.F. Haites (eds) Climate Change 1995: Economic and Social Dimensions of Climate Change, Contribution of Working Group III to the Second Assessment of Intergovernmental Panel on Climate Change. Cambridge University Press: Cambridge, UK, New York, and Melbourne. Pp. 125-144.
211. [1996] The economics of information: a survey. Empirica 23:119-128.
212. [1996] Elements of the economics of information; information and increasing returns. Chung-hua Series of Lectures by Invited Eminent Economists, No. 22: Nanking, Taipei, ROC: Institute of Economics, Academia Sinica.
213. [1996] Technical information and industrial structure, Industrial and Corporate Change 5: 645-652.
214. [1997] Economic growth for a small country. In A.W. Gray (ed.) International Perspectives on the Irish Economy. Dublin: Indecon Economic Consultants. Chapter 1, pp. 1-8.
215. [1997] The benefits of education and the formation of preferences. In J.R. Behrman and N. Stacey (eds.) The Social Benefits of Education. Ann Arbor: University of Michigan Press. Chapter 2, pp. 11-16.
216. [1997] Invaluable goods. Journal of Economic Literature 35: 757-765.
217. [1997] The functions of social choice theory. In K.J. Arrow, A.K. Sen, and K. Suzumura, (eds.) Social Choice Re-examined. Basingstoke and London: Macmillan in association with the International Economic Association. Vol. 1, pp. 3-9.
218. [1997] Kapitaltheorie als Erweiterung der Werttheorie. In K.J. Arrow, C. Bliss, and S. Zamagni, John R. Hicks und sein "Value and Capital." Dusseldorf: Verlag Wirtschaft und Finanzen. Pp. 31-46.
219. [1998] Innovation and increasing returns to scale. In K.J. Arrow, Y-K Ng, and X. Yang, Increasing Returns and Economic Progress, Basingstoke, UK: Macmillan, and New York: St. Martin's. Chapter 18, pp. 403-408.
220. [1998] "What has economics to say about racial discrimination?" Journal of Economic Perspectives 12: 91-100.
221. [1998] The external costs of voting rules: a note on Guttman, Buchanan, and Tullock. European Journal of Political Economy 14: 219-222.
222. [1998] The place of institutions in the economy: a theoretical perspective. In Y. Hayami and M. Aoki (eds.) The Institutional Foundations of East Asian Economic Development. Basingstoke and London: Macmillan, and New York: St Martin's Press in association with the International Economic Association. Chapter 2, pp. 39-48.
223. [1999] Discounting, morality, and gaming. In P.R. Portney and J.P. Wyant (eds.) Discounting and Intergenerational Equity. Washington: Resources for the Future. Chapter 2, pp. 13-21.
224. [1999] (with F.H. Hahn) Notes on sequence economies, transaction costs, and uncertainty. Journal of Economic Theory 86:203-218.
225. [1999] Amartya K. Sen's contributions to the study of social welfare. Scandinavian Journal of Economics 101: 163-172.
226. [1999] Team theory and distributed processing: surprise attack. Information Systems Frontiers 1:11-13.
227. [1999] The economics of information. Studi Economici. 54 (1): 5-14.
228. [1999] Comments on the commentaries. In J.E. Alt, M. Levi, and E. Ostrom (eds.), Competition and Cooperation: Conversations with Nobelists about Economics and Political Science. New York: Russell Sage, pp. 51-65.
229. [1999] Reflections on political science. In J.E. Alt, M. Levi, and E. Ostrom (eds.), Competition and Cooperation: Conversations with Nobelists about Economics and Political Science. New York: Russell Sage, pp. 321-325.
230. [1999] Inter-generational equity and the rate of discount in long-term social investment. In M. Sertel (ed.) Contemporary Economic Issues. Volume 4: Economic Behavior and Design, Basingstoke and New York: Macmillan and St. Martin's Press in association with the International Economic Association. Chapter 5, pp. 89-102.
231. [2000] Economic transition: speed and scope. Journal of Institutional and Theoretical Economics 156:10-18.
232. [2000] A comment on Cooper. World Bank Research Observer 15: 173-75.
233. [2000] Knowledge as a factor of production. In Annual World Bank Conference on Development Economics 1999. Washington, DC: International Bank for Reconstruction and Development. Pp. 15-20.
234. [2001] Die Debatte uber Skalerntrage in "Economic Journal." In K.J. Arrow, S. Blankenburg, G.C. Harcourt, B. Schefold, and P. Sylos Labini, Vademecum zu der Klassischen Debatte uber Kosten, Wettbewerb und Entwicklung, Dusseldorf: Verlag Wirtschaft und Finanzen, pp. 47-56.
235. [2001] In memoriam: John C. Harsanyi. Games and Economic Behavior 36: 5-6.
236. [2001] The five most significant developments in economics of the twentieth century. European Journal of the History of Economic Thought 8: 298-304.
237. [2001] Reflections on the reflections. Journal of Health Politics, Policy, and Law 26:1197-2003.
238. [2001] Entry, productivity, and investment. Review of Economic Design 6: 175-184.
239. [2001] Comment on "Developing Countries and the New Financial Architecture." In E. Malinvaud and L. Sabourin (eds) Globalization: Ethical and Institutional Concerns. Pontifical Academy of Social Sciences: Vatican City. Pp. 306-310
Attachment B
PRIVILEGED AND CONFIDENTIAL
In re: United States v. Microsoft Corp., Civ. Action No. 98-1232; New York v. Microsoft Corp., Civ. Action No. 98-1233
Mediator's Draft No. 18 of Settlement Stipulation and Proposed Consent Decree
Stipulation
The parties, by their respective attorneys, agree as follows:
1. The court has jurisdiction over the subject matter of this action and over all the parties to it.
2. The final judgment attached hereto (sometimes referred to as the "decree") may be entered by the court upon motion of any party or upon the court's own motion at any time after compliance with the requirements of the Antitrust Procedures and Penalties Act, 15 U.S.C. § 16.
3. The parties shall comply with the terms of the attached final judgment no later than 30 days after the date of the execution of this stipulation, with the exception of §§ 3.9 and 4.1, with respect to which compliance shall be due no later than 60 days after the date of the execution of this stipulation, and § 4.2, which specifies the time for compliance with that section.
4. The plaintiffs agree not to oppose a motion by Microsoft to vacate the findings of fact that the court issued on November 5, 1999, and to declare that those findings, and the judgment when entered, shall have no preclusive effect, either under principles of collateral estoppel (issue preclusion) or section 5(a) of the Clayton Act, 15 U.S.C. § 16(a), in any proceeding, the court having rendered no conclusions of law or determination of liability and Microsoft Corporation having not acknowledged liability and having represented that it has agreed to the entry of this judgment solely for business reasons, to avoid the expense and uncertainties of continued litigation. Microsoft's consent to the entry of this judgment is conditional upon the grant of this motion.
5. If the court does not enter the decree as the final judgment in this proceeding, all the parties are relieved from all obligations under the decree and this stipulation.
6. This stipulation will not be effective until all the parties to the litigation have signified in writing that they agree to it. It will become effective on the day on which the last party communicates its acceptance to the other parties.
7. This stipulation and the attached decree are the complete and integrated expression of the parties' settlement agreement.
4/5/00
Final Judgment
It is ordered, adjudged, and decreed, as follows:
§ 1. Jurisdiction:
This court has jurisdiction of the subject matter of this action and of Microsoft. Microsoft has violated sections 1 and 2 of the Sherman Act, 15 U.S.C. §§ 1, 2, and related state laws of the States of New York, California, Connecticut, Florida, Illinois, Iowa, Kansas, Kentucky, Louisiana, Maryland, Massachusetts, Michigan, Minnesota, New Mexico, North Carolina, Ohio, Utah, West Virginia, and Wisconsin, and the District of Columbia.
§ 2. Definitions:
(1) "operating system": the software that controls the operation of a computer. An "operating system product" is any operating system or part or feature thereof that is distributed commercially whether or not it is marketed for a positive price. A "personal computer operating system" is an operating system intended to be used with personal computers, whether or not such operating system is also intended to be used with other computers.
(2) "Windows operating system." Software code (including source code and binary) of Windows 98, Windows 2000 Professional, and their successors, including the Windows operating systems codenamed "Millennium," "Whistler," and "Blackcomb."
(3) "middleware": software that operates between two or more types of software (such as an application, an operating system, a server operating system, or a database management system) and could, if ported to multiple operating systems, enable software products written for that middleware to be run on multiple operating systems. Software does not cease to be middleware, if otherwise within the definition in this subsection, merely because it interacts directly with the operating system or other software. Examples of middleware within the meaning of the decree include Internet Explorer, the Outlook Express e-marl client, Windows Media Player, and the Java Virtual Machine. Examples of software that are not middleware within the meaning of the decree are disk compression and memory management.
(4) "platform software": either an operation system or middleware, as these terms are defined above.
(5) "default Middleware": software configured to launch automatically (that is, by "default") to provide particular functionality-when-other middleware has not been selected for this purpose. For example; a default browser is middleware configured to launch automatically to display Web pages transmitted over the Interact or an intranet that hear the .htm extension, when other software has not been selected for this purpose.
(6) "personal computer": a computer that is designed to he used by one person at a time that uses a video display and keyboard (whether or not the video display and keyboard are actually included), and that contains an Intel x86 or competitive microprocessor, and computers that are commercial substitutes for such computers.
(7) "original equipment manufacturer (OEM)": the manufacturer or assembler of a personal computer.
(8) "independent software vendor (ISV)": any entity other than Microsoft (or any subsidiary, division, or other operating unit of any such other entity) that is engaged in the development and licensing (or other marketing) of software products intended to intemperate with Microsoft platform software.
(9) "application programming interfaces (APIs)": the interfaces and protocols that enable an application, middleware, or server operating system to efficiently and effectively obtain services from (or provide services in response to requests from) platform software in a personal computer and to use, benefit from, and rely on the resources, facilities, and capabilities of such platform software.
(10) "communications interfaces": the interfaces and protocols that enable applications, middleware, or operating systems installed on other computers (including servers) to interoperate satisfactorily with the Windows platform software on a personal computer.
(11) "technical information": all information, regarding the identification and means of using APIs (or communications interfaces), that competent software developers require to make their products running on a personal computer, server, or other device interoperate satisfactorily with Windows platform software running on a personal computer. Technical information includes reference implementations, communications protocols, file formats, data formats, data structure definitions and layouts, error codes, memory allocation and deallocation conversions, threading and synchronization conventions, algorithms for data translation or reformatting (including compression/decompression algorithms and encryption/decryption algorithms), registry settings, and field contents.
(12)
(13) "end-user access": the invocation of middleware by an end user of a personal computer or the ability of such an end-user to invoke middleware. "End-user access" includes invocation of middleware by end-users which is compelled by the design of the operating system.
(14) "Market Development Agreement (MDA)": the class of agreements with OEMs that provides discounts from Windows operating system royalties.
§3. Prohibitions:
Microsoft Corporation is enjoined from:(1) agreeing or offering to provide any consideration or advantage to any person in exchange for, or conditioned on, such person's agreement or willingness not to develop, promote or distribute (or to limit the development, promotion or distribution) of any operating system product or middleware competitive with any Windows operating system product or middleware.
(2) offering or conditioning a Windows operating system license to any OEM, or the terms of administration of a license, or any change in Microsoft's commercial relations with an OEM, or offering or threatening to do any of these things, related to whether (or to the extent) the OEM
(3) limiting an OEM's
(4) conditioning the licensing of a Windows operating system, or the terms or administration of any such license (including the nature and extent of support provided), on the OEM's
(5) Entering into any agreement with an OEM in which the operating system royalties are payable to Microsoft by the OEM are set otherwise than by reference to a uniform royalty schedule to be established by Microsoft: in its sole discretion, except that the schedule may specify different royalties for different language versions
(6) agreeing or offering
(7) conditioning any bona fide ISV's access to technical information, or developer support to assist in its use, to assist in the creation of Windows-based applications (or the terms on which such Information or support is provided), upon such ISV's
(8) failing to disclose (at the time such APIs, technical information, or communications interfaces are disclosed to Microsoft's own software developers) for use in interoperating with Windows operating systems and middleware distributed with such operating systems, the APIs, technical information and communications interfaces that Microsoft employs to enable
(9) tying or combining any middleware product to or with a Windows operating system unless Microsoft offers a version of that operating system without such middleware product at a reduced price that reasonably reflects the relative costs of the operating system and the excluded middleware
(10) limiting an OEM's right or ability to add non-Microsoft middleware to a Windows operating system
§ 4. Affirmative Provisions:
(1) Microsoft shall license the source code for Windows operating systems on the following terms:
(2) Microsoft shall, when it makes a major Windows operating system release (such as Windows95,Windows 98, Windows 2000 Professional, Windows "Millennium," "Whistler," "Blackcomb," and successors to these), continue to license the previous Windows operating system at the existing royalty rate for three years to any OEM that desires such a license. During that period, Microsoft shall make the previous Windows operating system's code available to its 50 highest-volume OEM customers at customary and reasonable terms, together with reasonable personnel support (for which Microsoft may require compensation from the OEM at customary rates), for the purpose of enabling those OEMs to adapt the operating system to the latest hardware advances and to fix bugs. The OEM shall be free to market computers in which it preinstalls such an operating system in the same manner in which it markets computers preinstalled with other Windows operating systems, provided, however, that Microsoft shall be entitled to require OEMs to inform their customers that such computers contain a modified version of a Windows operating system.
(3) In all future MDAs, Microsoft shall offer the same MDA terms to all OEMs whose shipments of Microsoft operating systems fall within a specified range (e.g., the 10 largest OEMs, as measured by total annual volume of modified and unmodified versions of Microsoft operating systems that they ship, would be entitled to the highest MDA, the next 10 to a lower MDA, and the remaining OEMs to no MDA), subject to variations by geography for OEMs that make more than S0 percent of their sales outside the United States. No class entitled to the same MDA terms in accordance with this subsection shall have fewer than 10 members.
(4) Notwithstanding the foregoing provisions, upon the release of its next Windows operating system, codenamed "Millennium," and upon the next release, version, or service pack update of Windows 2000 Professional after May 30, 2000, Microsoft shall provide the means for OEMs and end users at their option readily to prevent end-user access to the operating system's browsing functionality.
§ 5. Term:
(1) Microsoft shall comply with the provisions of this decree within 30 days after its submission to the district court for approval.
(2) This decree shall expire at the end of five years from the date of that submission, except that:
§ 6. Enforcement:
In order to minimize the burden on the judicial system of enforcing this decree, the plaintiffs have agreed that exclusive responsibility for enforcing it shall be lodged with the United Department of Justice and with one of the-States that are plaintiffs in this action, as selected by the plaintiff States.
§ 7. Reporting and Compliance:
(1) To determine or secure compliance with this decree, duly authorized representatives of the plaintiffs shall, upon reasonable notice given to Microsoft at its principal office, subject to any lawful privilege, be permitted:
(2) No information or documents obtained by the means provided by this decree shall be divulged by any of the plaintiffs except in the course of legal proceedings to which one or more of the plaintiffs is a party, or for the purpose of securing compliance with this decree, or as otherwise required by law. If when information or documents are furnished by it Microsoft identified in writing material to which a claim of protection may be asserted under Rule 26(c)(7) of the Federal Rules of Civil Procedure and marks each page of such material "Subject to claim of protection under Rule 26(c)(7) of the Federal Rules of Civil Procedure," ten days' notice shall be given to Microsoft prior to divulging such material in any legal proceeding (other than a grand jury proceeding) to which Microsoft is not a party.
(3) Within thirty days of the date of submission of this decree for approval by the court, Microsoft shall designate an officer of the corporation to be the antitrust compliance officer. That officer shall have primary responsibility within the corporation for achieving and maintaining full compliance with this decree and shall serve as liaison with the plaintiffs with respect to the administration of the decree. The officer may be assisted by other employees of Microsoft and will report directly to Microsoft's chief executive officer.
§ 8. Miscellaneous Provisions:
(1) This decree applies not only to Microsoft but also to each of its officers, directors, agents, employees, successors, and assigns, and to all persons in active concert or participation with any of them who shall have received actual notice of this decree by personal service or otherwise.
(2) The district court shall retain jurisdiction to enforce the decree.
(3) The decree is in the public interest.
-
-
-
- The Proposed Settlement Ignores the Likely Tactics Microsoft Will Use to Eliminate the Next Significant Threat to its Monopoly Position
-
- The Decree Increases Microsoft's Market Dominance and Actually, Worsens Competitive Conditions in the Relevant Software Markets
-
- The Settlement Would Not Have Prevented Microsoft's Unlawful Campaign Against Netscape and Java
-
-
-
-
- The Complexity and Substantial National Importance of this Case, the Government's Flat Reversal of Position and its Disregard of Clear Tunney Act Obligations All Dictate the Necessity of Critical Judicial Oversight in this Landmark Proceeding
-
-
- This Complex, Controversial, Nationally Important Antitrust Prosecution Demands Serious Judicial Oversight
-
-
- Heightened Scrutiny is Needed Because Neither the Department Nor Microsoft Complied With their Respective Tunney Act Obligations
[n]o materials and documents of the type described in the [Tunney Act] were considered in formulating the Proposed Final Judgment. Consequently, none are being filed with this Competitive Impact Statement.
-
-
- The Court Should Closely Examine the Government's Reversal of Position on Relief
-
- Live Evidence is Needed on the Technical and Economic Complexities of the Software Industry and the Profound Failings of, and Harms Caused by, the PFJ
-
-
-
- INTRODUCTION
-
-
- MICROSOFT'S MONOPOLY POWER AND THE
THREAT POSED BY NETSCAPE, JAVA AND THE INTERNET
- NETWORK EXTERNALITIES
A software product with a large installed base has several advantages relative to a new entrant. Consumers know that such a product is likely to be supported by the vendor with upgrades and service. Users of a product with a large installed base are more likely to find that their products are compatible with other products. They are more likely to he able successfully to exchange work products with their peers, because a large installed base makes it more likely that their peers will use the same product or compatible products. Installed base is particularly important to the economic success of an operating system software product. The value of the operating system is in its capability to run application software. The larger the installed base of a particular operating system, the more likely it is that independent software vendors will write programs that run on that operating system, and, in this circular fashion, the more valuable the operating system will be to consumers.
- THE MIDDLEWARE THREAT: NETSCAPE AND JAVA
A new competitor "born" on the Internet is Netscape. Their browser is dominant, with 70% usage share., allowing them to determine which network extensions will catch on. They are pursuing a multi-platform strategy where they move the key API into the client to commoditize the underlying operating system. ... One scary possibility being discussed by Internet fans is whether they should get together and create something far less expensive than a PC which is powerful enough for Web browsing.
We need to move all of our Internet value added from the Plus pack into Windows 95 as soon as we possibly can with a major goal to get OEMs shipping our browser preinstalled. This follows directly from the plan to integrate the MSN and Interact clients. Another place for integration is to eliminate today's Help and replace it with the format our browser accepts including exploiting our unique extensions so there is another reason to use our browser.
-
-
- MICROSOFT DEFEATED THE THREAT POSED BY NETSCAPE AND JAVA
- MICROSOFT'S ILLEGAL PRACTICES
- By barring original equipment manufacturers ("OEMs") from removing access to Microsoft's Internet Explorer ("IE") browser from the Windows desktop, Microsoft prevented many OEMs from installing Navigator or other browsers, and that in turn protected Microsoft's OS monopoly by reducing potential middleware competition. This violated Sec. 2 of the Sherman Act.
- By preventing OEMs from altering the initial boot sequence for Windows, Microsoft prevented OEMs from promoting Internet access providers, many of whom were using and distributing Navigator to their customers. Again, this reduced competition with IE and protected Microsoft's OS market power in violation of Sec. 2.
- Through commingling software code for Windows with that of Internet Explorer, Microsoft deterred OEMs from installing Navigator. That, in turn, reduced Navigator's usage share, and thereby protected the applications barrier to entry by reducing developer's interest in the APIs exposed by Navigator. Microsoft also removed Internet Explorer from its Add/Remove utility, further entrenching Internet Explorer and further discouraging OEMs from distributing Navigator. The D.C. Circuit found these actions to be anticompetitive and to support a finding of liability for exclusionary conduct and therefore monopolization under Section 2.
- By entering into contracts with Internet access providers that foreclosed Navigator's access to an economically significant share of the Internet access provider ("IAP") market, Microsoft engaged in exclusionary conduct in protection of its OS monopoly, again in violation of See. 2
- By entering into contracts with independent software vendors that required those independent software vendors ("ISVs") to use Internet Explorer if the ISV need web display, Microsoft further foreclosed distribution of Navigator, again in protection of its OS monopoly, in violation of Sec. 2.
- By entering into an exclusive distribution contract with Apple for Internet Explorer after Microsoft had threatened to cancel the Macintosh version of Office, Microsoft engaged in exclusionary conduct in protection of its OS monopoly in violation of Sec. 2.
- Through a number of exclusionary actions directed at Java, Microsoft limited Java's viability as a cross-platform threat and did so in violation of Sec. 2. Those actions included: limiting distribution of "write once, run anywhere" JVMs directly through exclusionary contracts with ISVs and indirectly through Microsoft's actions against Netscape; deceiving developers who wanted to develop pure Java code into writing code with Windows-specific extensions that would make the code Windows dependent; and threatening Intel and inducing it to stop developing Intel multimedia software for Java.
- THE STATE OF THE MARKET TODAY
- MICROSOFT'S MIDDLEWARE ADVANTAGES
-
-
- THE RESTRICTIONS ON MICROSOFT'S BEHAVIOR
CONTAINED IN PFJ ARE INSUFFICIENT TO RESTORE THE
COMPETITIVE THREAT THAT MIDDLEWARE POSED IN 1995
- PROBLEMS WITH THE MIDDLEWARE REMEDIES
-
- The Reliance in the PFJ on OEMs to Distribute Competing Middleware
Despite the importance of natural advantages [referring to the installed base discussion above] in the market for IBM-compatible PCs, the complaint and proposed remedies addressed competitive issues that are critical to the success of new competition in this market. The most effective and economic point of entry for sales of IBM-compatible PC operating systems is the OEM distribution channel. New operating system software products should have unimpeded access to this channel. The Government's complaint and proposed settlement provide needed relief to facilitate the entry of new competitors, such as IBM's OS/2.
-
- IE Open Source and Java Must-Carry
- INATTENTION TO THE APPLICATIONS BARRIER TO ENTRY
- C. PROBLEMS WITH THE ENFORCEMENT MECHANISM
-
-
- APPROPRIATE REMEDIES SHOULD NOT ALLOW MICROSOFT TO
PROTECT ITS ILLEGALLY MAINTAINED MONOPOLY AGAINST
CURRENT AND FUTURE COMPETITION FROM OTHER MARKETS
- FUTURE COMPETITION IN SERVERS AND WEB SERVICES
About three years ago we changed the vision of our company. Instead of talking about a computer on every desk and in every home we started talking about empowering people through software anytime, any place, any device. ... It starts with a view, which came to us quite clearly about five, almost six years ago now that XML [eXtensible Markup Language] would really be the transforming industry phenomenon of the next five years. If it was the PC 20 years ago and graphical user interface 10 or 15 years ago and the Internet five or six years ago, it's XML. And I'm not going to give a long description, but I think the way you should think about it is XML will be the Lingua Franca of computing. It will be the basis on which systems work better with systems, people with people, businesses with businesses, businesses with consumers. It will improve the level of integration and connectivity. It gives us a framework at least for the software community to build the software that allows that. ... .NET is our platform to let people take advantage of the XML revolution.
I think you could say we are a company that invests in seven businesses around one platform. That platform is .NET. .NET is our platform for the next technology revolution that is going on. And that is the shift to the XML web service model as the fundamental way of building and deploying software. .NET is our platform to do that. ... That's how we think about the seven business areas in which we are investing. They're all being re-platformed or re-plumbed around .NET and XML web services.
- MICROSOFT IS ATTEMPTING TO PROTECT ITS EXISTING MARKET POWER BY USING ITS ILLEGALLY MAINTAINED MONOPOLY IN PC OPERATING SYSTEMS TO GAIN ADVANTAGES IN SERVERS AND WEB SERVICES
- THE PFJ GIVES INSUFFICIENT ATTENTION TO:FUTURE COMPETITION
-
-
- SUMMARY OF CONCLUSIONS
(a) "intellectual property rights": copyrights, patents, trademarks, and trade secrets;
(b) "to infringe intellectual property rights": to commit a legal violation of such a right.
(a) makes or promotes (or declines to make promote, distribute, or license) a non-Microsoft operating system product or middleware;
(b) makes, promotes, distributes, or licenses a modified version of the Windows operating system; or
(c) exercises any of the options provided under this decree;
(a) interrupting the Windows initial boot sequence by a registration sequence used to obtain subscription or other information from the user;,
(b) displaying icons of a competing platform software product on the Windows desktop, or the size, shape, or convenience of such icons;
(c) displaying a middleware user interface, provided that an icon is also displayed that allows the user to access the Windows desktop and that the OEM makes clear that the interface is not Microsoft's; or
(d) offering its own sign-up sequence, which may include an option to make a non-Microsoft middleware product (for example, non-Microsoft Web-browsing functionality) the default middleware product and to remove the icon for Microsoft's middleware product from the Windows desktop;
(a) also licensing, shipping, or promoting (or declining to license, ship, promote; or limiting its licensing, shipment, or promotion of)(i) a Microsoft middleware product (ii) any other Microsoft software product that Microsoft distributes, in whole or in part, separately from the Windows -operating system(whether or not for a separate or positive price) (iii) the unmodified version of such an operating system if the OEM offers a modified version of the Windows operating system pursuant to this decree, or
(b) making middleware supplied by Microsoft the default middleware in computers sold or distributed by the OEM;
(c) whether the OEM limits end-user access to the middleware that is distributed with the operating system,
(a) to provide any consideration or advantage to any person in exchange for, or conditioned on such person's agreement or willingness to degrade or limit the quality of any non-Microsoft platform software, or not to may the supplier of any non-Microsoft platform software, or
(b) to include or promote any product of any person on the Windows desktop, in a folder on the Windows desktop, in the Active Desktop, or in the Windows initial boot sequence, related to the distribution, use, or promotion of Microsoft platform software, or to the limitation of the distribution, use, or promotion of non-Microsoft platform software;
(a) use, distribution, promotion, or support of any Microsoft middleware
(b) declining to use, distribute, promote, or support any non-Microsoft middleware
(a) Windows platform software to interoperate with Microsoft applications installed on the same personal computer, or
(b) Windows operating system software and middleware distributed with such operating system to interoperate with Microsoft middleware installed on the same personal computer if the middleware is (i) Internet Explorer, the Outlook Express e-mail client, Windows Media Player, or the Java Virtual Machine, or their successors, or (ii) distributed separately from the operating system for installation on any Windows operating system; or
(c) a Windows operating system and middleware distributed with such operating system installed on one personal computer to interoperate with any of the following software installed on a different personal computer or on a server-- (i) Microsoft applications, (ii) Microsoft middleware, or (iii) Microsoft client or server operating systems,
(a) Microsoft-shall grant each of its 50 highest-volume OEM customers, at the OEM's option, a perpetual, nonexclusive license to the source code of Windows operating systems for the sole purpose of using that source code to modify those operating systems for purposes of (i) preventing end-user access to any middleware included in the operating system, (ii) facilitating, improving, or otherwise optimizing the interoperation of any non-Microsoft middleware with, and fixing the bugs in, the operating system, and (iii) installing any end-user interface; provided that OEMs shall have no right to make modifications to a Windows operating system that render inoperable any of the APIs exposed to ISVs by that operating system unless doing so is reasonably necessary to accomplishing purposes (i), (ii), or (iii) above and the end-user to whom such operating system is licensed is given the means readily to install all software necessary to endure that such APIs are rendered operable. The source code licenses granted by Microsoft under this subsection shall not entitle OEMs to use such source code for any purpose other than creating modified versions of Windows operating systems for the purposes stated in this section and working with ISVs to facilitate the interoperation of such ISV's products with Windows operating systems.
(b) The terms of source code licenses granted by Microsoft under this subsection shall be standardized and not be subject to negotiation with individual OEMs. Microsoft shall not charge OEMs a royalty or fee for access to the source code of Windows operating systems.
(c) Microsoft's royalty for any modified version of a Windows operating system installed on an end-user's personal computer shall be calculated as follows: (i) if the royalty charged that OEM for the unmodified version is no higher than the royalty charged for the predecessor operating system, the royalty charged the OEM for the modified version shall not exceed the royalty charged that OEM for the predecessor operating system; (ii) if the royalty charged that OEM for the unmodified version exceeds the royalty charged that OEM for the predecessor system, the royalty charged that OEM for the modified version shall be the royalty charged that OEM for the unmodified version discounted by the percentage difference that is allocable in accordance with accepted accounting principles to the middleware that is (i) excluded or (ii) made not end-user accessible by the OEM. The allocation shall be based on the development costs of the unmodified version of the operating system, as determined by the agreement of the parties or, in the absence of the agreement, by an arbitrator selected in accordance with the rules of the American Arbitration Association.
(d) OEMs shall have the right to license any modified version of a Windows operating system that they create pursuant to this § 4(1) to end-users, and to value-added resellers, systems integrators, retailers, ISVs, and other OEMs for licensing to end-users, for installation and use on personal computers, provided only that such non-end-user licensees agree, either in a sublicense With-the OEM or in a license with Microsoft, to be bound by the terms set forth in-the OEM's license (other than those terms providing for access to and modification of source code) with Microsoft pursuant to this section.
(e) Microsoft may require that modified versions of Windows operating systems created by a particular OEM be installed only in the form in which the unmodified versions of that operating system are installed, but must permit the OEM to distribute any non-Microsoft software in any form. Microsoft may also require that OEMs, and any licensees pursuant to . 4(1)(d) above, provide their customers with end-user licenses for such modified versions of Windows operating systems in a form prescribed by Microsoft .that is consistent with this decree. Microsoft is not required-to grant OEMs any right to disclose source code for the original or any modified version of a Windows operating system except as provided in the preceding sentence and in subsection 4(h) below.
(f) Microsoft may require that an OEM that develops a modified version of a Windows operating system that boots up automatically into a non-Microsoft user interface to include an icon on the primary screen of that user interface that enables the end-user to return to the Windows desktop as designed by Microsoft.
(g) Microsoft shall make all source code for Windows operating systems available to OEMs that enter into source code licenses pursuant to this section beginning with the first alpha, beta, or other release of the operating system outside of Microsoft and shall supply complete updates to that source code at the time of all later releases and release candidates. Microsoft may require OEMs to base their modified versions of Windows operating systems on the commercially released versions of those operating systems and not on a beta release or a release candidate, provided that Microsoft supplies OEMs with the final code for such systems at least 180 days prior to the earlier of their scheduled release date or their release. Microsoft may prohibit OEMs from releasing any modified version of a Windows operating system prior to the earlier release of Microsoft's release of that operating system or 60 days after the scheduled release date.
(h) To facilitate creation of modified versions of Windows operating systems by OEMs, Microsoft shall provide OEMs with its internal build tools, source code archives, bug-tracking databases, custom compilers, test suites, and other development tools ordinarily used by software developers in modifying and testing modified source code for operating systems (subject to normal and customary restrictions on disclosure of such proprietary technology), as well as reasonable access to knowledgeable Microsoft support engineers familiar with the source code, whose time may be billed by Microsoft to OEMs at customary rates. Subject to customary and reasonable intellectual property rights (including customary and reasonable nondisclosure agreements executed by ISVs and their personnel exposed to Microsoft's source code), Microsoft must permit an OEM to work with one or more ISVs or other software developers (which may participate in modifying the source code) to facilitate the OEM's development of a modified version of a Windows operating system pursuant to . 4(1) of this decree.
(i) OEMs shall have the right to use the word "Windows" to designate any modified version of a Windows operating system created pursuant to this section and to state, when true, that the modified version runs applications that run on Microsoft Windows, provided that the OEM states clearly that such modified version has been modified by the OEM, and does not imply that Microsoft endorses the modifications.
(j) Microsoft shall have no obligation to provide product support to an OEM's customers for those aspects of a modified version of a Windows operating system created by the OEM that are due to the modification.
(a) The source code licenses granted pursuant to § 4(1) are perpetual, and the right to license modified operating systems created thereunder shall continue for an additional five years; and
(b) If the obligation set forth in § 4(2) to continue to license a predecessor operating system is triggered during the five-year period referred to in the preceding subsection, Microsoft shall continue to comply with that obligation with respect to that predecessor operating system for an additional two years, but § 4(2) shall have no further force or effect after the expiration of the two-year period.
(a) access during normal office hours to inspect and copy all books, ledgers, accounts, correspondence, memoranda, source code, and other documents and records in the possession, custody, or control of Microsoft (which may have counsel present) relating to any hinters contained in this decree;
(b) subject to the reasonable convenience of Microsoft and without restraint or interference from it, to interview officers, employees, or agents of Microsoft, who may have counsel present, regarding any matters contained in this decree;
(c) upon written request and on reasonable notice to Microsoft at its principal office, require Microsoft to submit written reports,nder oath if requested, with respect to any matters contained in this decree.
|

 U.S. Department
of Justice
U.S. Department
of Justice
